Quick Intro
Over The Wire is a free website that offers many different “war games” to sharpen your skills in a CTF style format. Today we will start the game Bandit which is a beginner level room aimed at getting you familiar with the command line.
Connecting over SSH and Bandit0
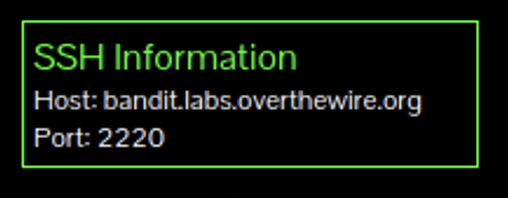
If you navigate to https://overthewire.org/wargames/bandit/ you’ll find this info in the top left. Next you open up a terminal and use the ssh command to connect.
The default port number for ssh is 22 so it’s very important you specify that we want to use port 2220, otherwise the connection won’t work.
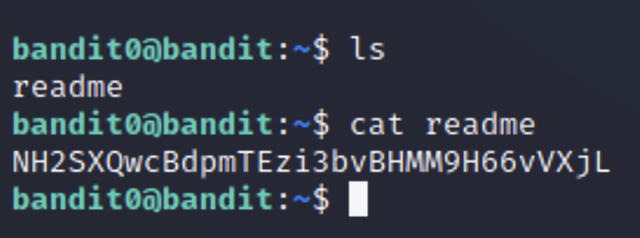
The first level is aimed at just learning how to navigate files in linux. The first command you need to be familiar with is ls. This command lists all the available folders in the current directory. Now we can see a file named readme, but how do we view the content of a file? For that we use the command cat. We type cat and the name of the file we want to see then the contents are printed out in the terminal and we have our password for the next level.
Bandit1
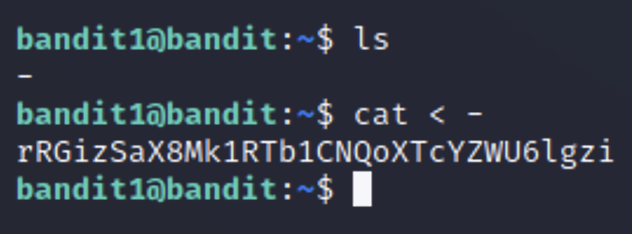
Level 1 is essentially the same process as level 0; however our file’s name is a special character and if you tried “cat -” you would receive an error message. One way to get around this is to use a “<” in front to tell cat to read the dash as a file name. You could also write out the entire path with “./-” (where “.” is a shortcut for full path of the current directory).
Bandit2
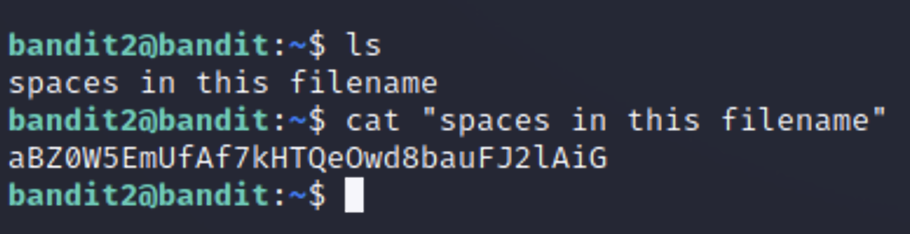
If our filename has spaces all we need to do is put the full name in quotes.
Bandit3
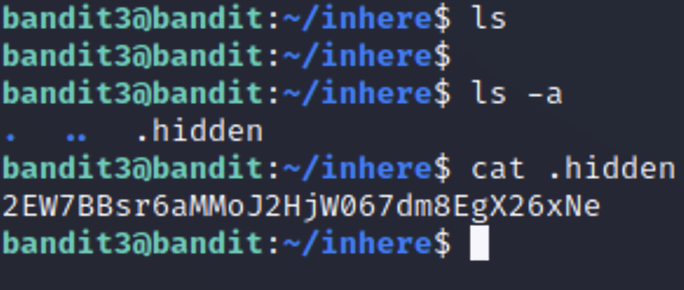
This time if you enter ls you’ll notice that nothing is returned in our terminal. This is because the file is hidden. To view all files in a directory, even hidden ones, we us the “-a” flag for “all”. The hidden file will have a period at the beginning of the name, which is what tells linux to hide it.
Bandit4
The next level comes with a little hint. There are multiple files in the directory and while we could cat each one individually that is not very efficient. One way we could find the correct file is with the file command.

The file command displays information about files. Most human readable letters will be listed as either ASCII or Unicode. The syntax for this command is “file file_name” but we don’t want to do this for every file as that doesn’t save much time and the files all have special characters in their names. To use the file command on an entire directory we can enter “file ./*”. Here is how it works
- file: Our command that displays info about the files
- ./: The period is shorthand for current working directory since all of the files we need to check are in the same place; this works nicely and it allows us to circumvent the special characters
- *: This is the wildcard symbol and it can be used with many different commands for pattern matching and searching. Since we need to check everything in the directory we can use it by itself to mean everything, but we could also use it with partial names like “-file*” to achieve the same goal.
Bandit5
For this level we need to find a file using multiple parameters. The best command for this is find, but the find command can get pretty complex as well as many other commands in Linux so how do we learn about it? A couples ways are
- typing “?” , “-h” , or “–help” after the command
- the man pages
- tldr: another command you can install to give brief explanations and examples by entering tldr [command]
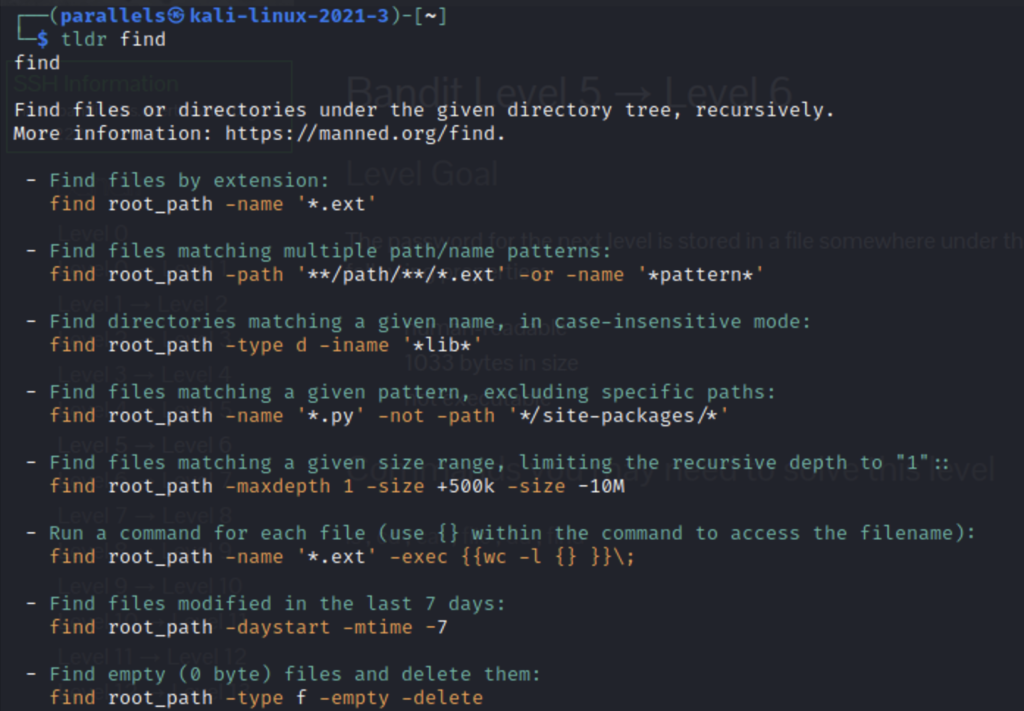
We see that the general syntax for the find command is
find [path] [parameters]
We can see an option for -size but we need more info so let’s check the man pages.
Tip” use the “/” key to search for key words
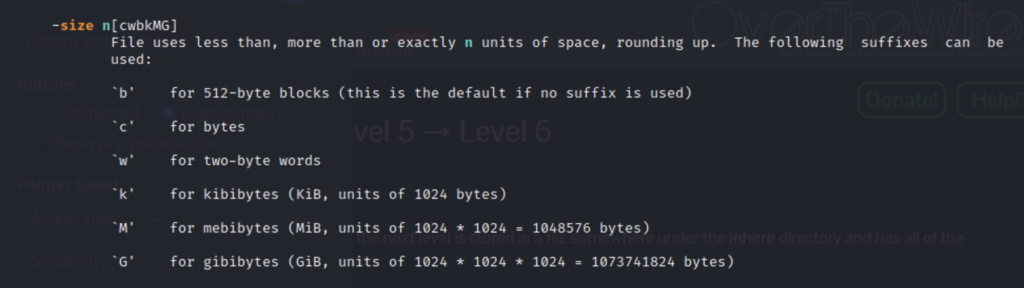
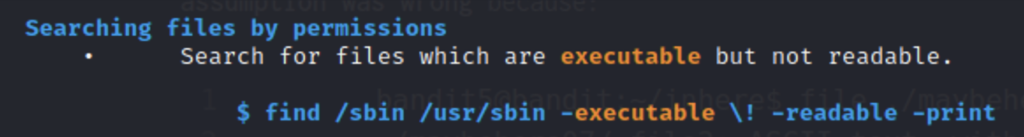
Now that we know the syntax and our parameters let’s try to find the files.
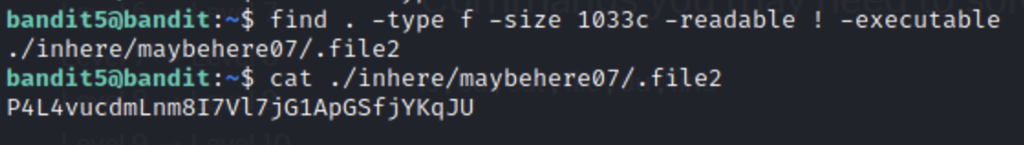
To search for something that is not executable we put a ! before -executable and then to see if the files were human readable we can use the – readable flag.
Bandit6
This level is very similar to the previous level but with different search parameters. So let’s go back to the man pages and look around for some useful flags.
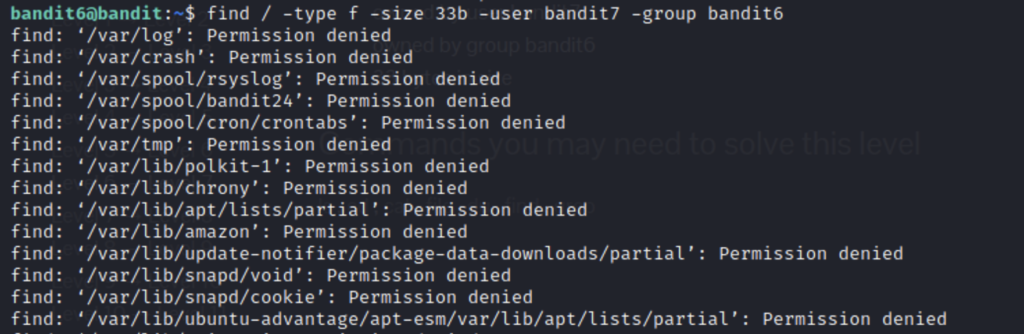
After finding all the matching parameters for our search and entering the command you might find your screen flooded with files you can’t access. No one wants to tediously read through all of that to find the one that they need so a good way to filter out all the bad results is 2>/dev/null.
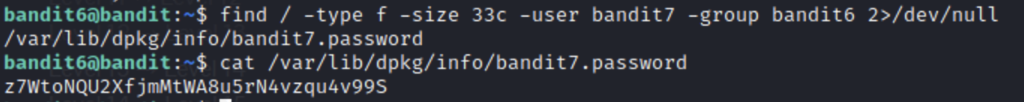
Bandit7
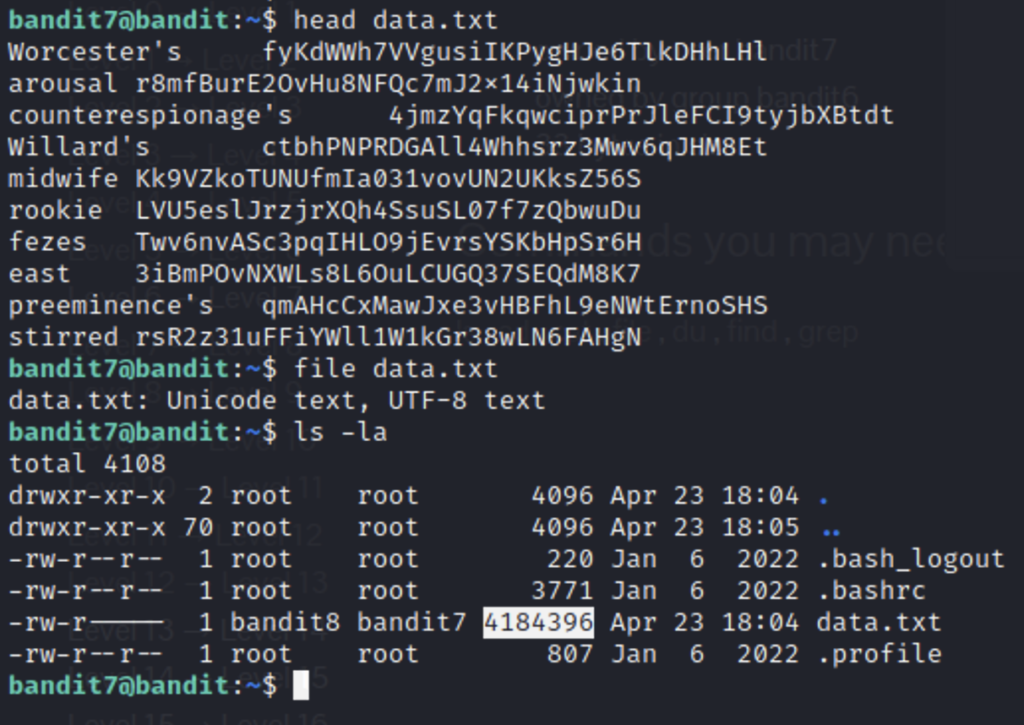
On this level we are given a file with dozens of passwords next to normal English words. The website tells us that the password we are looking for is next to the word “millionth”. A great tool for searching through text for patterns is grep. The syntax for grep is grep [pattern] [file].
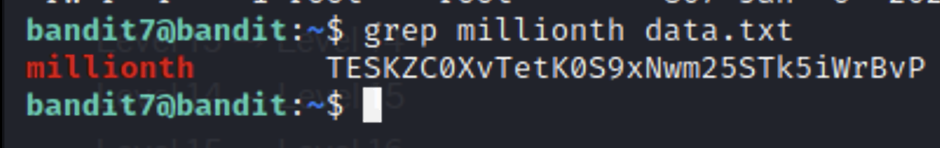
Bandit8
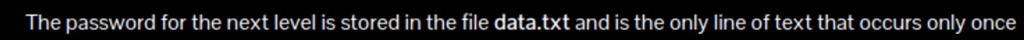
There are way too many lines to even try to do this manually so we’ll have to find some commands to help us. The two tools we will need for the this level are uniq and sort. You can pipe the commands from one command to another using a “|”.
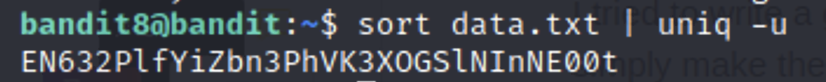
Sort organizes the data and then uniq compares it all and tells us what is unique. The -u flag only displays unique lines.
Bandit9

For this level we will need the strings a command and grep. The strings command sorts through the data and looks for printable strings for us. We can use the pipe feature and grep to sort through the strings it returns.
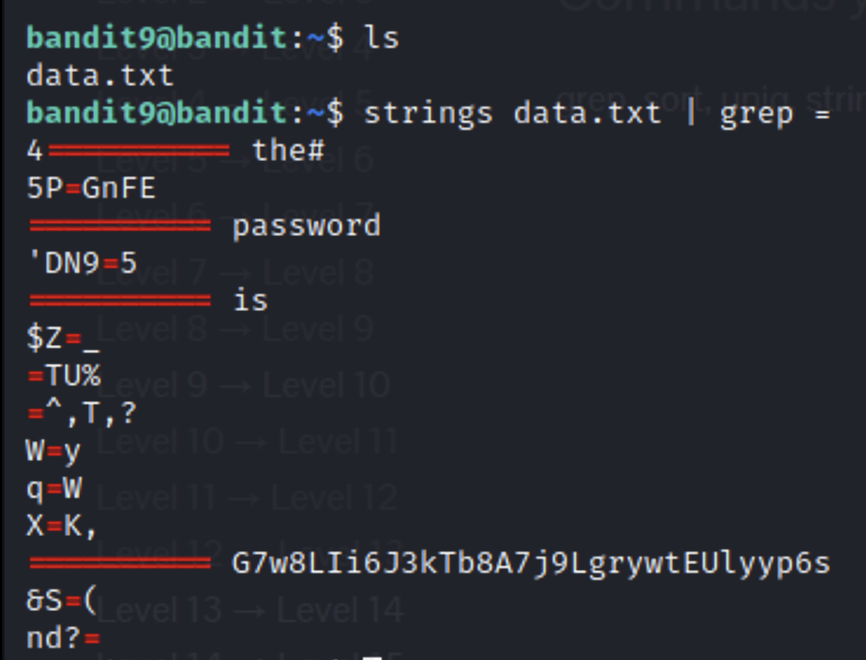
Bandit10
Base64 is a pretty well known encryption tool and can be used with the base64 command.
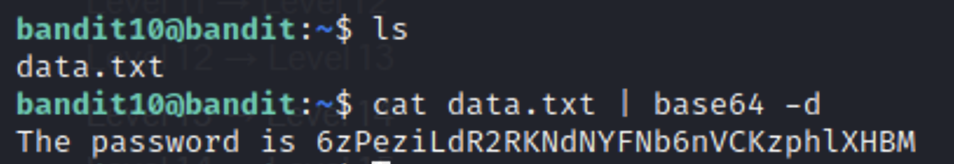
We cat the file then pipe the output to base64 using -d for decrypt.
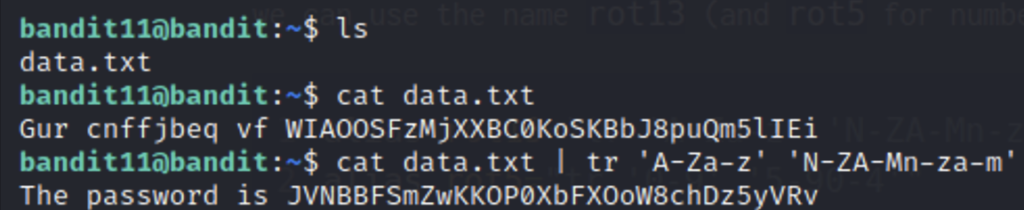
Bandit11
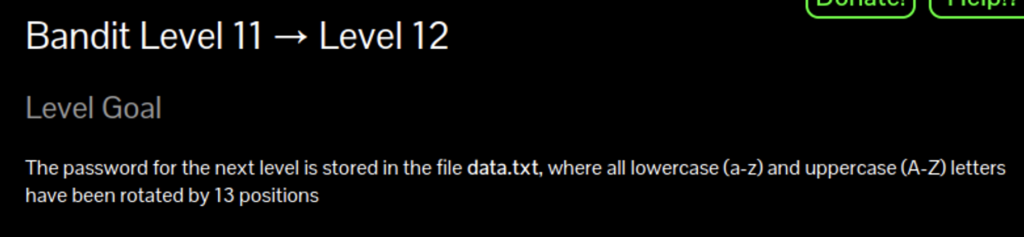
The encryption being described is rot13 or a Caesar Cipher. There are plenty of online tools for reversing rot13 but if you wanted to do it in the command line you would use the tr command which stands for translate
tr [old chars] [new chars]
Bandit12
First we’ll make a new directory in /tmp directory where we have write permissions. Here are the commands for that.
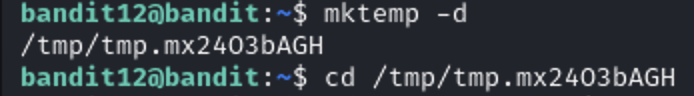
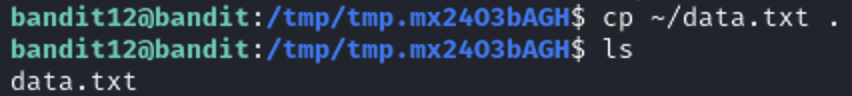
Now let’s look at the file and figure out what is going on
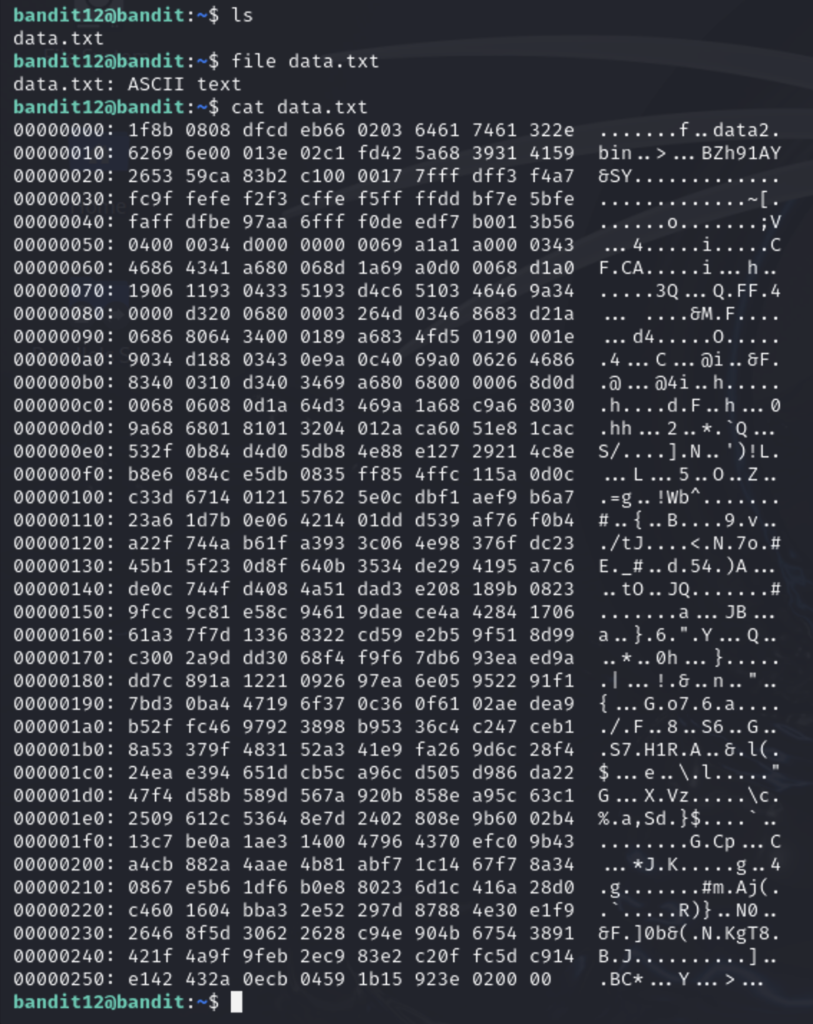
The file is a hexdump of binary file. We can tell from the top of the furthest right column that the previous name of this binary was “data2.bin”
A hexdump is a representation of a binary file that can be used for debugging and analysis. The binary data is represented in hexadecimal as well as ASCII text.
One tool used to create hexdumps of binaries is xxd and it can also revert a hexdump back into it’s original binary. Using the -r flag
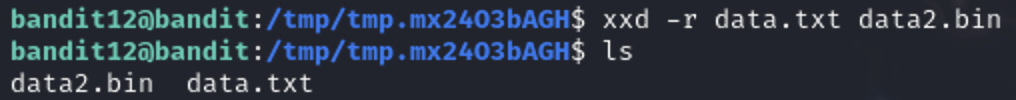
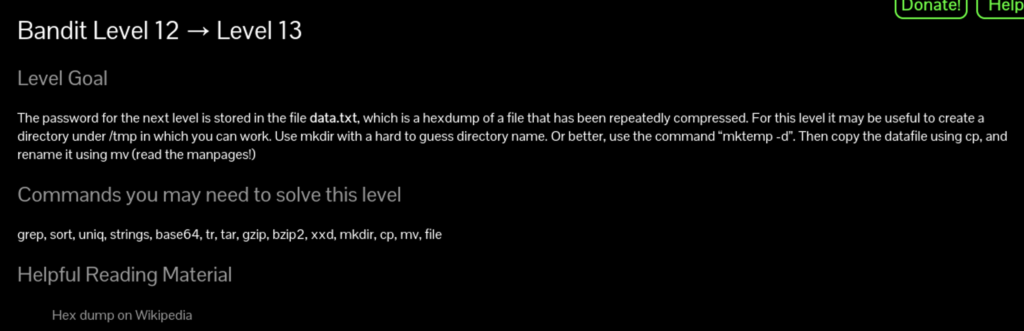
The file is a repeatedly compressed data file. To solve this puzzle we’ll have to know how to decompress various types of compressed files.
gzip -d [filename].gz -d for decompress
bzip2 -d [filename].bz2 -d for decompress
tar xf [filename].tar x for extract and f to denote filename
NOTE: in order to use the command the file will have to end with the appropriate extension so you will have to rename it first. This is very tedious, but after a bit of practice it becomes very easy.

Bandit13
After logging in we find the only file “sshkey.private”
SSH keys are used to securely log into to a computer over ssh without using a password. You keep telling encrypted key on your computer as a file and the use the -i [key] flag when executing ssh at the command line.