.pptm is a Microsoft Powerpoint file extension, if you’re not running windows you can use the free and open source libreoffice to view the file. I downloaded mine using sudo apt.
The first command I did was strings to see if there was any hidden text in the file.

There is a hidden slide within the file so I opened it with libreoffice
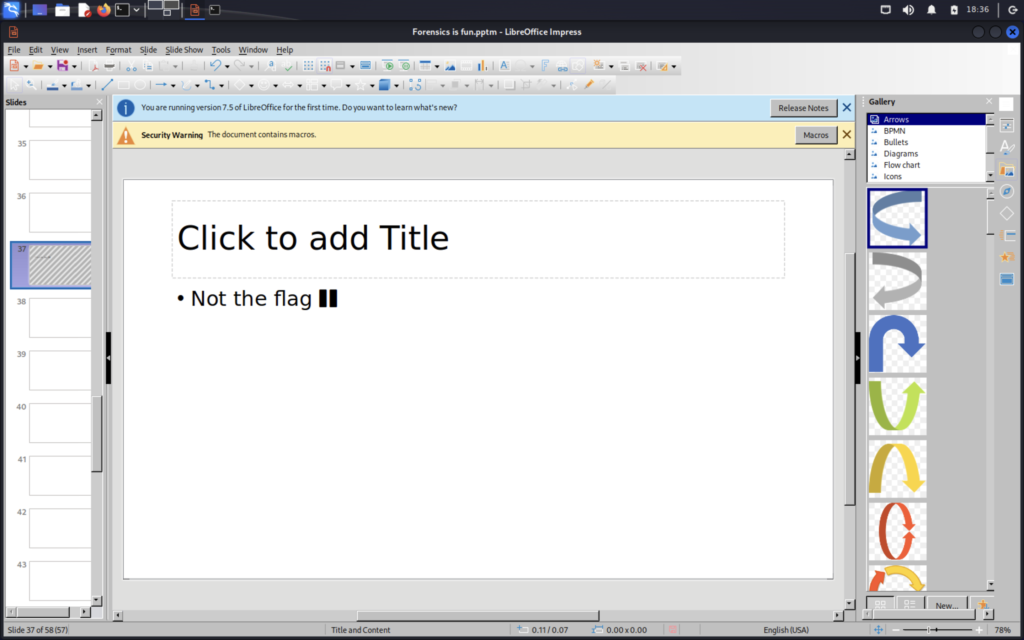
The hidden slide is denoted with the grayed out bars, but sadly it is just a rabbit hole. When I initially opened the file I received a security warning about macros, so let’s look there next.
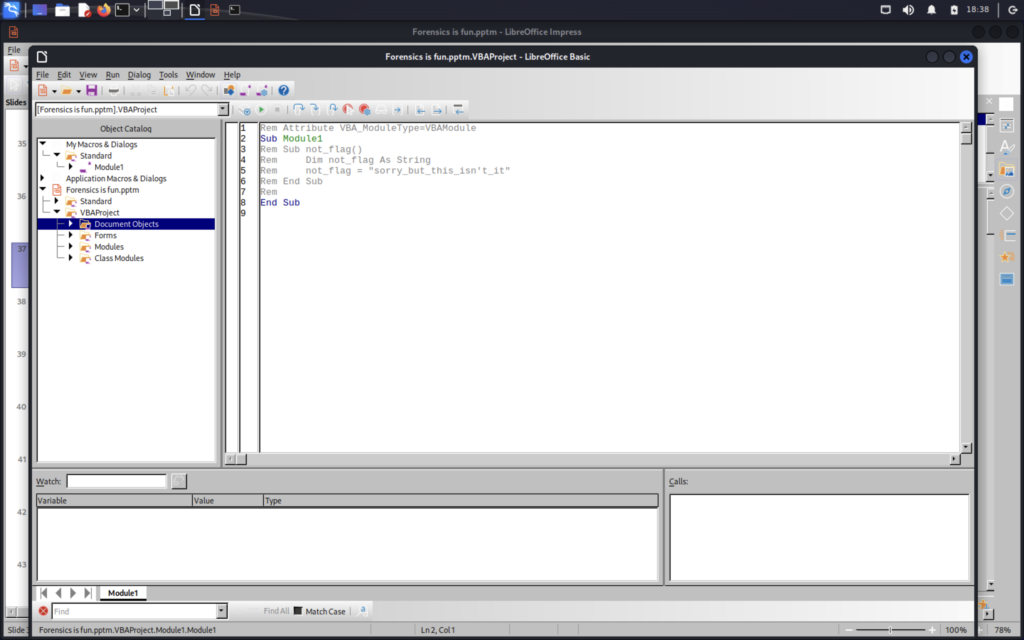
Another false flag. Next I decided to use binwalk to see if there were any files I could extract.
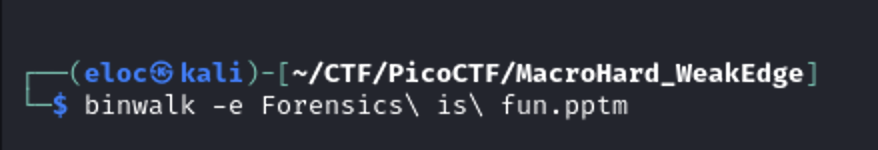
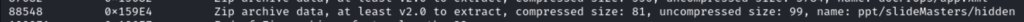
Another hidden file. Viewing the hidden file I found this cipher.
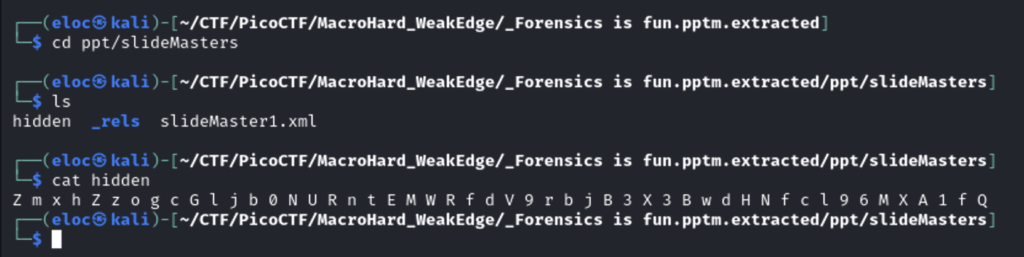
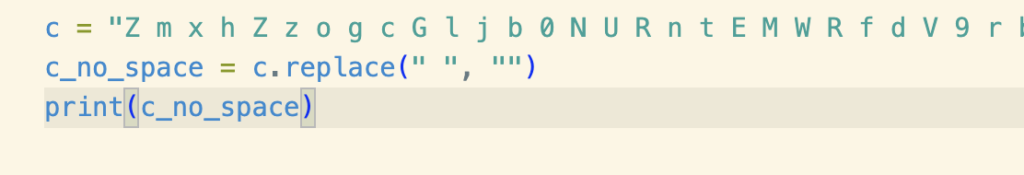
The spaces were making it difficult for online decoders to recognize so I quick removed them using python.
After that I was able to decode it using cyberchef. I could have used python, but cyberchef’s gui and auto recognition features make it much faster and efficient.
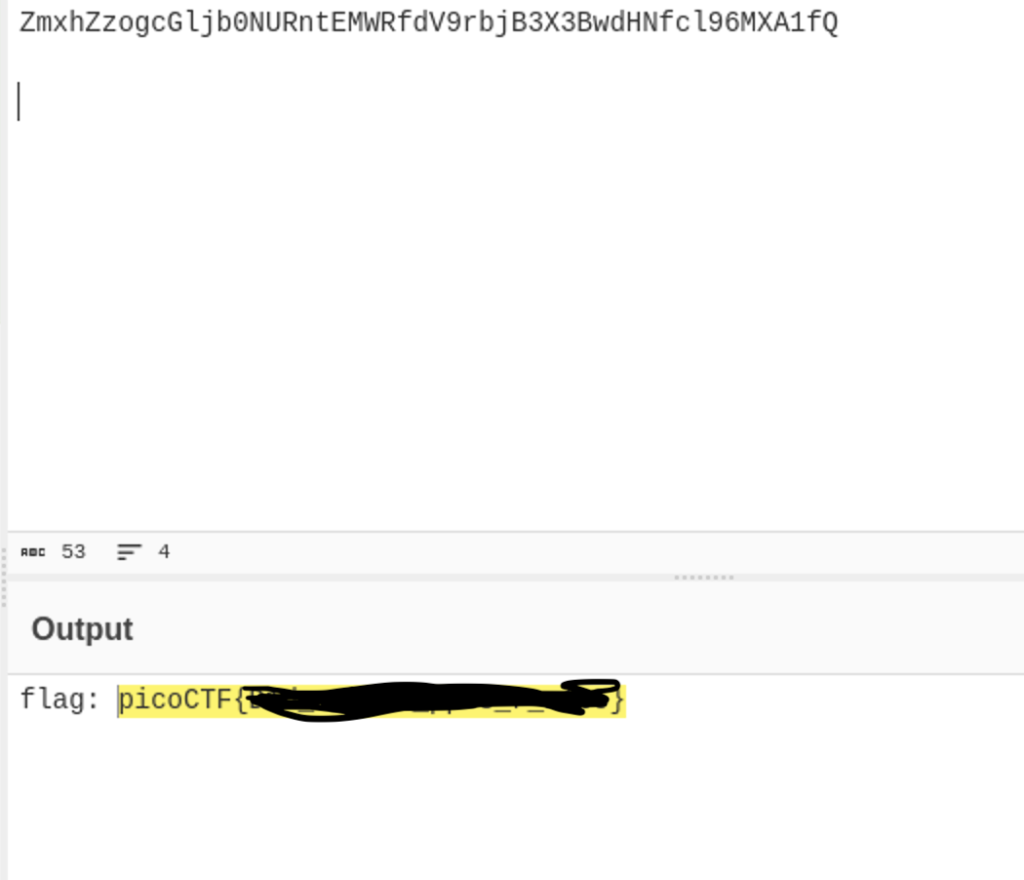
And there’s the flag!