This is a simple web hacking room that serves as a good intro to IDOR vulnerabilities
What is an IDOR?
IDOR stands for “Insecure Direct Object Reference”. In simple terms an IDOR is a vulnerability where a website uses user supplied input to access internal objects directly. It is one of the most common web app vulnerabilities. The best way to learn about them is to dive in.
Getting The Flag
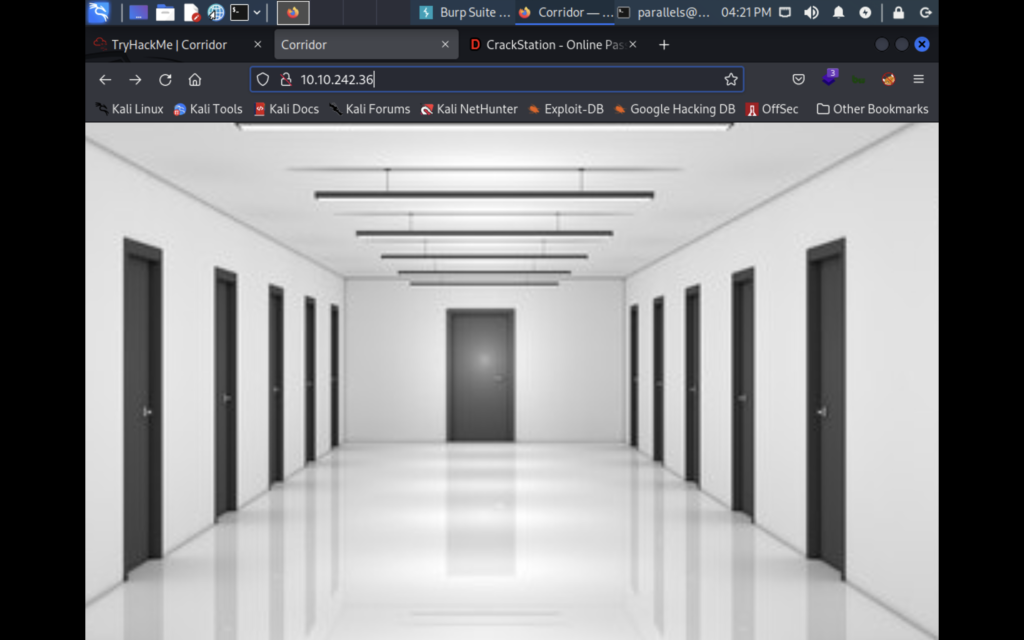
When you visit the site you’re greeted with this image that allows you change your perspective and click on doors. After clicking around for a while you’ll notice that all the doors just point to empty rooms.
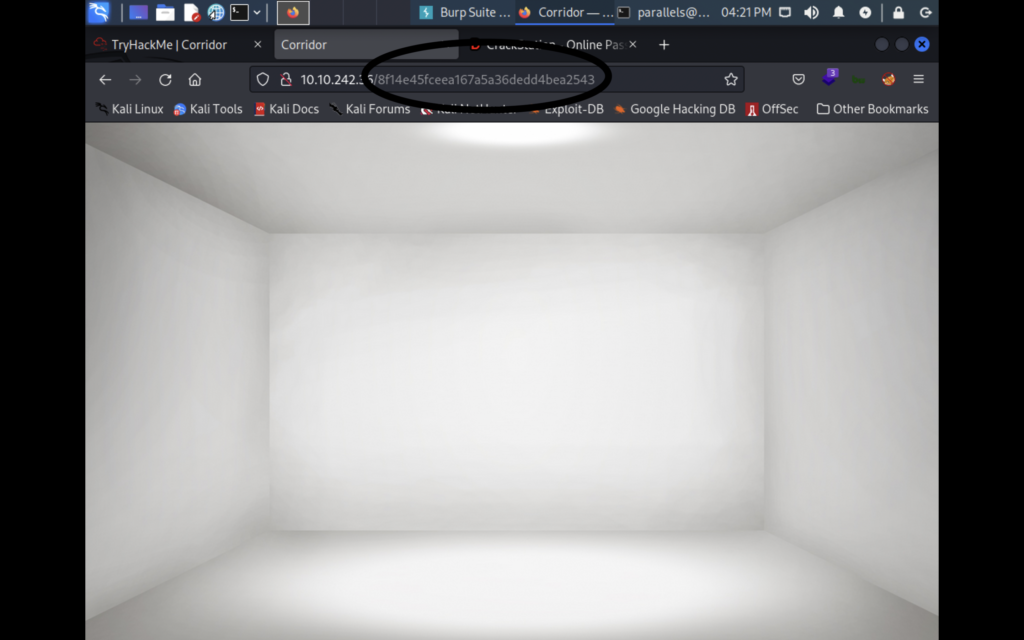
If you look at the url though you’ll notice that every room has a different string of gibberish added to it whenever you click a door. This seems like a hash so let’s try to crack it using crackstation.net.
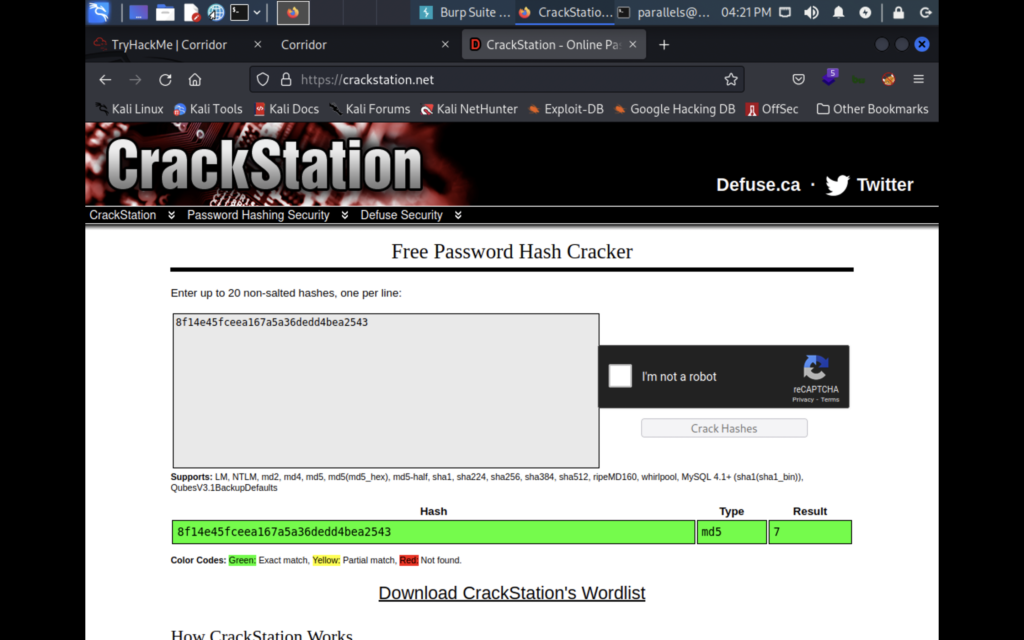
It comes back as an MD5 hash and the original digest was 7. Let’s crack the other rooms to see if there is a pattern. Checking all of the rooms individually is tedious, but if you view the source code of the corridor you’ll find them all listed.
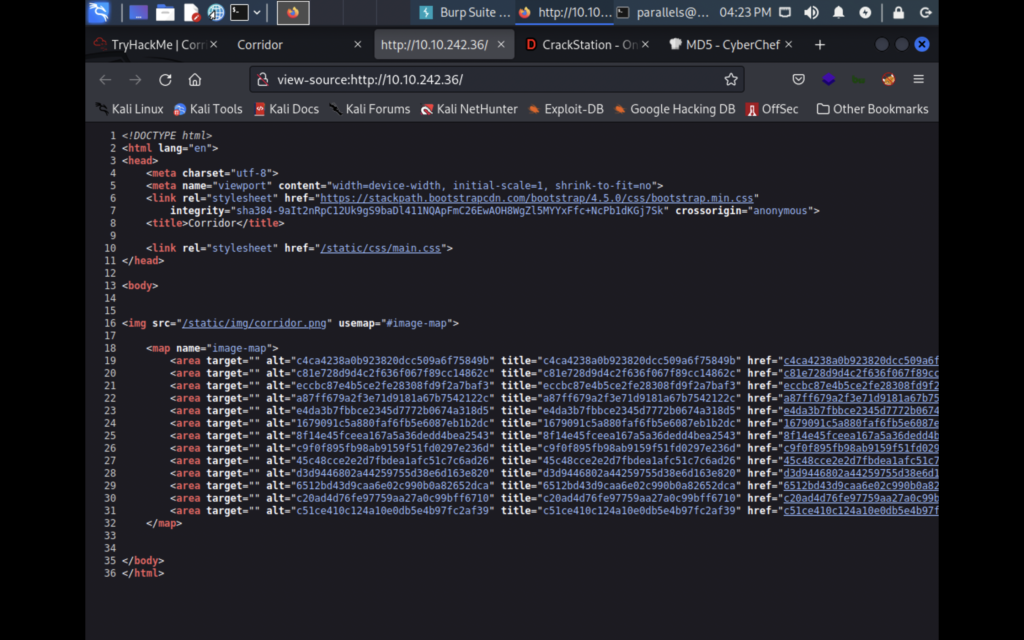
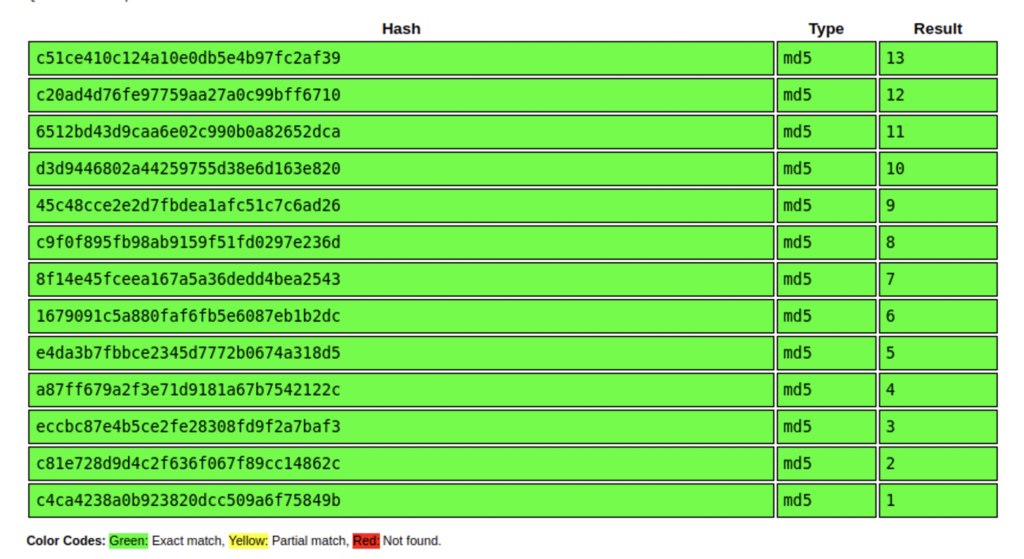
They all come back as numbers 1 through 13. So the rooms are numbered, but if you count the doors you’ll find that there are 14. Where is the missing door. Let’s generate our own hashes and put them in the URL. I used https://gchq.github.io/CyberChef/ to cook up some hashes. At first I tried 14 but that returned a 404 error. One of the first things I learned about IDORs was that whenever you see a number in the url or http request switch that to 0 to see what that does to an application. So In tried 0.
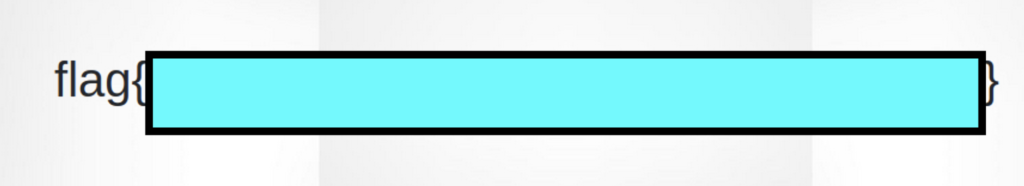
Which returned the flag. If you’re having trouble generating the hash make sure you’re using the MD5 algorithm and be careful of pressing space or enter as that will change the hash.