PicoCTF is a capture the flag platform run by Carnegie Mellon University with the aim of providing a training ground for people interested in the world of cybersecurity. Carnegie Mellon has a great computer science program and they have some excellent hackers in their alumni as well. Pico CTF is a great starting point and today we will be walking through the first 3 levels.
Obedient Cat
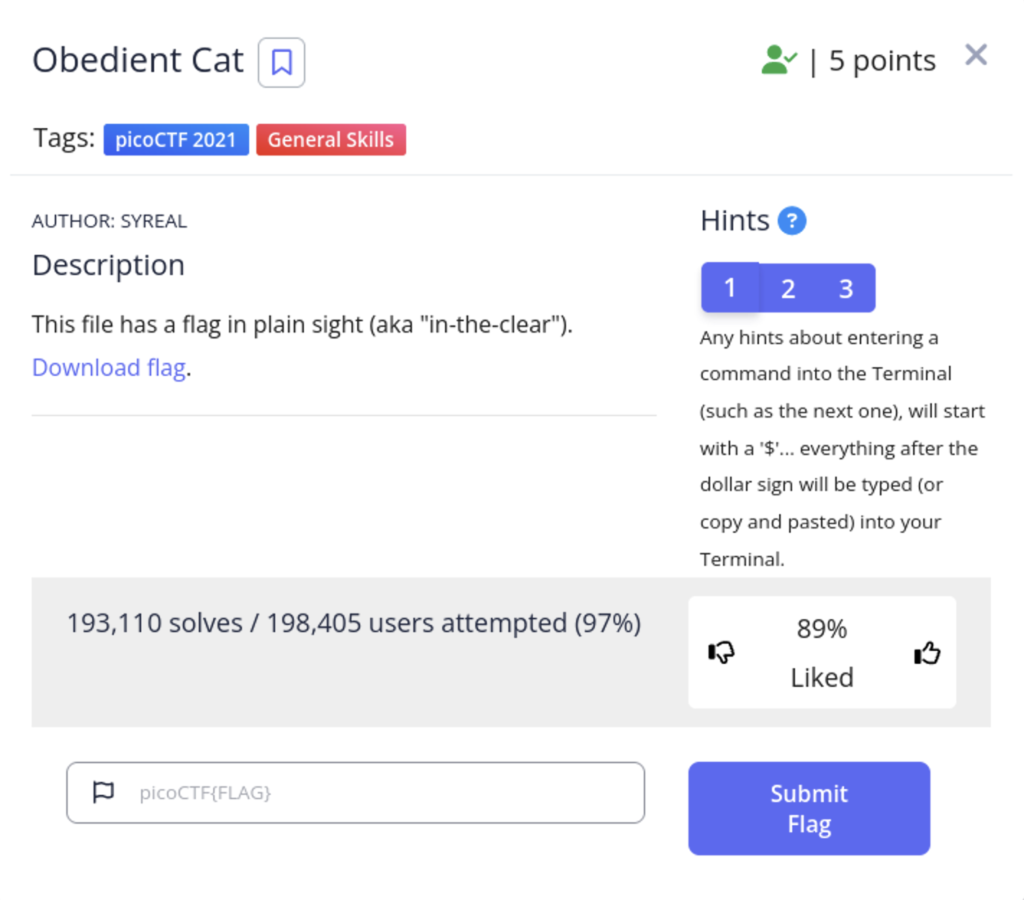
Command line skills are a must have if you’re interested in cybersecurity. This first level is really just a chance to practice making directories and viewing files from the command line. I recommend creating a separate directory dedicated to your CTFs to keep things organized. If this is your first time using the command line this can be very confusing. Here are my commands I used to solve this challenge.
Note: I am currently running Kali Linux. These commands will work for most other Linux distros and MacOS as well. For windows you would use different commands.
Here is an explanation of what the commands do
- 192 – Creates a directory called “PicoCTF” to keep things organized
- 193 – cd stands for “change directory” this moves to the directory we just created
- 194 – ls is short for list. The directory where I keep my downloads is one step up from my current directory. “../” signals that I wish to move one directory up from my current one. I entered this command to see the name of the file we downloaded which contains the flag
- 195 – mv is the command used to move files around the linux the files system. Now that I know the name, I type out the path to the file ( where it is located on my local machine) and move it to my current directory which is dented using a “.”
- 196/197/198 – next I make a directory for this challenge and move the flag to that directory then cd into that directory.
- 199 -cat is command used view the contents of a file in text on terminal screen. After this command you will have the flag
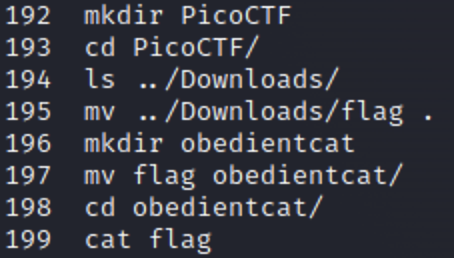
Mod 26
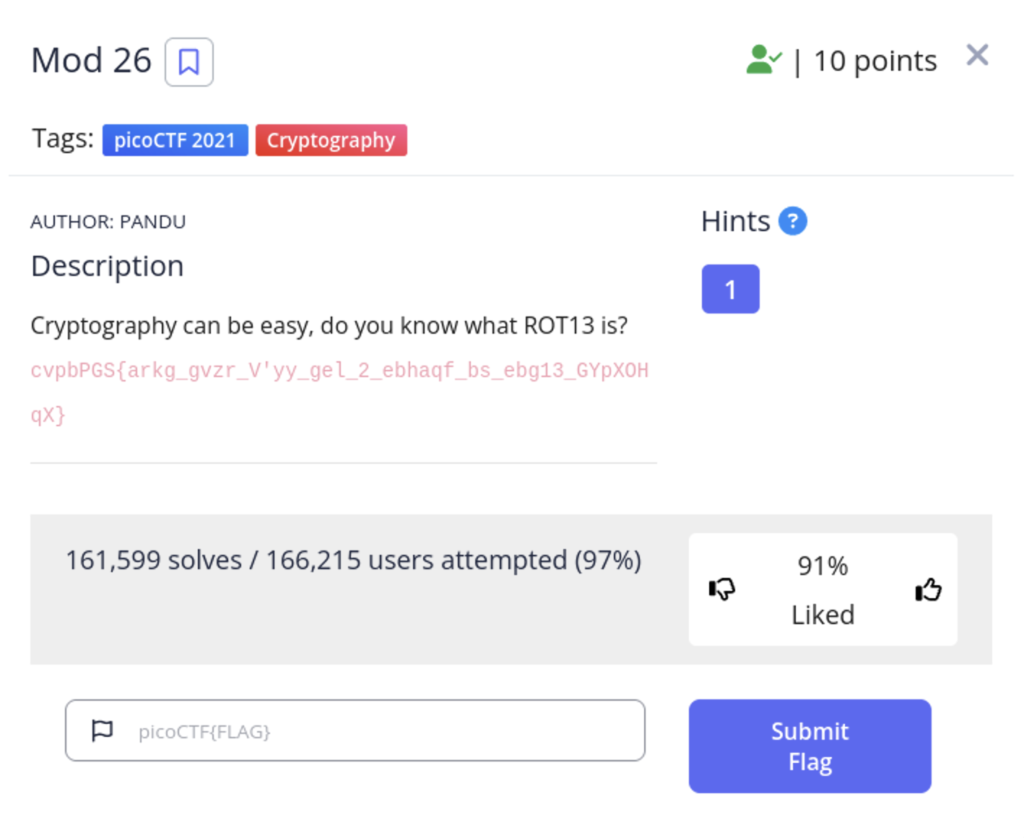
ROT13 is a basic cipher that you will encounter a lot in CTFs. It works by shifting every character in the text 13 places forward in the alphabet. Because the alphabet is 26 characters (in English) this cipher is symmetric meaning decrypting is the same process as encrypting. There are dozens of online tools to help you with this.
Python Wrangling
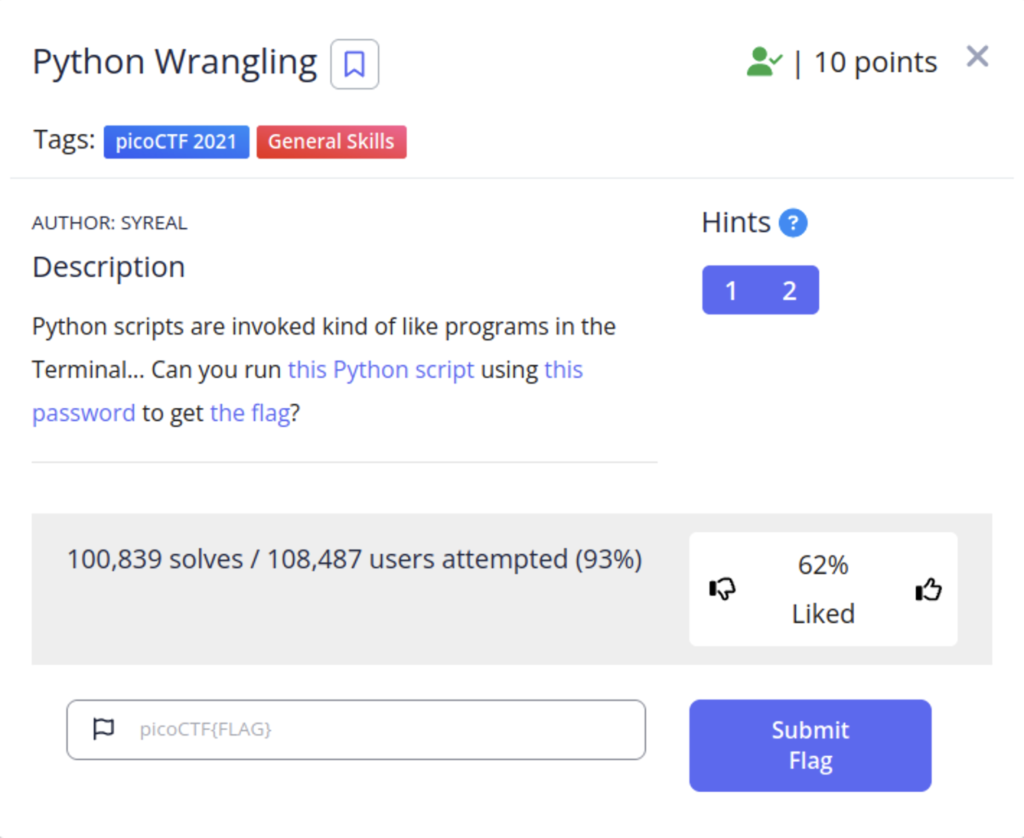
This next challenge teaches you how to run python scripts from the command line. For this task we need to download 3 files; the script, the password, and the flag. Once you have those files create a directory for them and move them all to said directory. Next we need to make a slight adjustment to the script.
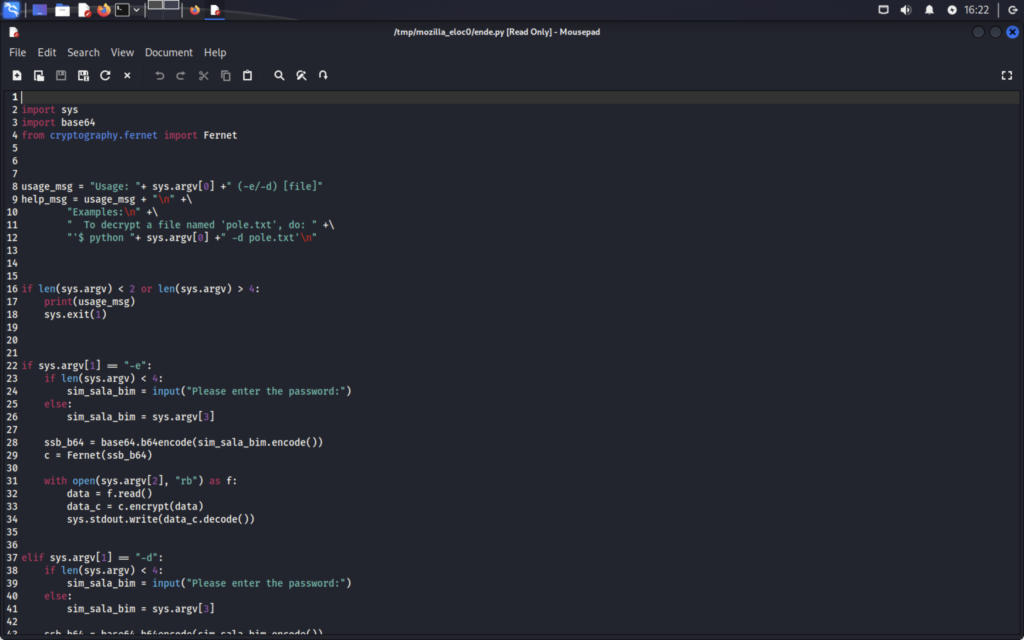
This how the script first looks to us when we download it. In order for a script to run in the terminal we need to enter a shebang. A shebang is a string of text we enter at the top of the file to tell our computer what language this should be interpreted as. It looks like this
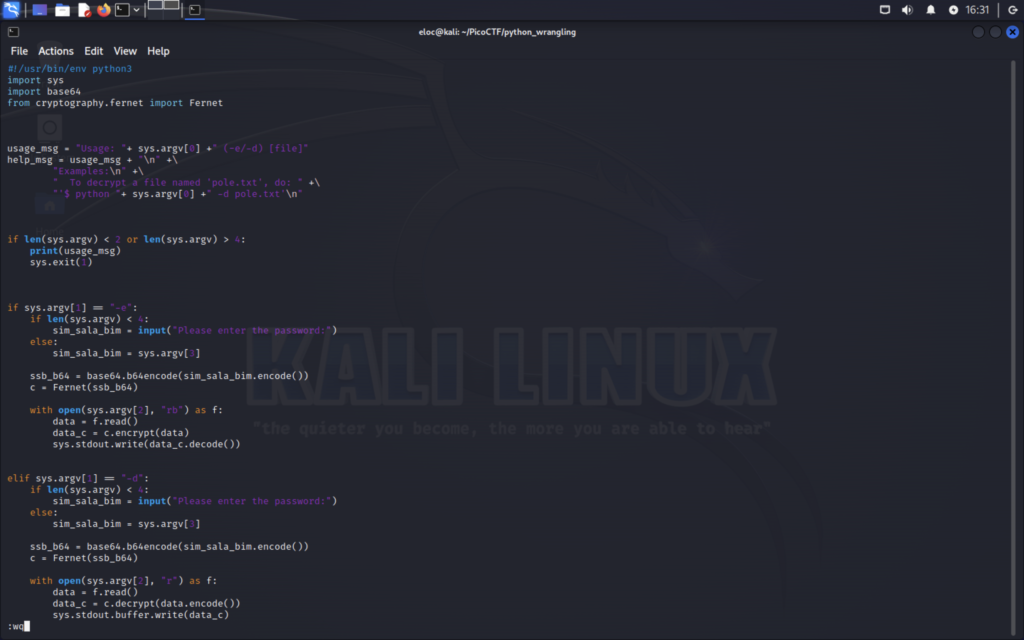
Next you need to make the script executable so we can run it. This can be done using the command ” chmod +x [filename]. Upon reading the script we can see how to use it. The syntax is “script name argument filename”. After that we will be prompted for the password we downloaded and then the flag will be shown to us.
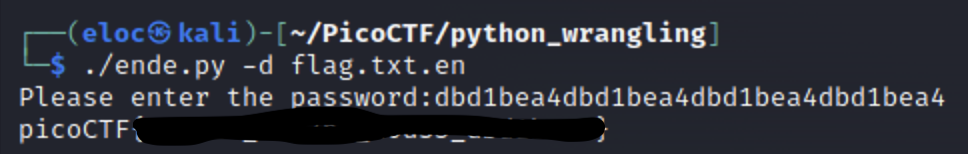
Note: When we run a script from the command line we need to enter the full path. One shortcut for this is using “./”. Since “.” is shorthand for our current working directory we can use this instead of typing the full path every time, for example ” /user/home/directory/script”. Alternatively you could use the command “python[version number]” instead. i.e python3 ende.py -d flag.txt.en