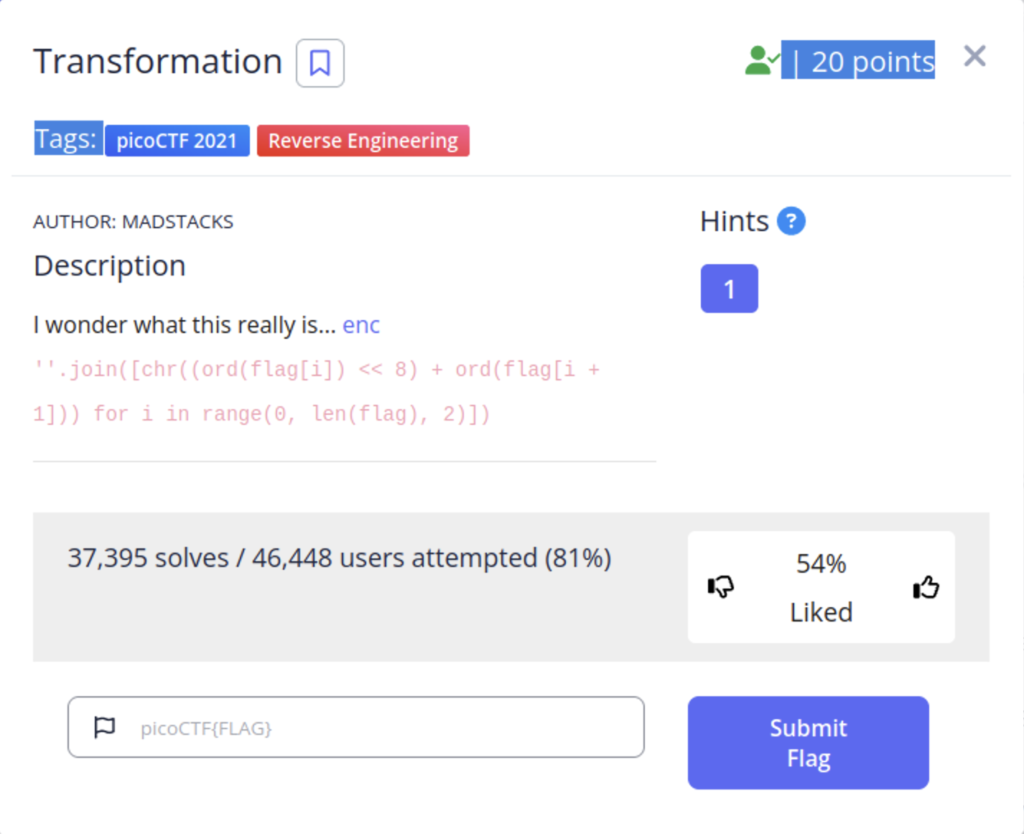
This challenge is a reverse engineering challenge. We have been given a file called enc that contains a string of characters. We have also been given a snippet of code that shows how the characters were encoded. To solve this challenge we will have to reverse the process.
First let’s break down the code

- ”.join – the code we are looking at is placing the encoded characters into a list. if you were to print the encoding without ”.join your results would look similar to [“a”, “b”, “c”]. The purpose of this piece of code is to join the items with no space or characters between them.
- chr() – is a function that converts decimal and hexadecimal into it’s assigned ascii character
- ord() – does the inverse of chr(). Converting ascii characters to a number
- << 8 – this is a bitwise shifter. It is a mathematical operand that shifts an integer 8 spaces to the left in binary. Which is the same as multiplying by 256.
- for i in range(0, len(flag), 2)- this section of code pairs up the characters in the original flag into groups of two.
The snippet of code takes characters in two at a time and multiplies the value of the ord() function by 256 for the first one and adds the value of the second ord() . Essentially creating a hexadecimal number. Since we have the encoded text we can calculate the hex values of the characters. split them at the octet then convert them back into ascii characters.
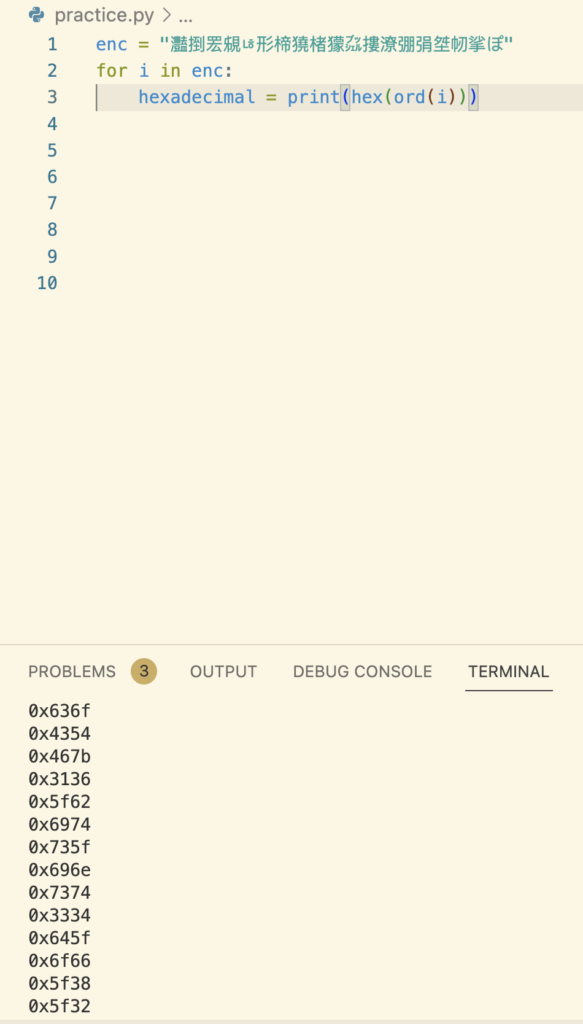
First we define our string. Next we create a loop that will iterate through each character of the string and first generate the numerical value with ord() the convert that to hexadecimal with hex(). When we convert the text though we will need to get rid of the “0x”. We can do that with python by adding the following.
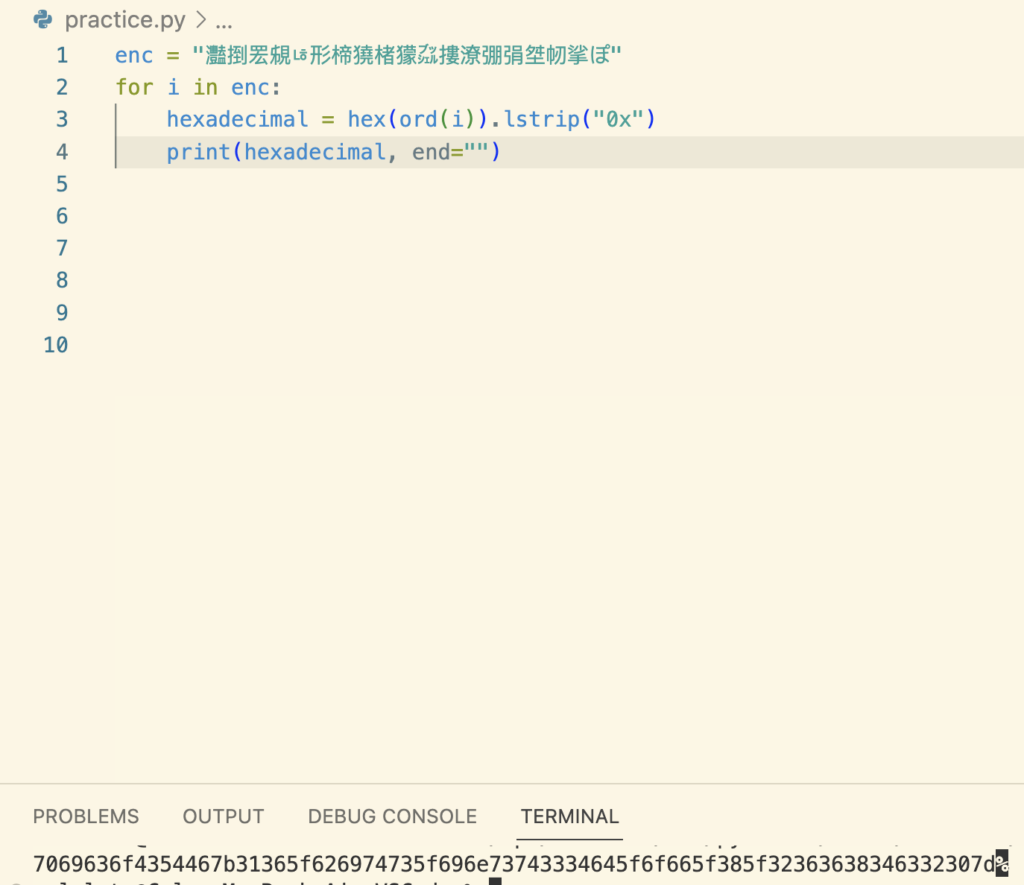
Now let’s use an online tool to convert back into characters

Now we hav our flag 🙂