The .pcapng file extension stands for Packet Capture Next Generation and it is a file type that stores network traffic. When data moves across a network it does so in “packets”. We can use a tool like Wireshark to analyze these packets and find the flag.
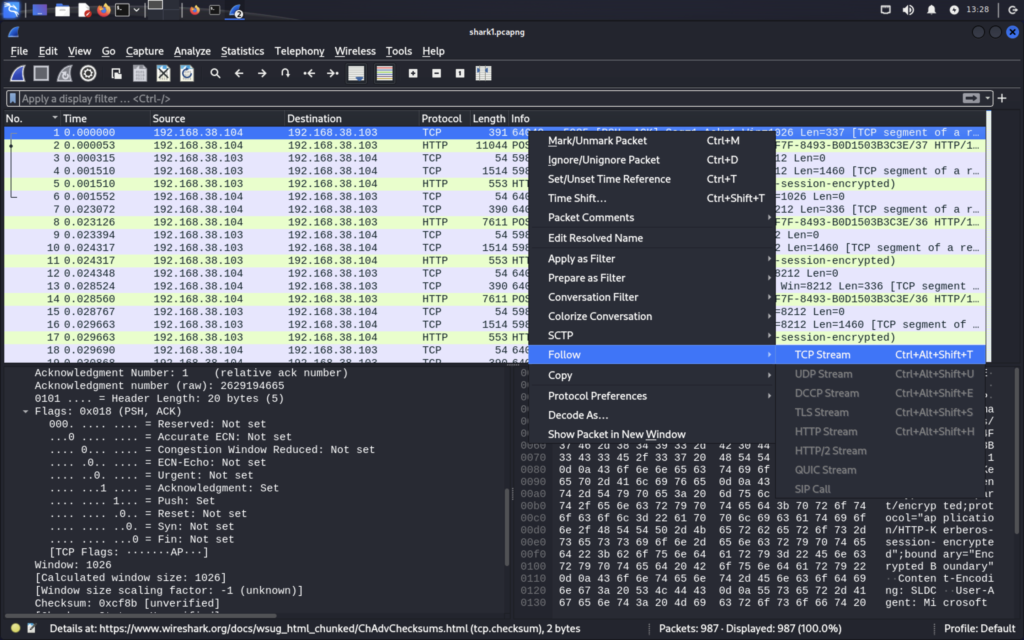
There’s hundreds of packet in this file so manually looking for the flag would be tedious. Certain packets will be related to each other and grouped together because they are part of the same session, in wireshark these are called streams. You can right click on any packet and press “Follow” then TCP Stream or any other applicable options. This will open a new window that will display all the stream. Right now I’m looking for anything that sets a packet apart from the rest of the file. You can toggle between different streams using the button in the bottom right. After looking for a little bit I found something interesting with stream 5.
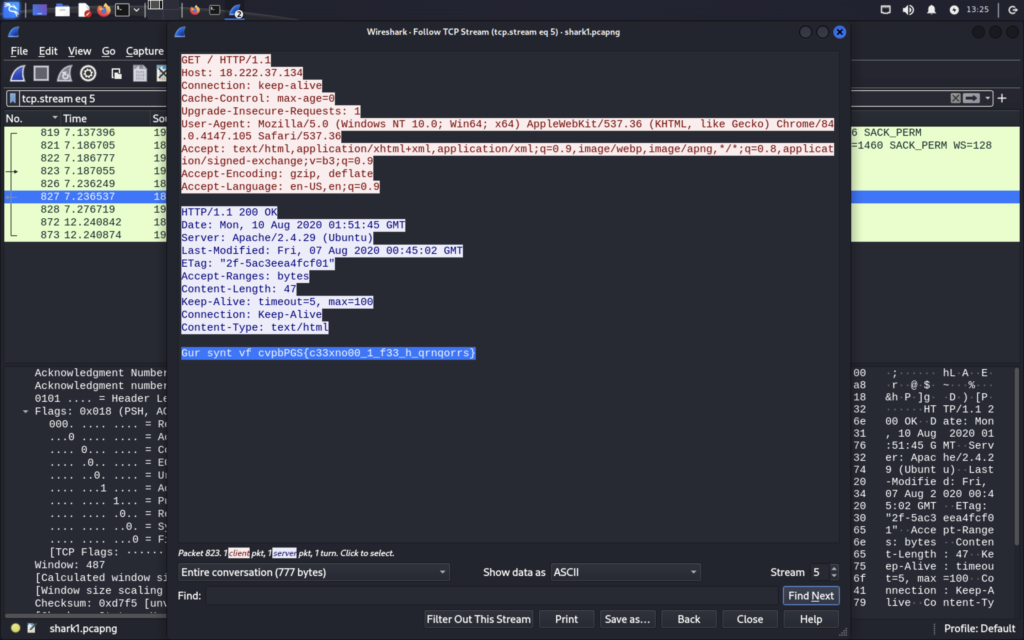
The other packets were all encrypted but stream 5 wasn’t. The content at the bottom appears to be rot13.
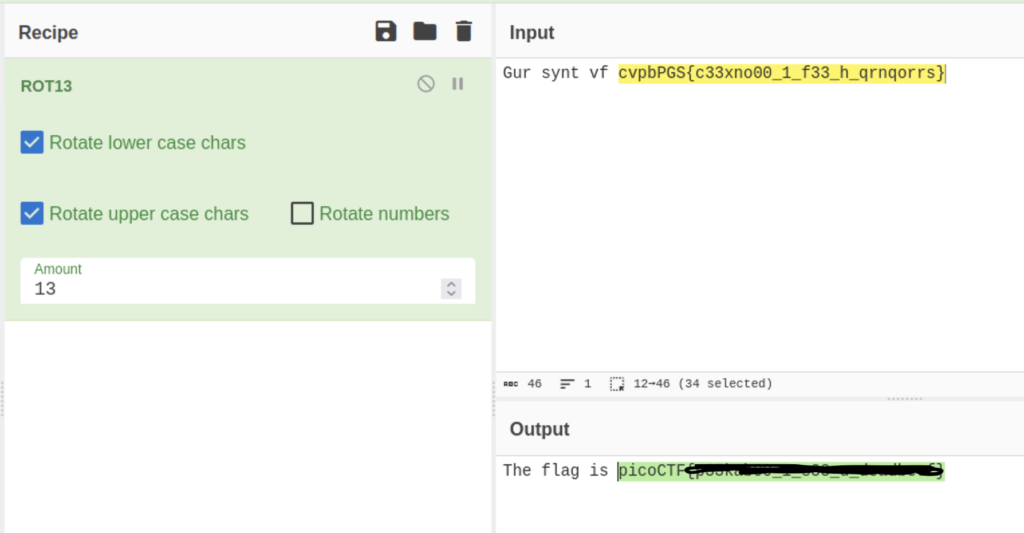
(cyberchef.io)
We found the flag!