One Time Pad Encryption Crash Course
OTP(One Time Pad) is strong encryption algorithm that utilizes the XOR mathematical process to encrypt text. XOR(Exclusivey-OR) is a mathematical function where two strings of binary are compared to each other to create a new string of binary. If they match, like 1 to 1 or 0 to 0, then a 0 is placed but if they don’t match then a 1 is placed.
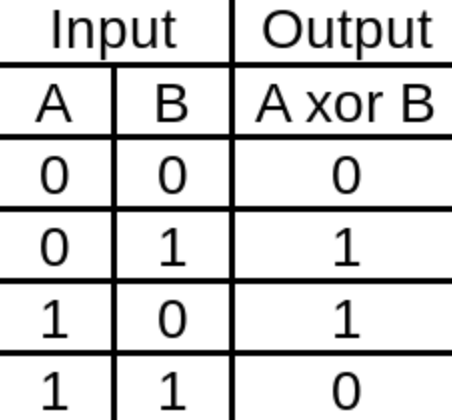
First you take a message and convert it to binary then you take a binary key of the same length and you -perform the XOR operation with the two. That is how your perform OTP encryption. OTP is secure so long as the same key is not used multiple times otherwise you can utilize the xor operation reverse the encryption.
The Script
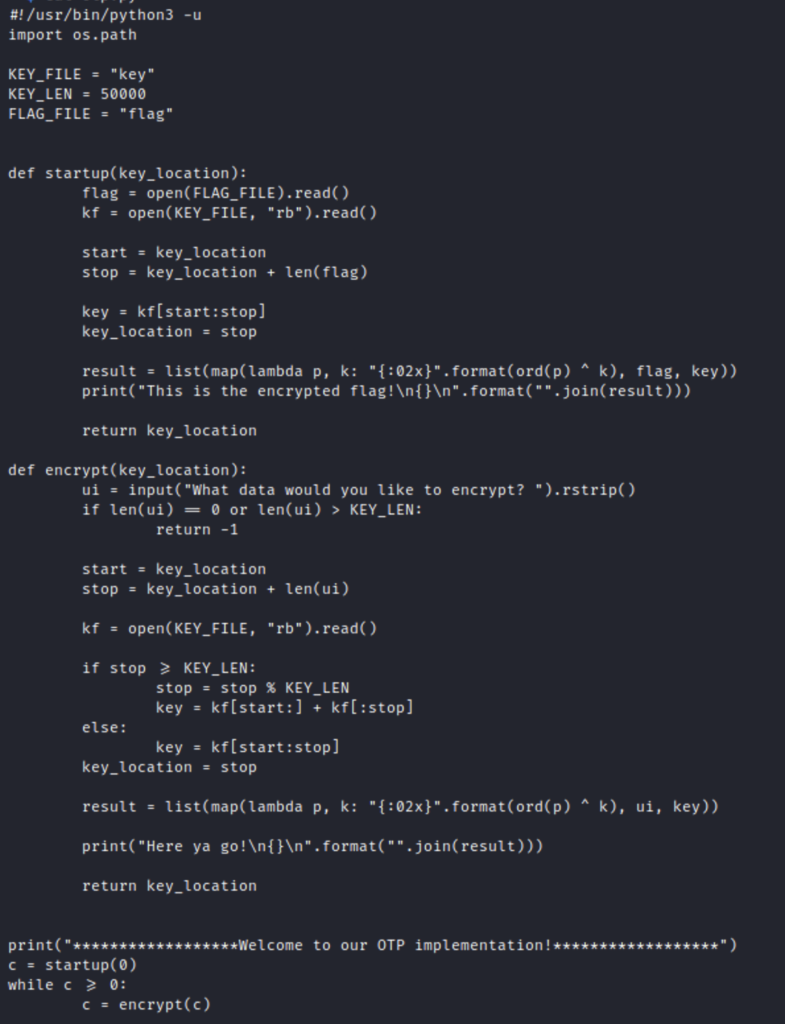
This is the script that came attached with the challenge. It looks intimidating but you only need to understand the basic concept of OTP to solve this challenge. The majority of the lines are for executing the XOR process discussed above. Let’s also use the netcat command given to us in the challenge.

We are given a version of the flag then asked if we want to encrypt a message ourselves. The program uses a KEY_FILE with a length of 50000. The flag is 64 hex characters which mean it is 32 characters long. If we encrypt our own message we can use the result to reverse the original XOR. First we need make sure we use the same key to do this we will use Python to send two messages. Since the first 32 characters of the key were used to generate flag we will have to loop around through all 50000 characters in the file then send our own 32 character digest so that we can reverse the flag. The code to do this looks like this.
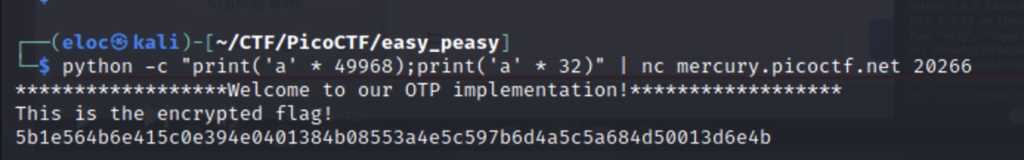
We are using the python command to write a one liner that we can pipe into the netcat command. Now let’s write a script to determine the flag.
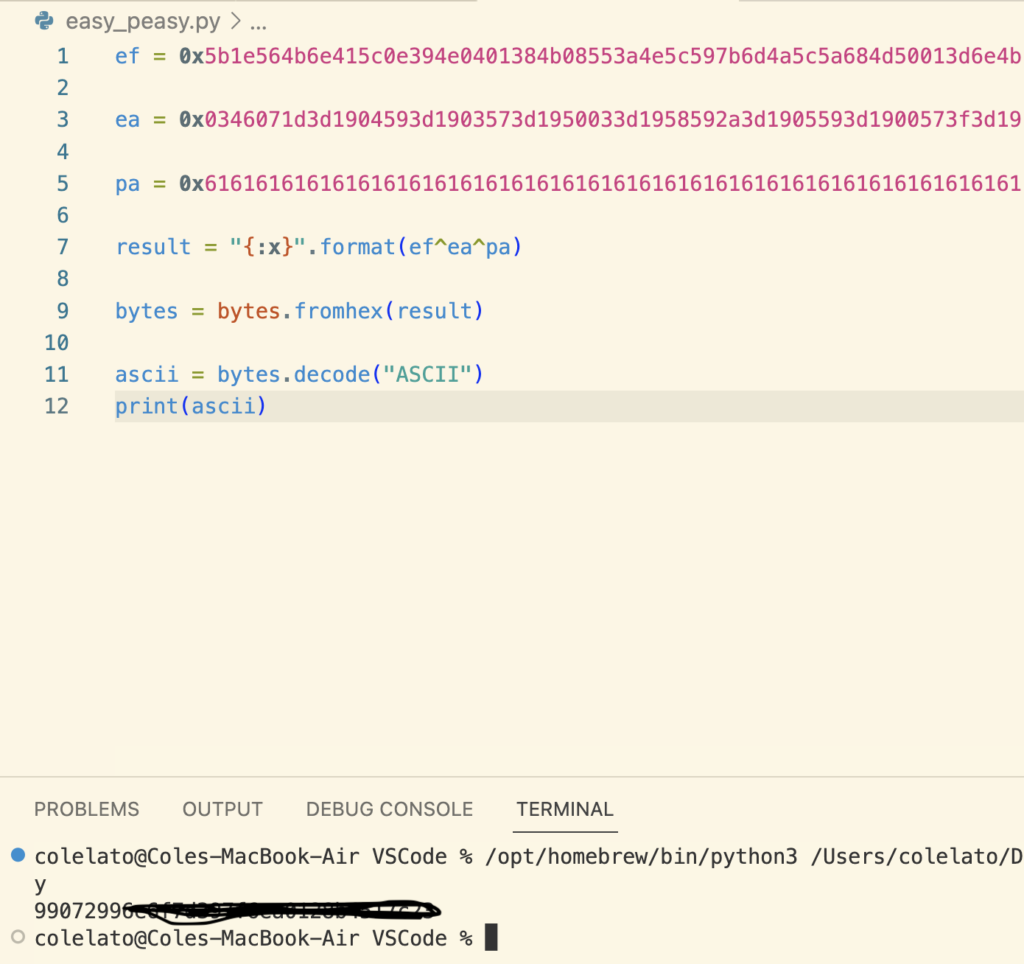
First we define three variables.
- ef – Our encrypted flag we got from the netcat command
- ea- The result of our 32 a’s we encrypted with the same key
- pa- This is the hex value of the a’s. So this is our plaintext
To reverse the function we perform this calculation
ef xor ea xor pa
This will return the flag in hex and the rest of the code is just translating it from hex to decimal.