Natas is a war game geared towards getting you familiar with web hacking. If you’re new to hacking this is a great place to start as it covers the basics.
Natas0
Viewing the page source of a website is one of the critical recon steps when attacking a network. On this page you’ll view the raw html as well as the information about how the site is built and even developer comments. Once you view the source of this level the password will displayed for you
Natas1
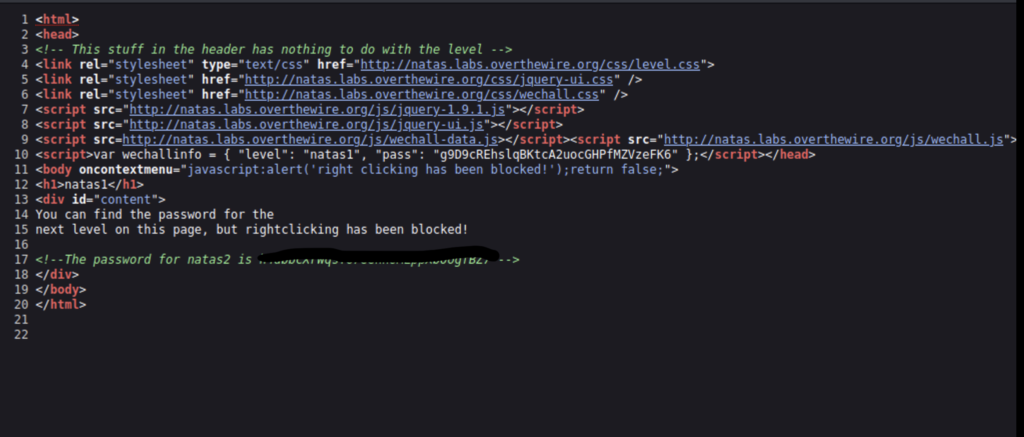
In the previous level we learned that you can right click to view the page source. You can also use the keyboard shortcut “ctrl + u” to view it
Natas2
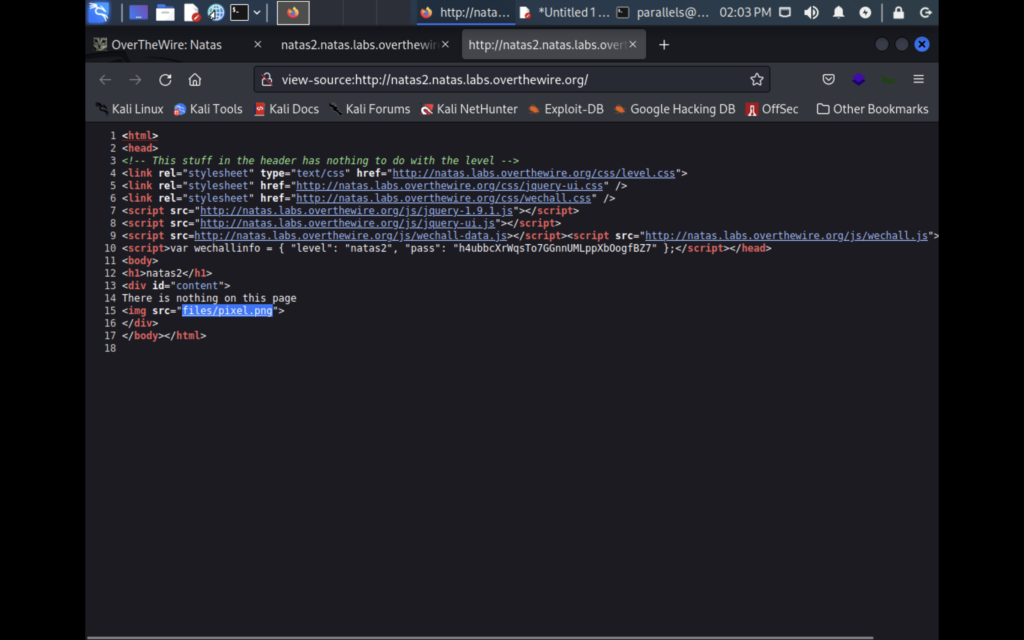
Looking at the source code for Natas2 we see that an image is being sourced from another file. You can go to this file by putting file location in the url.
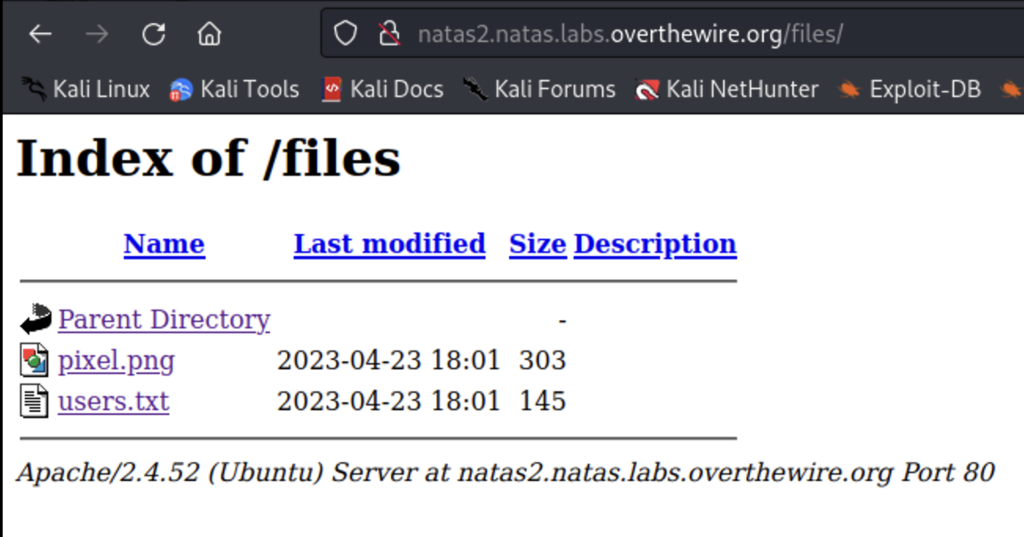
Once you look under users.txt you’ll find the password for the next level.
Natas3
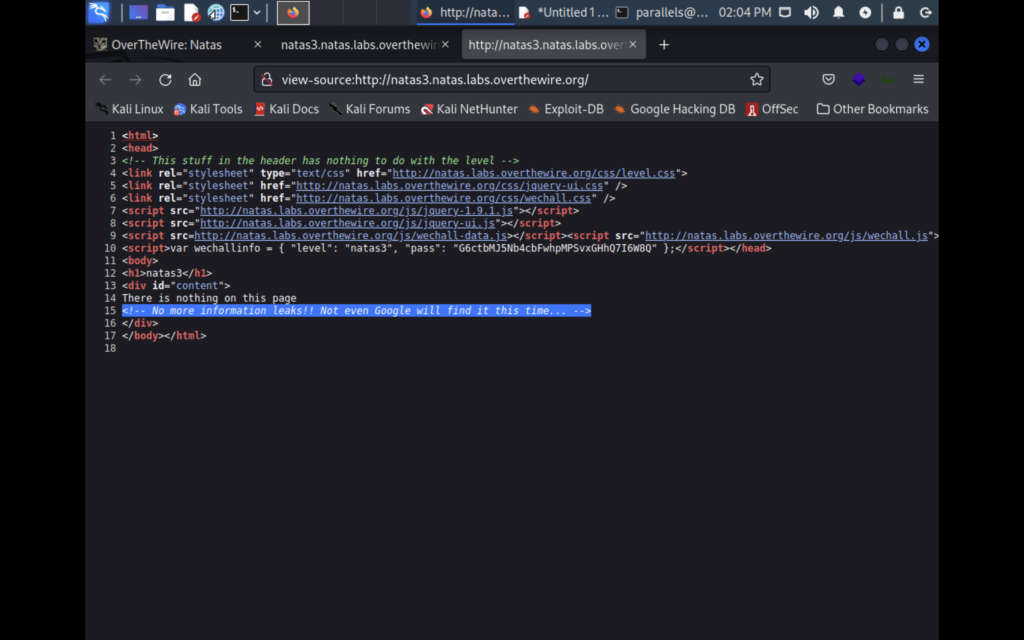
Looking at the source of the next level we find this comment. If you don’t know a little about web development this might seem like nothing but here is an oversimplified crash course of what you need to know for this level. Companies like Google send out web crawlers to document websites and index them in their search engines so that people can find these websites. But if you’re web developer you might not want all your web pages indexed by google because they may contain sensitive information. So what you can do is have a /robots.txt page on your website. Crawlers will visit these websites and know not to index any websites you have listed there. We can also see this page, so let’s check out the robots.txt.

We can see that there is a hidden page called /S3cr3t/ . Once you visit that page you’ll find the password.
Natas4

For this next level you’re going to need a proxy. I recommend installing the free tool BurpSuite. You can use proxy tools to intercept the http(s) request and edit in all sorts of ways. It’s required to be knowledgeable of proxies and how to use them to be a good hacker. Let’s intercept the request to this webpage.
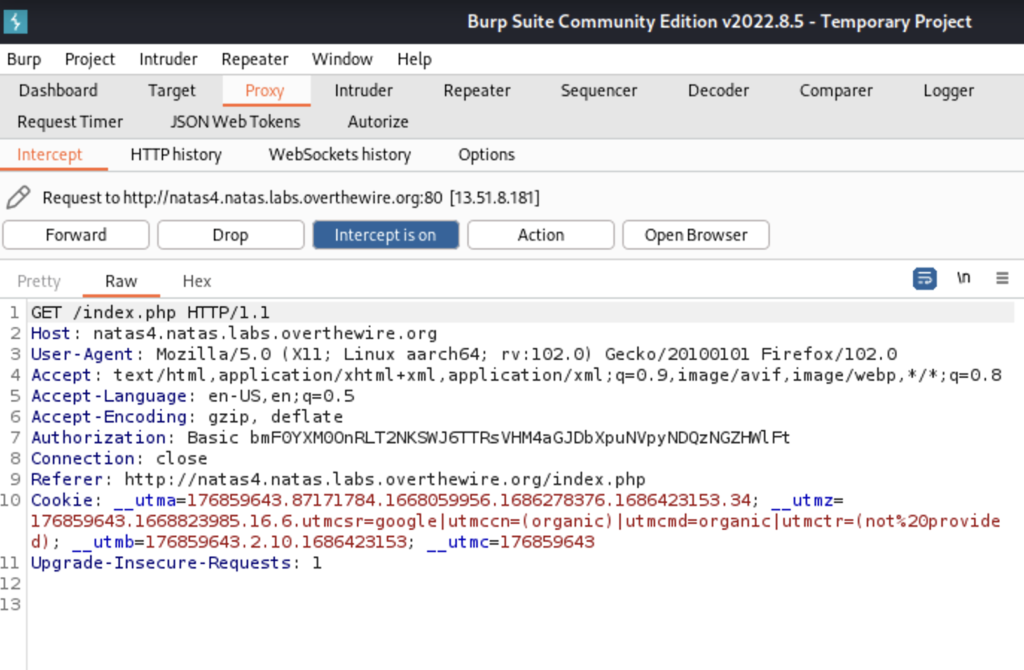
There’s a lot of information here but this part that pertains to this level is the referer. In the prompt to this level we were told that we couldn’t access the password because authorized users only come from a specific site. This site is called a referer. We can manually change the referer in the request then forward it through to the webpage.
Natas5
Let’s use Burp again to check out the request being sent.
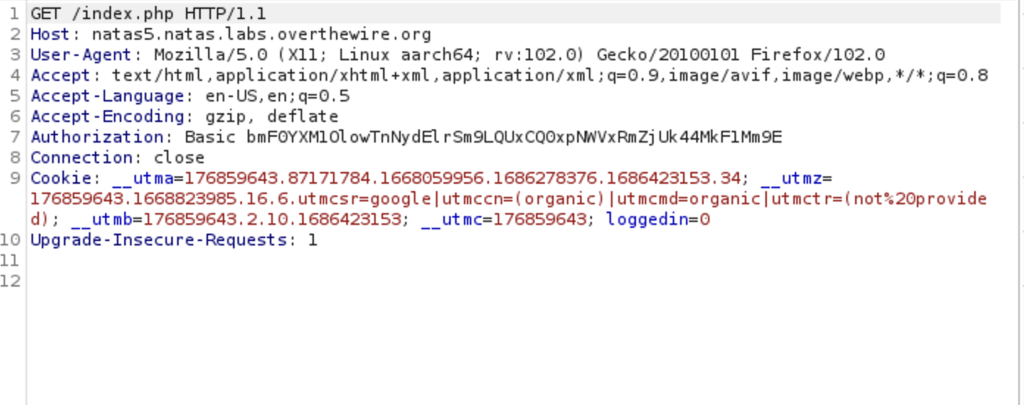
Just above line 10 we see loggedin=o . Let’s change that zero to a one and forward the request.
Natas6
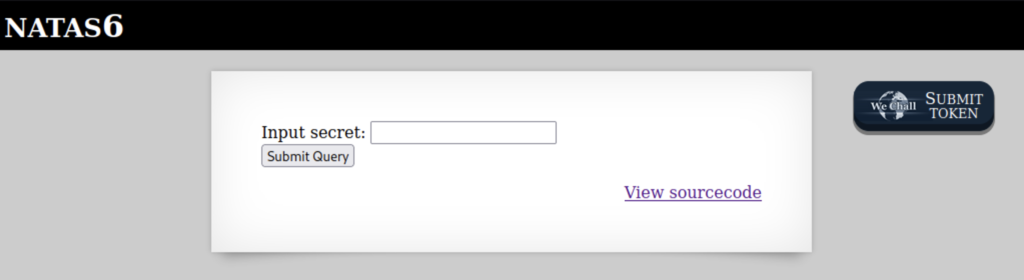
This level shows an input field where we need to put in the correct secret. There is also a tab to view the source code so let’s look at that.
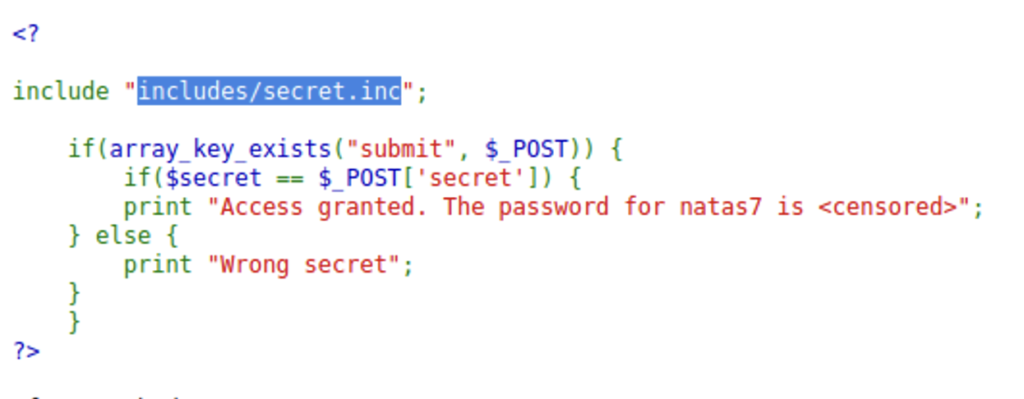
The PHP code basically says that once the correct secret is inputted the website will display the password, but it also includes what appears to be the file location to the secret so let’s go check that out.
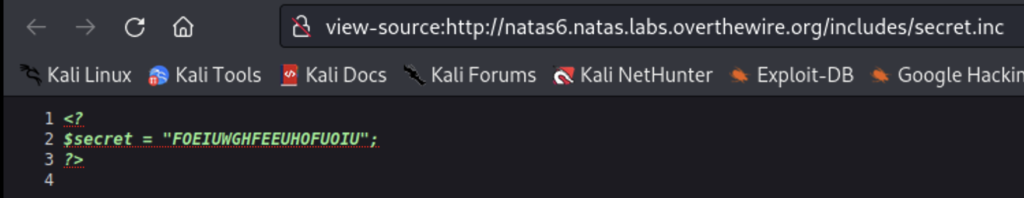
Now that we have our secret all we have to do is enter it to obtain the next password.
Natas7
his level at first just seems to have two hyper links for Home. and About. We can also see this change reflected in the url. Let’s look at the source code.
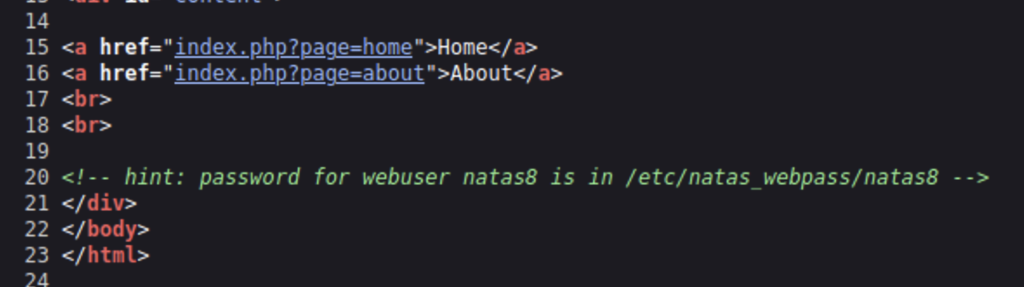
We have been given the file location for the next password. Going back to the webpage let’s try to enter in the file location in place of Home or About in the url.
Natas8
On Natas8 we see another input field for a secret, similar to the one we saw on Natas6. But this time the source code is different.
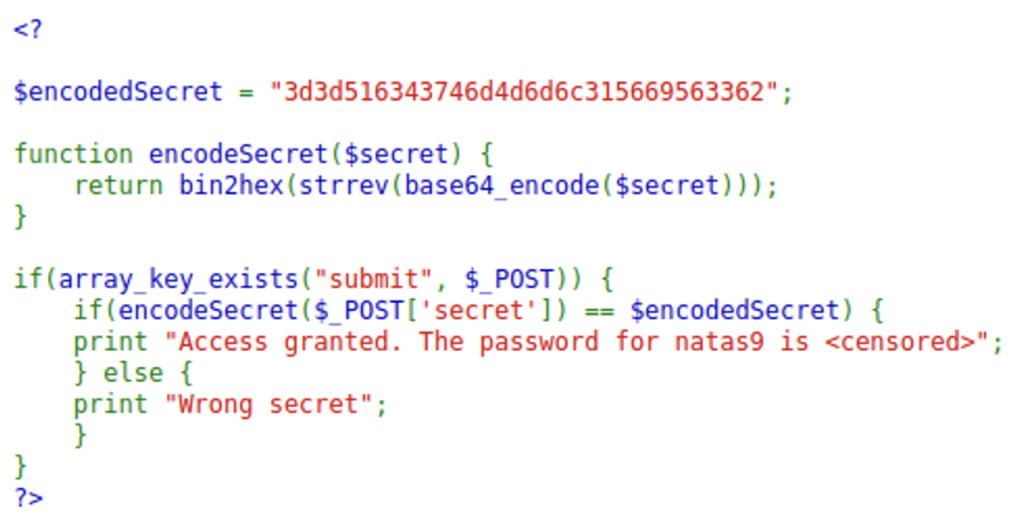
The secret has been encoded and stored on the webpage alongside the php code that describes how it was encoded. Meaning if we rewrite the code but backwards we will be able to determine what the secret originally was.
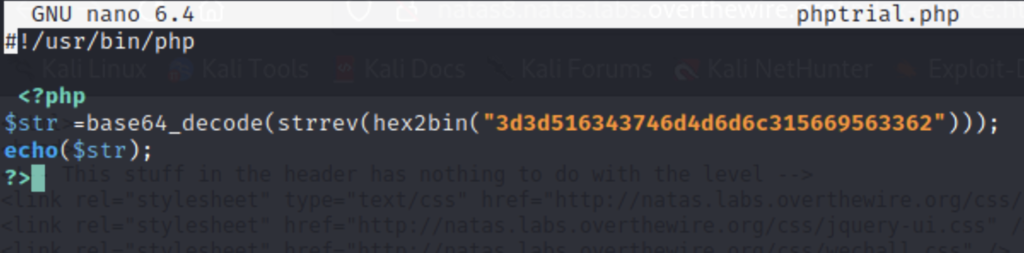
Once we have our secret we can submit it to obtain the password.
Natas9
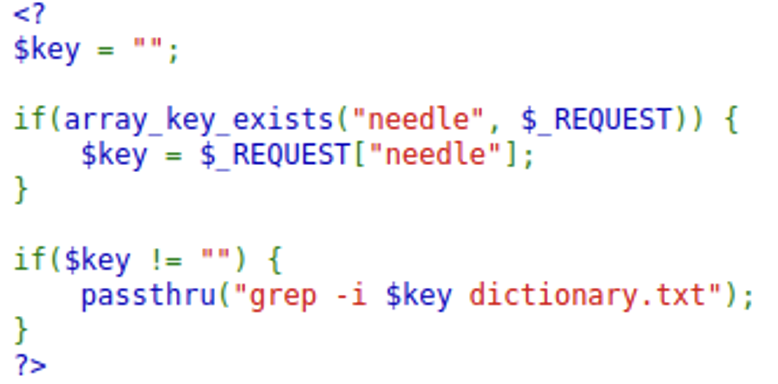
The source code for 9 shows us that this level works as a quick search for the dictionary. Where what we typed will be passed through to a command to search the dictionary. This command can also be viewed in the url.
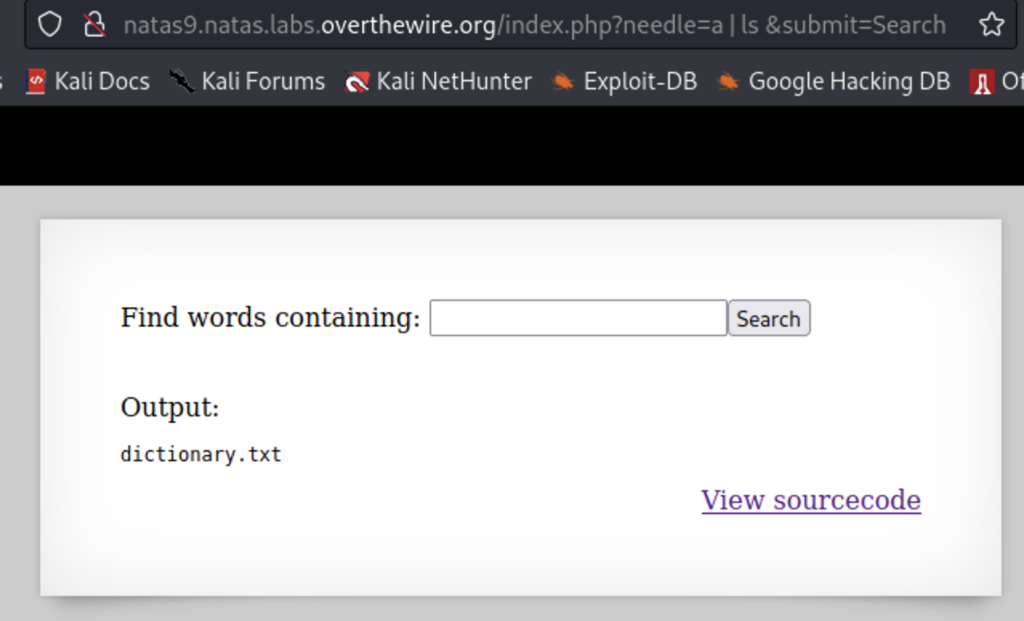
This exploit is called a command injection. A command injection is where you put own command into the website to have it executed for you. On this level we are using the “|” (pipe) to have our ls command executed. Which lists the content of the current directory. But how do we view the content of other directories? For that we’ll have to execute a directory traversal attack. Since this website is running on a linux server as we’ve seen in the previous levels we can use the linux cli syntax “../../../” to move up through the file system and the use the cat command to view this files.
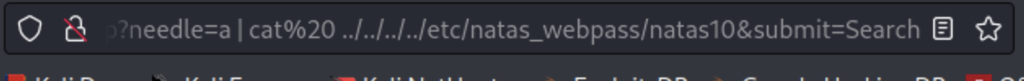
However you might remember from previous levels we already know where the passwords are kept and if we type out the full path of “/etc/natas_webpass/natas10” we won’t need to wander around the file system but it’s good practice as you may use that technique in the future.
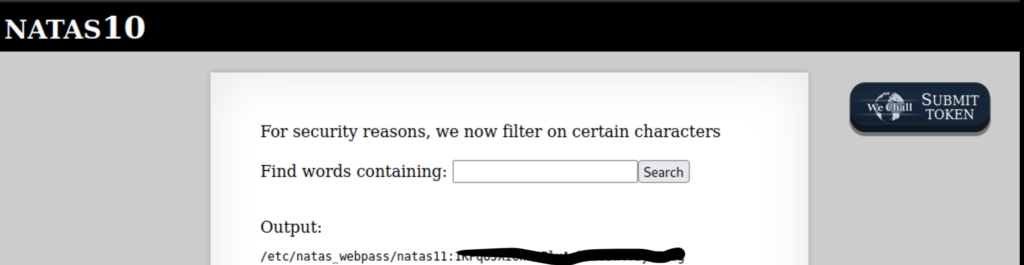
Natas10

This level is essentially the same as the last level except with filter to prevent the same attack.
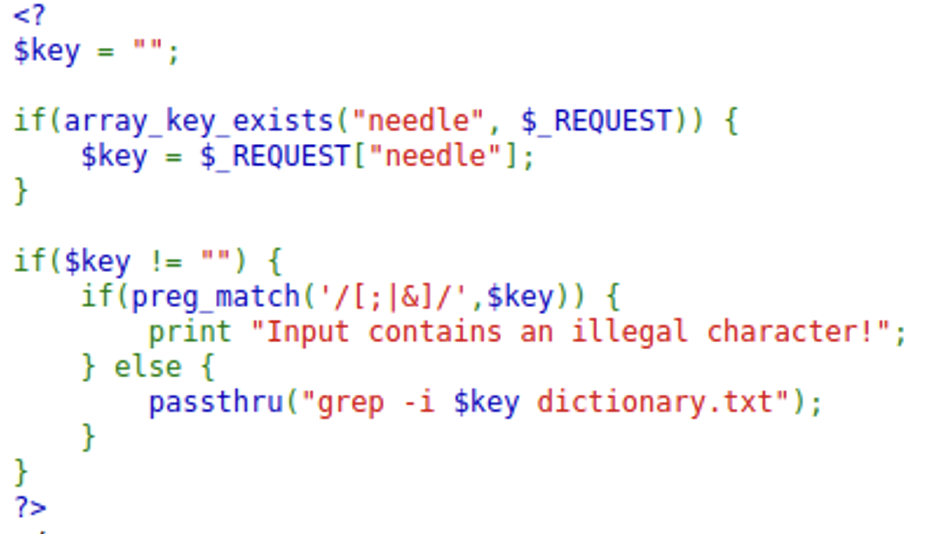
However the grep section from the previous level is still the same.
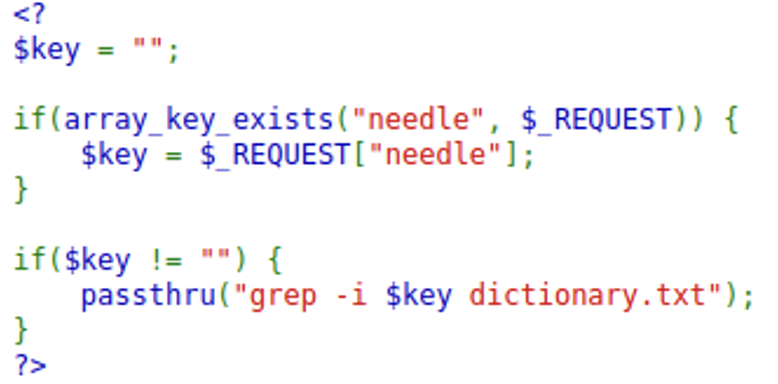
grep is a cli tool used for matching text patterns. The basic syntax is “grep [pattern] [file_to_search] (the “-i” is flag that tells grep to not be sensitive to case). Our input comes in right before the file to search parameter so we can enter our own file to search and we already know what file to search in.