This will be a simple walkthrough to demonstrate the fundamentals of hash cracking using a couple different tools. But first we have to understand what a hash is and how do we crack it?
Hashes vs. Encryption
Encryption is converting data to cipher text so that it may be transported or stored securely without disclosing any of the data or jeopardizing the integrity of it. When you encrypt data you will one day decrypt it so that you can view the data and use it in it’s original form. Hashes however are a one way trip.Once you hash it you can not reverse the algorithm to obtain the original input.
The output of a hashing algorithm is called a message digest. These are fixed in length regardless of the input, so if I only enter the letter o or the entire contents of the wikipedia page for MD5, the message digest will be the same fixed length.
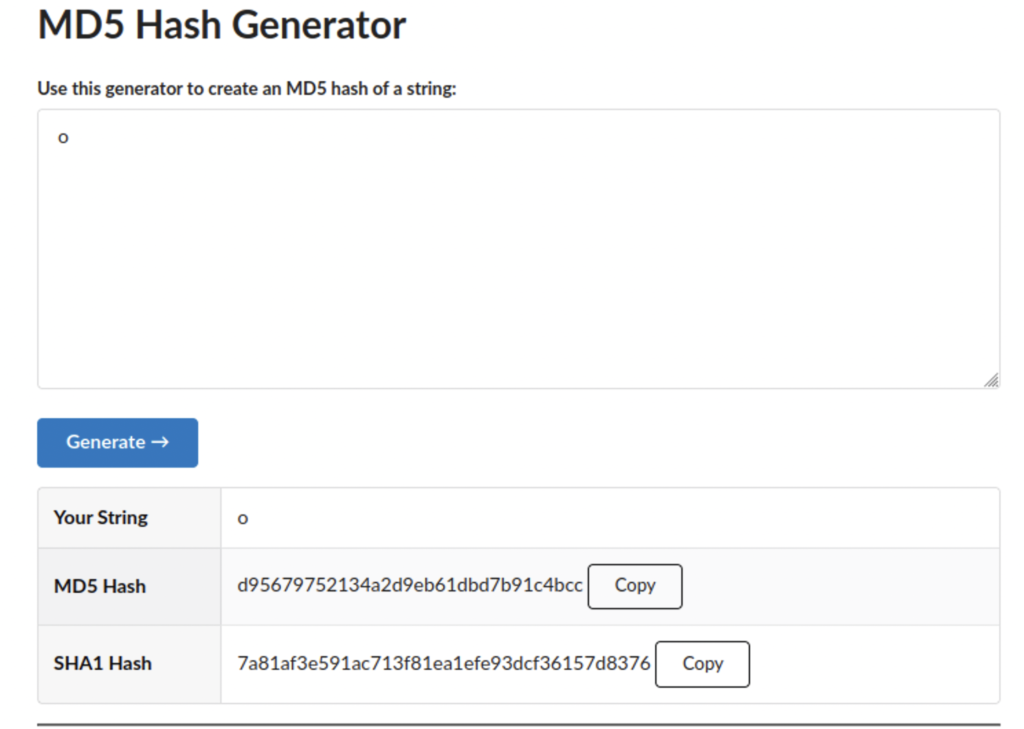

So why use a hashes? Hashes can serve many functions and are especially useful for storing passwords. If companies stored passwords in clear text they might as well just give them away to threat actors and if they encrypted them it would be too easy to reverse the encryption process, so companies store passwords as a hash.
General Overview of How Passwords Work
When you set up your password with a website that website takes your password and calculates the hash and then stores it in a database. Whenever you log in again the same calculation is performed to see if the hash matches the one in the database. Entering the hash itself wouldn’t work either.
How Are They Vulnerable?
While you can’t reverse a hash, if you know how the hash was calculated you can perform the same function and try to recreate the hash by guessing passwords till you get a match. It sounds like you might be more likely to win the lottery and be struck by lightning on the same day. But there are tools to make this process much faster and many people use weak passwords which makes them vulnerable.
John The Ripper
This tool is widely known and a good one to be familiar with especially if you like doing CTFs. It’s already in the Kali repository and there is plenty of documentation online about how to download it. This tool essentially performs the calculations for us and presents us with the original text provided we enter the correct syntax.
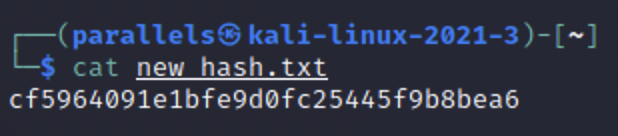
This is the hash we will be working with today. You could just plug the text file straight into the tool, but you will be waiting a very long time and there are more efficient ways of cracking it.
We could stare at this screen for hours before anything happens. So we need to find out what kind of hashing algorithm was used to create the hash, so that John is not blindly guessing in any algorithm it can think of.
There are plenty fo tools that can tell you what algorithm a hash may be such as hash-id.py. A CLI executable written in python.
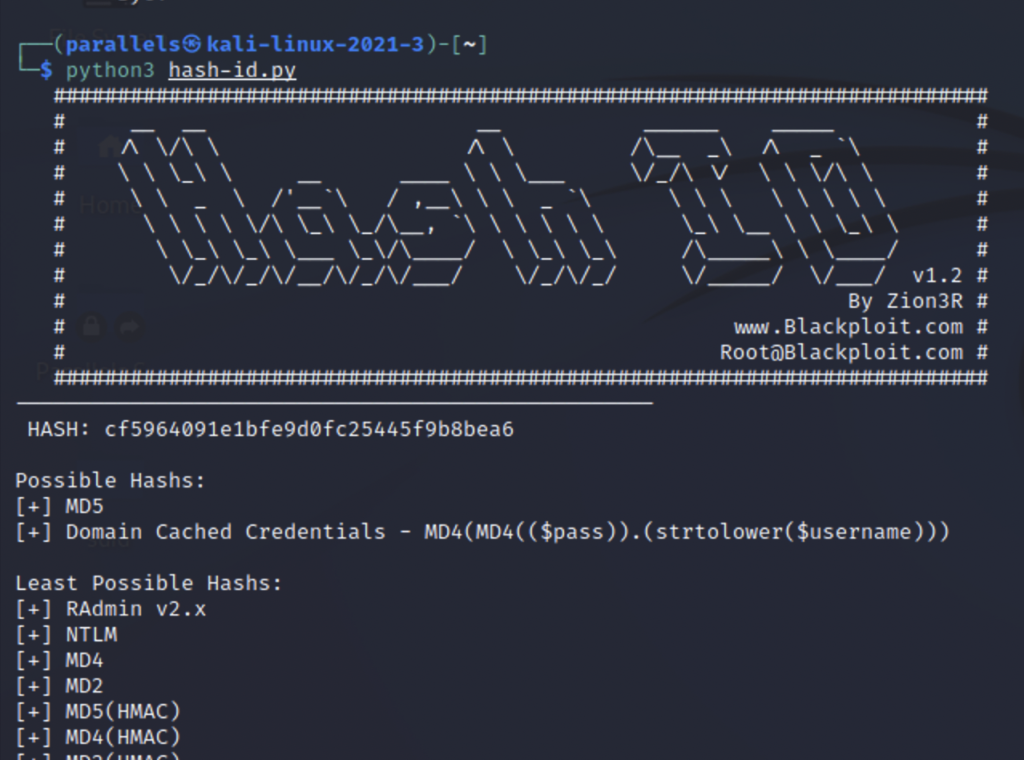
If you don’t want to download this you could also use a website like https://www.tunnelsup.com/hash-analyzer/
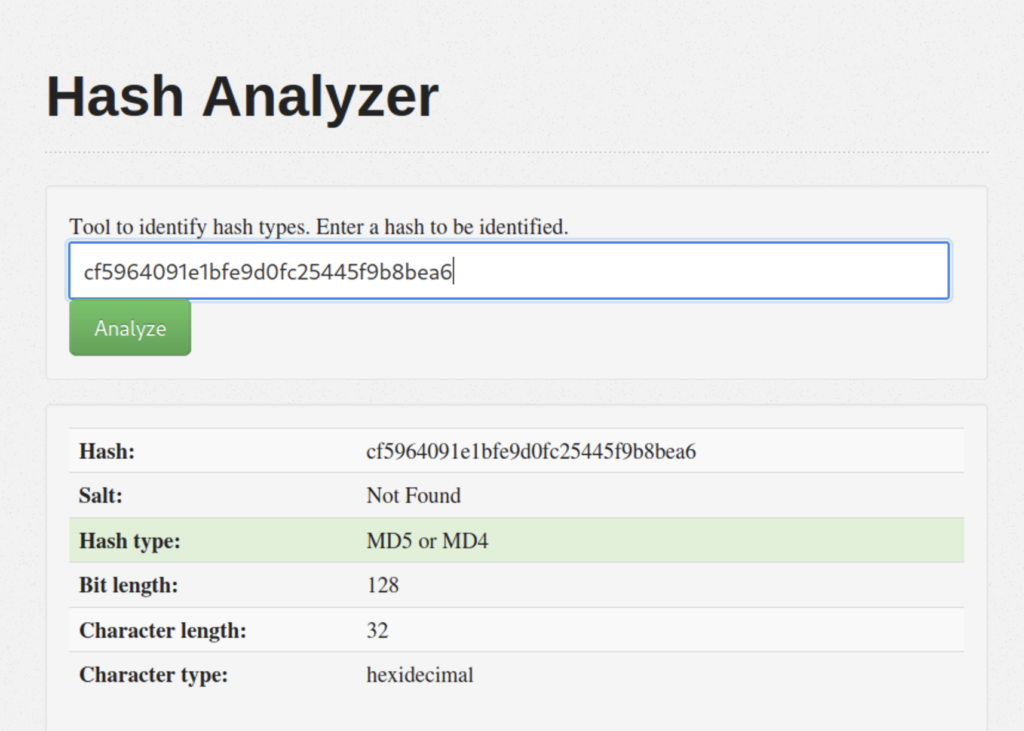
Both tools have told us that we are probably working with MD5. Now we need to to tell John that it’s MD5 but how do we do that? We can see what formats are supported by using john –list=formats.
That’s a lot to look at so let’s use grep to make it easier.
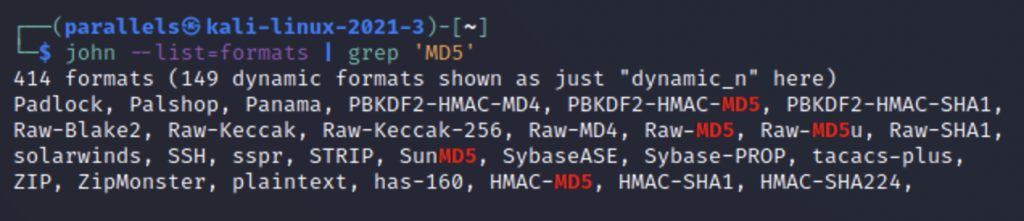
We can see that there are several different formats for MD5 but let’s use Raw-MD5 first. The second thing we need is a wordlist of passwords for John to guess with. I will be using rocky.txt.
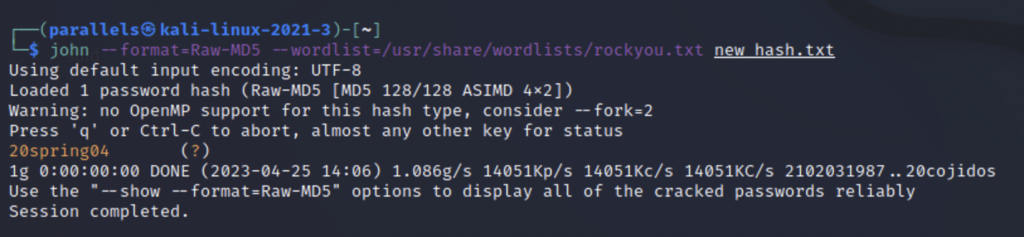
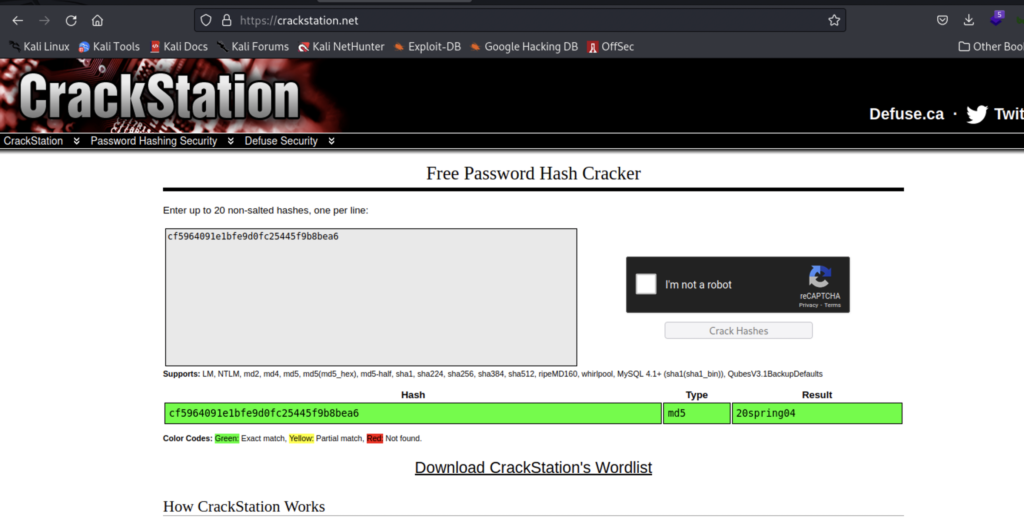
The information we need for the command to run is the format, wordlist, and text file containing our hash. After a couple seconds the hash is cracked and we see that the password is 20spring04. If you don’t like using the command line you could use something like crackstation.net. But you have limited functionality with that tool.
How To Protect Yourself
This demonstration was for educational purposes, in order to showcase some of the technology behind how our passwords work and how bad actors can steal them. But if hashing isn’t bullet proof then what can we do? The biggest thing and perhaps the most important thing that everyone overlooks is using better passwords and not reusing them. The wordlist in todays demonstration contains nearly 15 million common passwords and there are more out there just like it. Use long and complex passwords and use a different one for every site. If this sounds like a hassle there are tools out there that can manage your passwords for you and even generate them. Making them so complex that even todays super computers couldn’t guess them. Additionally criminals can be lazy too. So you don’t need to have the worlds best password, just better than the person using ‘123456’.