Today we will do a walk through of Pickle Rick room on TryHackMe.com. This is an easy room that teaches basic web recon and linux command line skills.
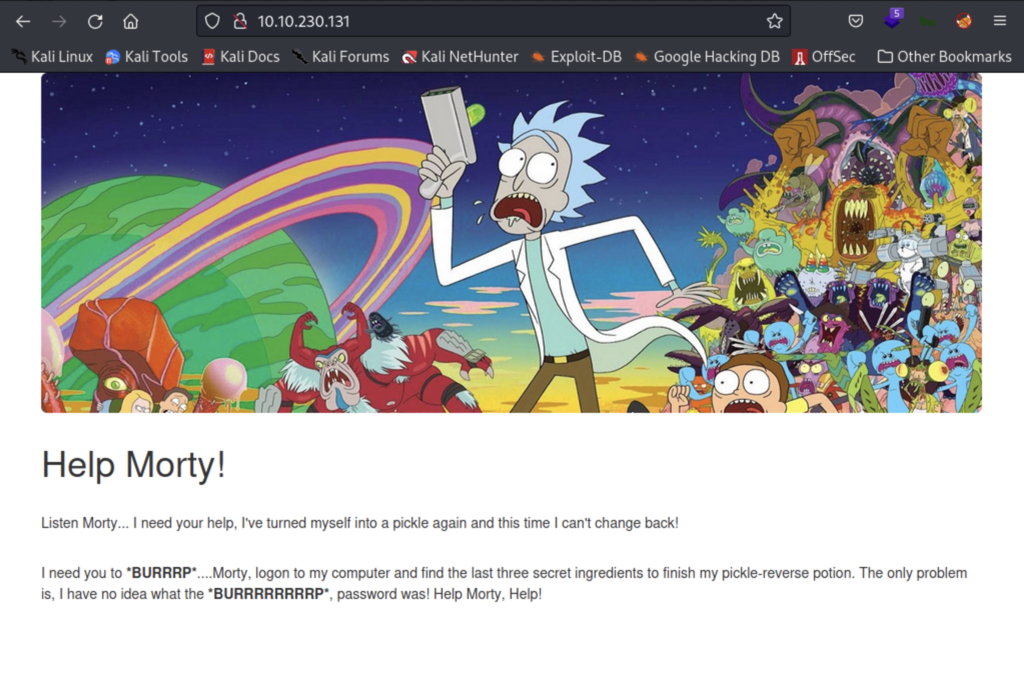
The IP address takes us to this webpage. I launch gobuster and while that runs in the background I do some manual enumeration of the site. If you view the source page for this site you’ll find a username in an html comment.

We still need to find a password and we’re not sure where to even try the username. Our nmap reveals the only services running are ssh and http so let’s keep looking. Next I tried robots.txt.
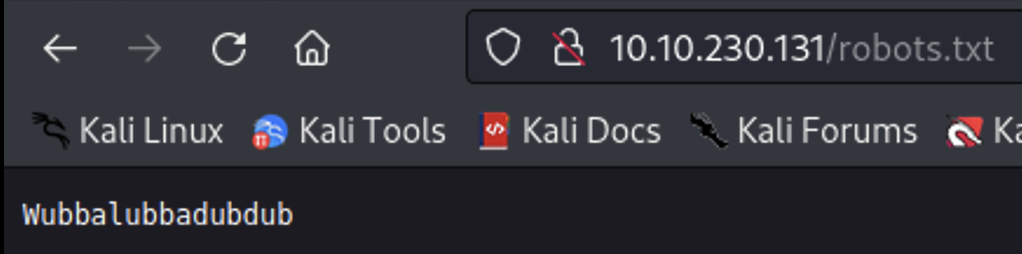
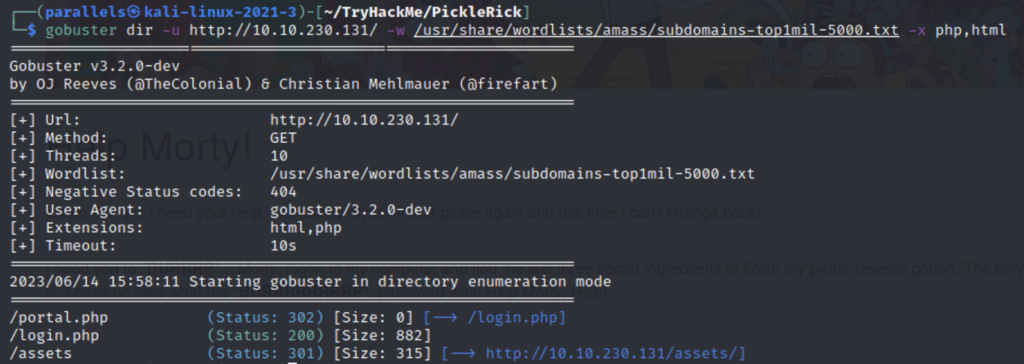
This is a catch phrase from the show, it may be a password. My initial gobuster didn’t return anything of interest so I tried a second one but this time looking for the php file extension using ” -x php”.
Let’s go try what we found so far on the login page.

The login works and we’re allowed into the site however we can only access the page that acts as a terminal.

After using the terminal emulator for a bit I find a file that looks interesting but when I try to view the file using cat I get this message in return. A few other commands like nano and vim also return the same error. But I am able to view the file using grep.
grep . [filename]
grep- look through the file for any matching patterns
. – works as a wildcard for grep which then returns the whole file
Our first ingredient
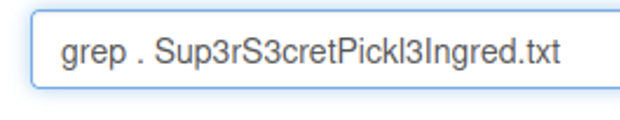
I also find a clue telling us to look around the file system for more ingredients(flags). cd does not work but you can use ls to view the contents of other directories like so
ls ../../
the ../ moves up one directory then lists the contents of that directory. Once I find a directory I want to check I add that to the end to navigate like so.
ls ../../../home
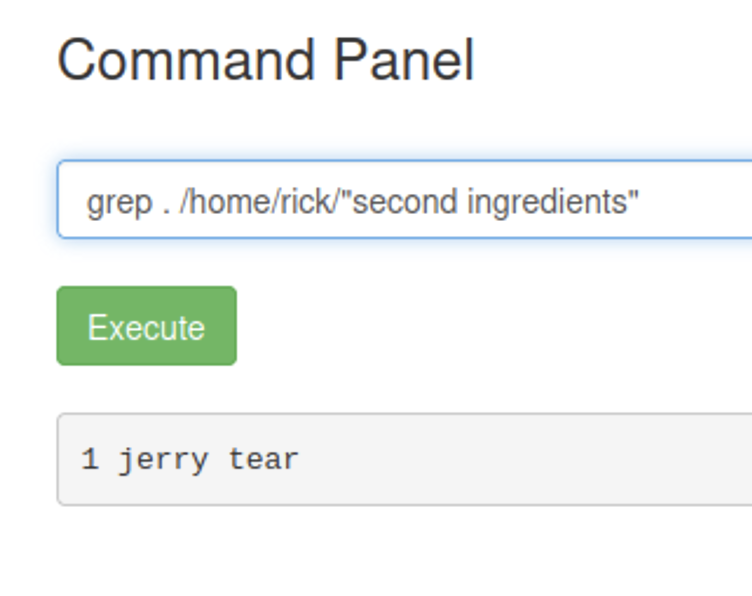
After doing this for a while I find a folder named “second ingredient” under /home/rick and we can use the same grep workaround from before.
I have a feeling that our last flag is in the root directory but we are currently the user www-data and do not have permission. I check our sudo privileges with “sudo -l”.
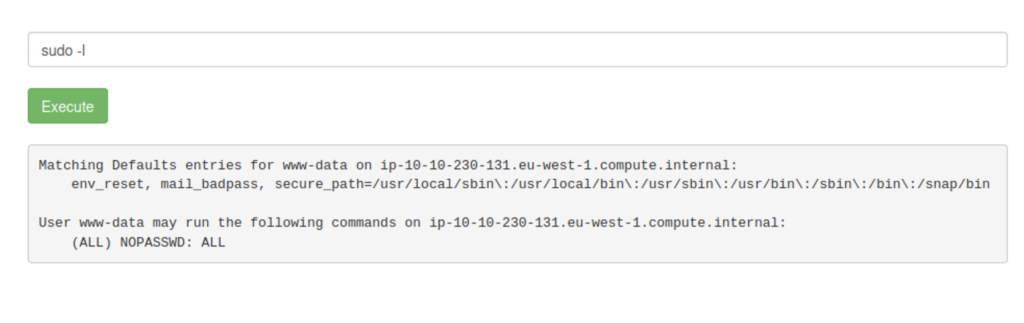
We have permission to run any command as sudo with no password so just like before but this time with sudo.
