Steganography is the practice of hiding secret messages in non secret forms of media. For example hiding a secret text in a image or sound file. But why would you want to use steganography? Perhaps you live in a country that censors free speech, you’re an international spy, or you’re just plain paranoid. Either way steganography is fun and there are many tools to do it. One of which is steghide.
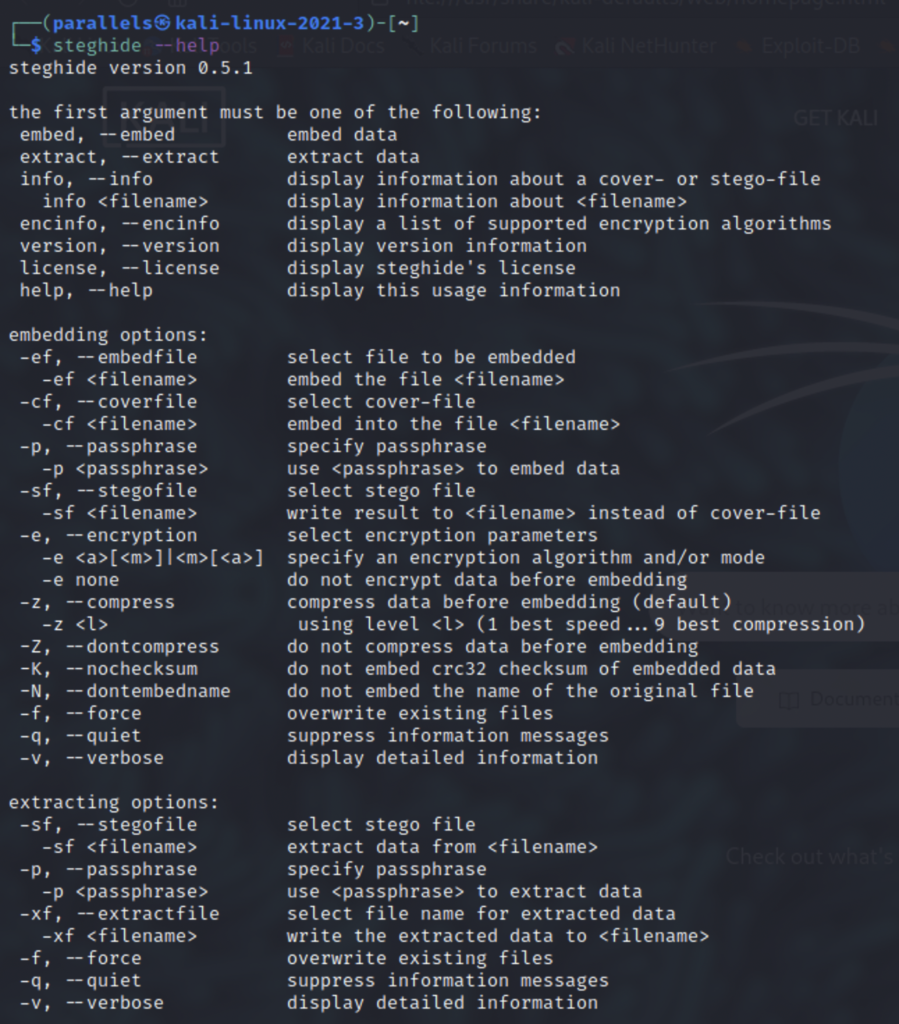
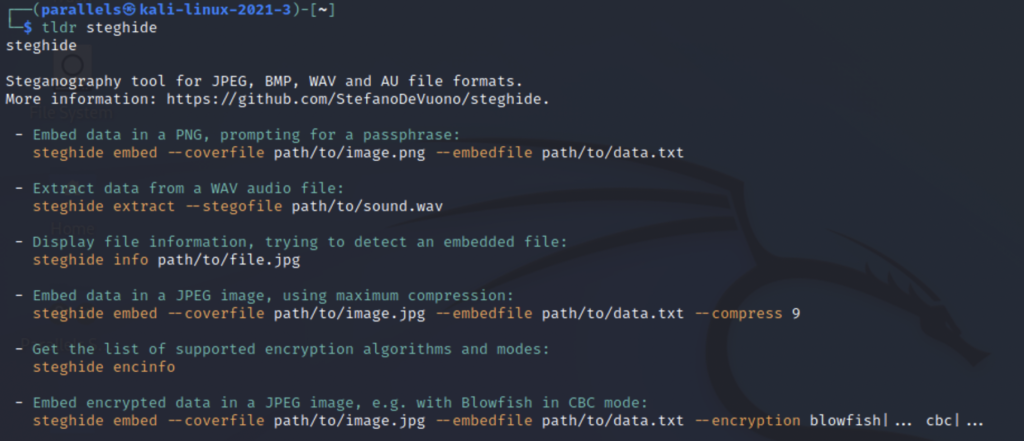
Steghide is already in the Kali Linux repository so you can install it with sudo apt install steghide. After installing it go ahead and take a look at the help menu. There’s not too many flags but if you want to see some examples take a look at the tldr.
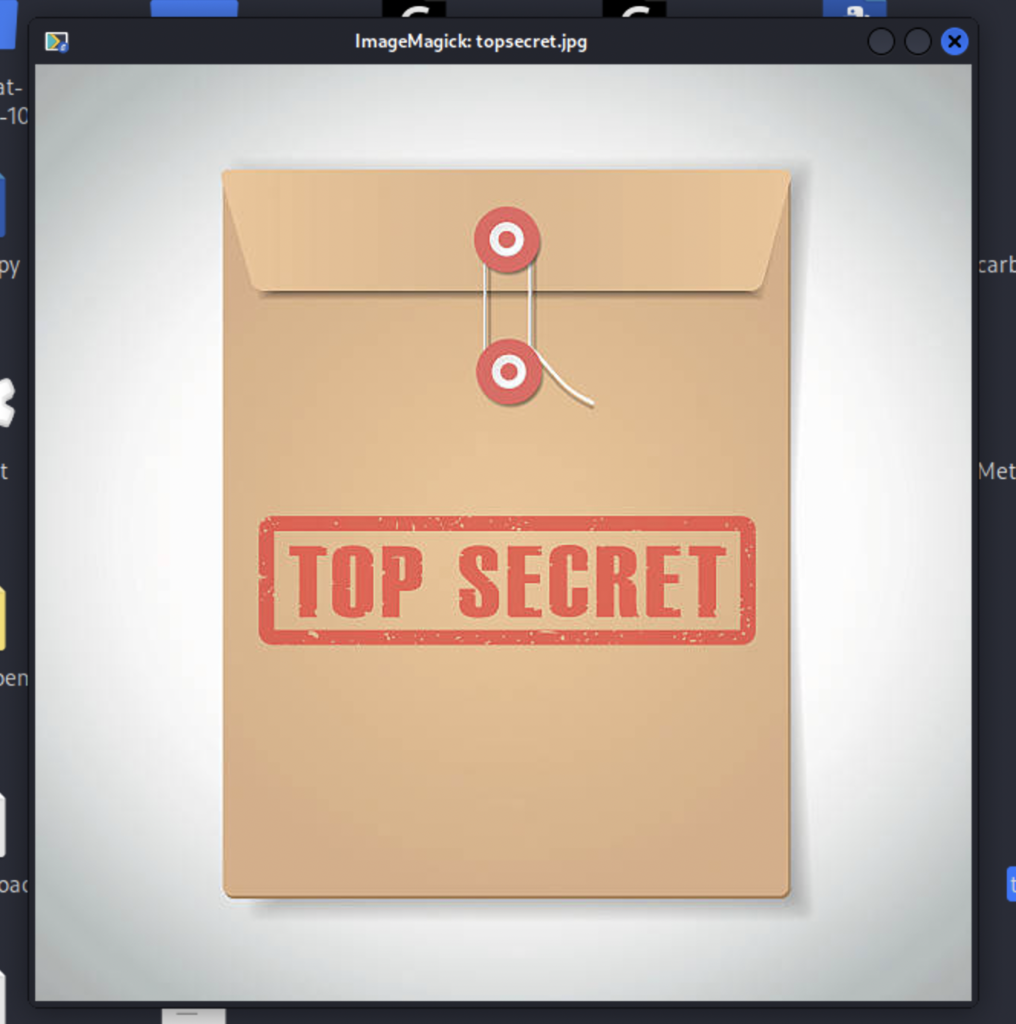
First we will embed data into a file. For this example I have chosen an image of a top secret folder which we will embed a text message into.
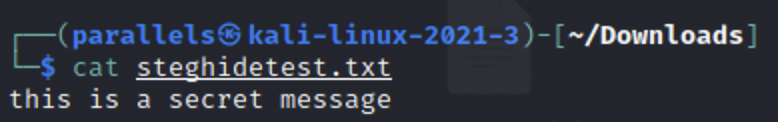
Next, we will choose a text file to be embed. I wrote a text file with a simple message for an example.
Now we need to embed steghidetest.txt into top-secret.jpg.
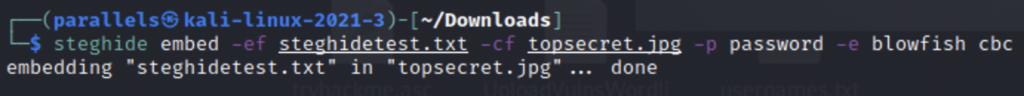
First we need to specify that we want to embed a file, then we can put in the details. -ef denotes the file we wish to embed, this is the file that contains the secret message. After that we choose the cover file which we want to embed into using -cf. Then we can set a password using -p and an encryption type with -e. For demonstration purposes I chose password as my password, but obviously this should never bee your password. If you’re curious about what encryption types are available with steghide you can run steghide encinfo.
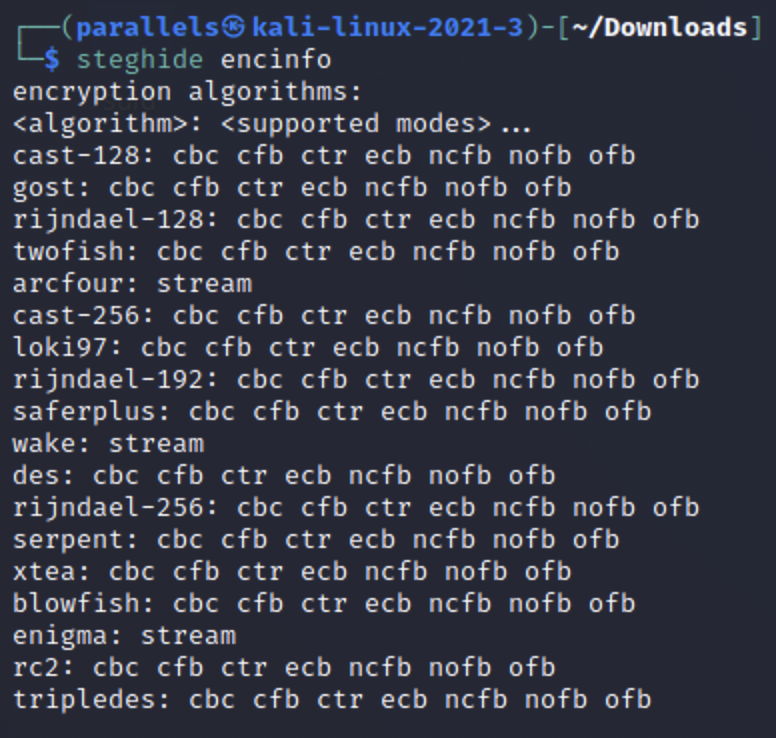
For our example I chose blowfish because it is robust, common and safe encryption algorithm (at the time of this blog post). Don’t use DES, it is a deprecated encryption standard that can be easily cracked by today’s technology. We won’t go into detail about all the different modes you see for each encryption type. Just know that cbc is block ciphering and works well. After that we are ready to embed and you can hit enter.
As you can see our folder looks the same and you wouldn’t suspect anything had been done to the image. The one clue you might find is the file size would be larger (though with small text files this difference would be negligible). If you are trying to put a much larger text file into a smaller image file you may distort the image because the pixels are actually changing in order to write the data to it. You could circumvent this by compressing the embedded file or maybe switching to a large audio file so you have more data to write to.
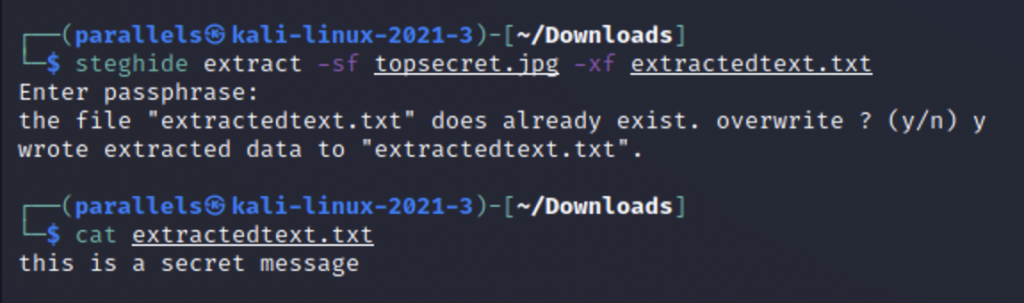
Now let’s try to extract our secret text to see if it worked. We first switch to the extract mode and then enter the file we wish to check for steganography with -sf. After that we can write the extracted data to a file using -xf . We will be prompted for the password and after entering it the data will be giving to us unencrypted. But what if we didn’t know the password and wanted to access the data? If the password is weak then it is possible to brute force it.
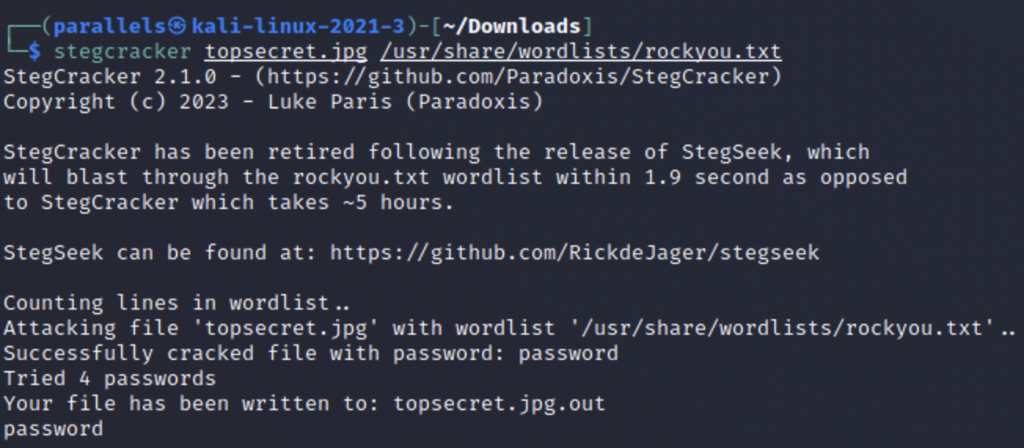
We can use a tool called stegcracker that is very simple and easy to use. We simply enter the file we wish to crack and then feed a wordlist to stegcracker and it launches a brute force attack. In this case since I chose such a weak password it was cracked on the fourth attempt but wordlists like rocky.txt contain millions of passwords and can tear through the lists very quickly.