1. netsh
nesh
netsh [context] [subcontext] [command]
Here is a practical example
netsh interface ipv4 show config
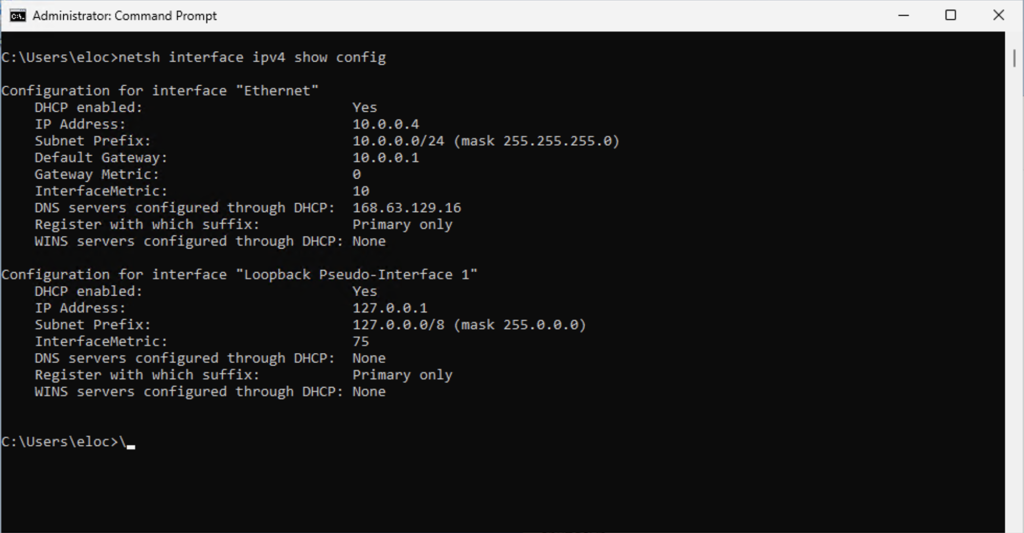
Now this is practically the same as ipconfig but netsh has a lot more use and functionality, for example.
- Network Configuration: You can use
netshto configure network interfaces, set IP addresses, configure DHCP, manage wireless networks, and more. - Firewall Configuration:
netshallows you to manage the built-in Windows Firewall. You can create rules, open ports, and configure firewall settings. - WLAN Management: If you’re on a laptop or desktop with wireless capabilities, you can use
netshto manage and connect to wireless networks. - Winsock Catalog Reset: This can be useful if you’re experiencing network issues. You can reset the Winsock catalog using
netshto reset the network stack to its default state. - HTTP Proxy Configuration: Configure proxy settings for HTTP and HTTPS traffic.
- IPSec Configuration: Configure Internet Protocol Security (IPSec) policies for secure communication.
- Routing Configuration: Configure routing tables and routing settings.
- Network Diagnostics:
netshprovides various commands to diagnose and troubleshoot network-related problems.
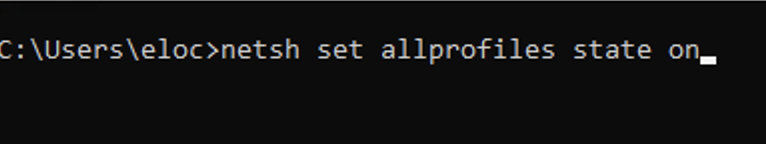
This command will turn on a firewall
=====================================================================================
2. ping
The ping command is a network utility used to test the reachability and responsiveness of a host or server on a network.
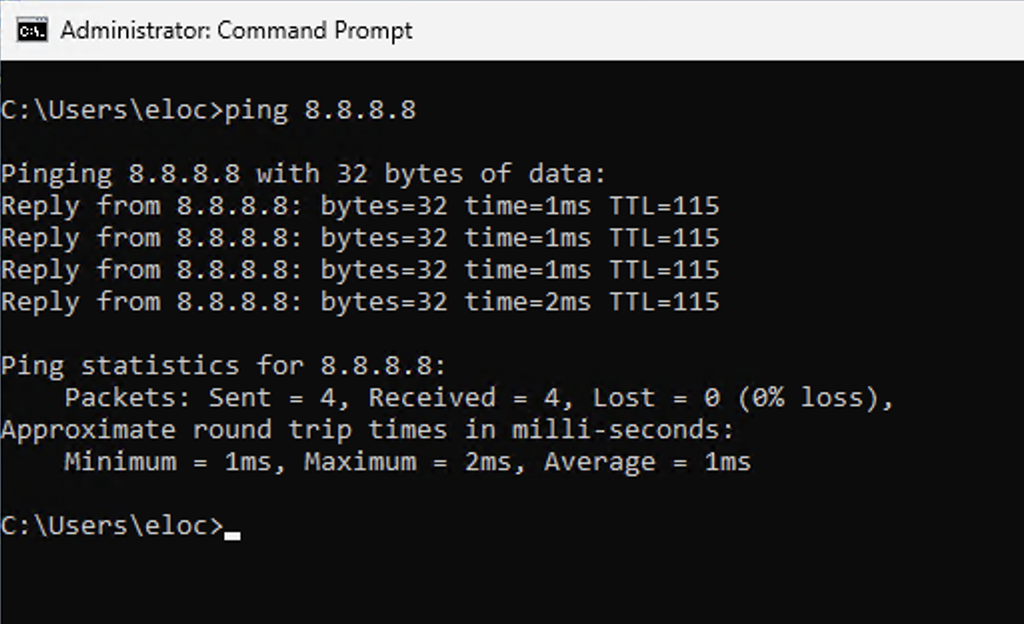
This command is used frequently when troubleshooting as it allows you to gather detail about how fast your and stable your connection is very rapidly. You can use this command to if a service is up and running, diagnosing network connectivity issues, and testing the stability and speed of your connection.
When you run the ping command, your computer sends a series of small data packets (ICMP Echo Request messages) to the destination address. The destination system receives these packets and, if properly configured, responds with ICMP Echo Reply messages.
Some common flags that are helpful to know are
-c count: Specifies the number of ping requests to send before stopping.-i interval: Specifies the time interval between sending ping requests.-t ttl: Sets the Time to Live (TTL) value for the packets, determining how many network hops they can pass through.-s packetsize: Specifies the size of the data packets being sent.-q: Quiet mode, which displays only summary information.
It’s important to note that some systems or firewalls might be configured to block ICMP traffic, which could affect the ability to send and receive ping requests. Additionally, while ping is a valuable tool for basic network diagnostics, it doesn’t provide a comprehensive view of network health, especially in complex networks. For more in-depth analysis, specialized network monitoring tools are often used.
=====================================================================================
3. tracert
The tracert command is the Windows equivalent of the traceroute command in Linux. Its primary purpose is to trace the route that packets take from your computer to a destination host or server on a network, helping you identify the network hops (intermediate devices) along the way and measure the response times. Often this is the command you will use if ping was not enough.
When you run the tracert command, your computer sends a series of ICMP (Internet Control Message Protocol) Echo Request packets to the destination address. These packets have gradually increasing Time to Live (TTL) values. The TTL value determines the number of network hops (routers) the packet can traverse before being discarded. As the packets traverse the network, routers decrement the TTL value until it reaches zero, at which point the packet is discarded and an ICMP Time Exceeded message is sent back to your computer. This tells your computer how many hops it takes to reach a destination and what those hops along the way are.
Some options are
-d: Preventstracertfrom performing DNS reverse lookups on IP addresses, which can speed up the trace.-h max_hops: Specifies the maximum number of hops (TTL) to reach the destination.-w timeout: Sets the timeout in milliseconds for waiting for a response from each router.-4or-6: Forcestracertto use IPv4 or IPv6, respectively.
One thing to remember is that certain Firewalls or Security Softwares may block the ICMP packets sent by tracert. If that happens your command will look like this.

=====================================================================================
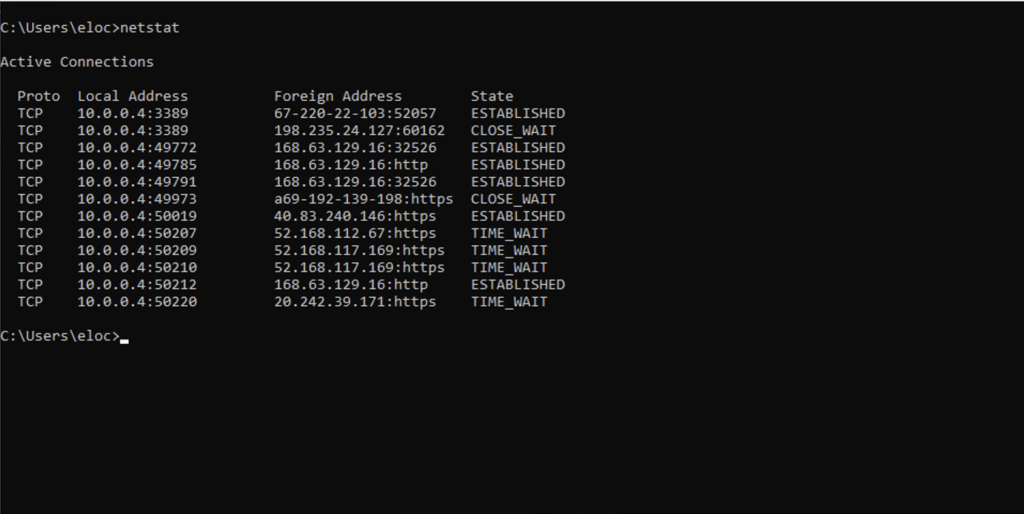
4. netstat
The netstat (network statistics) command is a networking utility available in various operating systems, including Windows and Unix-like systems. It provides information about network connections, routing tables, interface statistics, masquerade connections, and more. The primary purpose of the netstat command is to display and manage network-related information and statistics.
-t: Display TCP-related information.-n: Show numerical addresses instead of resolving hostnames.-c: Continuously refresh the display of active connections.-p: Show the process or application associated with each connection.-r: Display the routing table.-i: Display network interface statistics.-a: Display all listening and non-listening sockets.
=====================================================================================
5. route
The route command is used in various operating systems, including Windows and Linux, to view and manipulate the IP routing table. The routing table is a key component of the networking infrastructure that the operating system uses to determine the path that network packets should take to reach their destination. The route command allows you to view and modify this routing table.
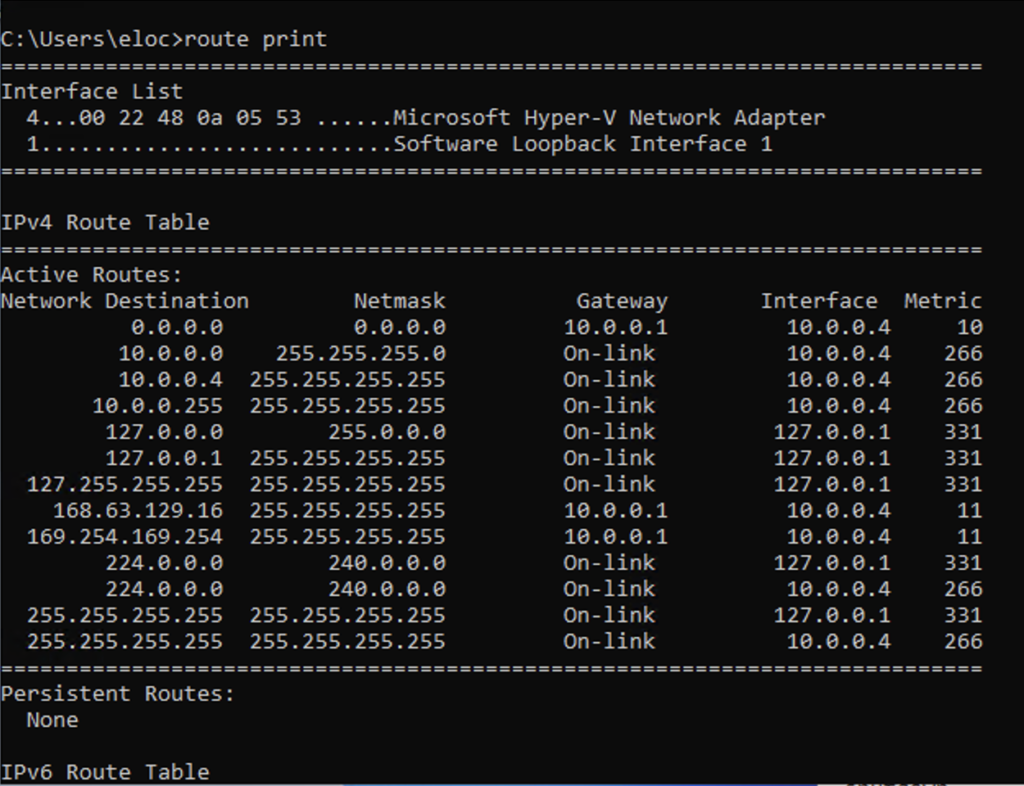
- Viewing the Routing Table: You can use the command route print to display the current routing table, including the network destination, subnet mask, gateway, interface, and metric.
- Adding a Route: You can use the route add command followed by the destination network, subnet mask, and gateway to add a new route to the routing table.
- Deleting a Route: You can use the route delete command to remove a specific route from the routing table.
- Modifying Metrics: The metric is used to determine the cost of a route. You can use the
route changecommand to modify the metric of an existing route.
=====================================================================================
6. shutdown /r /fw /f /t
This last command is really helpful to know. This will shutdown your computer then restart it in the BIOS so you don’t have to spam a certain button or keystroke.
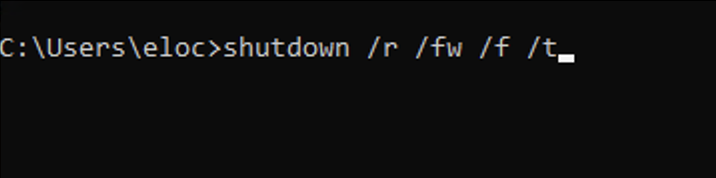
/r: Specifies that the computer should be restarted after shutting down./fw: This option is used to indicate that the restart should go into the firmware (system BIOS/UEFI) setup upon reboot. This can be useful if you need to make changes to the BIOS settings./f: Forces any running applications to close without warning. This is useful to ensure that all applications are closed properly before the shutdown or restart./t 0: Sets the delay time before initiating the shutdown or restart. In this case,0indicates no delay, meaning the shutdown or restart will happen immediately.
Please note that the effectiveness of the /fw option may depend on the computer’s BIOS/UEFI configuration and support for this feature. Additionally, using the /f option without giving applications a chance to close gracefully might result in data loss if there are unsaved changes in open applications.